http://open-source-security-software.net/project/MISP/news.atomRecent news for MISP2024-11-15T12:33:47.140768+00:00python-feedgenhttps://www.misp-project.org/research-topics/MISP - MISP, research topics2023-10-14T20:58:02.060969+00:00MISP Research topics Exploring New Horizons in Cyber security and threat intelligence with MISP: Research Opportunities
Welcome to the MISP Research Initiative!2023-10-14T20:58:02.060969+00:00https://www.misp-project.org/2023/07/31/MISP.2.4.174.released.html/MISP - MISP 2.4.174 released with major workflow enhancements, new features and fixes2023-07-31T01:00:00+00:00We are thrilled to announce the immediate availability of MISP v2.4.174 with significant workflow improvements, accompanied by a host of quality-of-life enhancements and bug fixes.2023-07-31T01:00:00+00:00https://www.misp-project.org/2023/08/23/MISP_now_supports_Signal_Metadata_Format_Specification_SigMF.html/MISP - MISP now supports Signal Metadata Format Specification SigMF2023-08-23T01:00:00+00:00As one of the outcomes of GeekWeek8, MISP now supports a new set of features useful for handling radio frequency information in the Signal Metadata Format Specification) (SigMF), commonly used in Software Defined Radio (SDR), digital signal processing and data analysis applications.2023-08-23T01:00:00+00:00https://www.misp-project.org/2023/08/24/MISP.2.4.175.released.html/MISP - MISP 2.4.175 released with various bugs fixed, improvements and security fixes.2023-08-24T01:00:00+00:00MISP 2.4.175 released with various bugs fixed, improvements and security fixes.
Improvements Added support of start_date and end_date options in the MISP dashboard widgets.2023-08-24T01:00:00+00:00https://www.misp-project.org/2023/08/26/MISP-Sentinel-UploadIndicatorsAPI.html/MISP - MISP to Microsoft Sentinel integration with Upload Indicators API2023-08-26T01:00:00+00:00MISP to Microsoft Sentinel integration Introduction The MISP to Microsoft Sentinel integration allows you to upload indicators from MISP to Microsoft Sentinel.2023-08-26T01:00:00+00:00https://www.misp-project.org/2023/09/15/MISP.2.4.176.html/MISP - MISP 2.4.176 released with various improvements and bugs fixed.2023-09-15T01:00:00+00:00MISP 2.4.176 released with various improvements and bugs fixed. This version also includes major improvements in the misp-stix library especially on the storing relationships and the description of relationships in the MISP standard format.2023-09-15T01:00:00+00:00https://www.misp-project.org/2023/09/27/MISP.2.4.177.released.html/MISP - MISP 2.4.177 released with various improvements and bugs fixed.2023-09-27T01:00:00+00:00MISP 2.4.177 released with various bugs fixed and improvements.
Improvements [dev] added a shell script to generate the restsearch parameters. [CLI] add command to expire active AuthKeys that do not have an IP allowlist set.2023-09-27T01:00:00+00:00https://www.misp-project.org/2023/07/11/MISP.2.4.173.released.html/MISP - MISP 2.4.173 released with various bugfixes and improvements2023-07-11T01:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.173 with a new password reset feature, along with a host of quality of life improvements and fixes.2023-07-11T01:00:00+00:00https://www.misp-project.org/2023/06/13/MISP.2.4.172.released.html/MISP - MISP 2.4.172 released with new TOTP/HTOP authentication, many improvements and bugs fixed2023-06-13T01:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.172 with new TOTP/HTOP authentication, many improvements and bugs fixed.2023-06-13T01:00:00+00:00https://www.misp-project.org/2023/05/18/MISP.2.4.171.released.html/MISP - MISP 2.4.171 released with a long list of fixes, a dashboard rework, STIX 2.1 improvements and more2023-05-18T01:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.171 with a long list of fixes, major STIX 2 improvements and an overhaul over the dashboard widget toolkit.2023-05-18T01:00:00+00:00https://www.misp-project.org/2023/04/29/MISP.how.to.push.to.a.taxii.server.html/MISP - How to push to a TAXII server from MISP2023-04-29T01:00:00+00:00If you want to push data from your MISP instance to a TAXII server, there are a few steps you need to follow.2023-04-29T01:00:00+00:00https://www.misp-project.org/thanks/MISP - MISP, Sponsoring - Thanks Page2023-04-15T04:00:05.230896+00:00Thank you! The MISP project owes its existence and continuous improvement to the invaluable support of numerous organizations and individuals. We are deeply grateful to the following organizations, whose ongoing contributions have helped us enhance the project and ensure its long-term sustainability.2023-04-15T04:00:05.230896+00:00https://www.misp-project.org/2023/04/13/MISP.2.4.170.released.html/MISP - MISP 2.4.170 released with new features, workflow improvements and bugs fixed2023-04-13T01:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.170 with new features, workflow improvements and bugs fixed.
It includes many improvement release of misp-stix, the core Python library for importing and exporting STIX (1, 2.2023-04-13T01:00:00+00:00https://www.misp-project.org/2023/04/03/MISP-Sentinel.html/MISP - MISP to Azure Sentinel integration2023-04-03T01:00:00+00:00MISP to Azure Sentinel integration Introduction The MISP to Azure / Sentinel integration allows you to upload indicators from MISP to Microsoft Sentinel.2023-04-03T01:00:00+00:00https://www.misp-project.org/2023/03/14/MISP.2.4.169.released.html/MISP - MISP 2.4.169 released with various improvements and bug fixes.2023-03-14T00:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.169 with various improvements and bug fixes.
It includes many improvement release of misp-stix, the core Python library for importing and exporting STIX (1, 2.2023-03-14T00:00:00+00:00https://www.misp-project.org/2023/02/23/MISP-fail2ban-integration.html/MISP - MISP and fail2ban2023-02-23T00:00:00+00:00fail2ban - MISP fail2ban is known to do a great job at giving attackers a hard time when they try to “test” passwords or enumerate users of a service.2023-02-23T00:00:00+00:00https://www.misp-project.org/2023/02/20/Critical_SQL_Injection_Vulnerabilities_Fixed.html/MISP - Critical SQL injection vulnerabilities in MISP (fixed in v2.4.166 and v2.4.167)2023-02-20T00:00:00+00:00Critical SQL injection vulnerabilities in MISP (fixed in v2.4.166 and v2.4.167) Introduction As of the past 2 months, we’ve received two separate reports of two unrelated SQLi vector vulnerabilities in MISP that can lead to any authenticated user being able to execute arbitrary SQL queries in MISP.2023-02-20T00:00:00+00:00https://www.misp-project.org/2023/02/16/MISP.2.4.168.released.html/MISP - MISP 2.4.168 released with bugs fixed, security fixes and major improvements in STIX support.2023-02-16T00:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.168 with bugs fixed and various security fixes.
It includes a rather substantial release of misp-stix, the core Python library for importing and exporting STIX (1, 2.2023-02-16T00:00:00+00:00https://www.misp-project.org/2022/12/26/MISP.2.4.167.released.html/MISP - MISP 2.4.167 released with many improvements, bugs fixed and security fixes.2022-12-26T00:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.167 with new features and fixes, bugs fixed and a security fix.2022-12-26T00:00:00+00:00https://www.misp-project.org/2022/12/15/Video_MISP_Workflow.html/MISP - Training Video - MISP Workflow2022-12-15T00:00:00+00:00MISP Training Video December Edition - Workflow MISP has been a widely used open source CTI platform for the past decade, with a long list of tools that allow users to customise the data models and contextualisation of the platform, yet true customisation of the actual workflows and processes had to be done externally using custom scripts.2022-12-15T00:00:00+00:00https://www.misp-project.org/2022/12/15/Video_MISP_Best_practices_for_encoding_threat_intelligence.html/MISP - Training Video - MISP Best Practices for Encoding Threat Intelligence2022-12-15T00:00:00+00:00MISP Training Video December Edition - Best Practices for Encoding Threat Intelligence and Leveraging the information in MISP to Make Threat Landscape Report Content of Training Session MISP data model introduction Best practices - from evidences to actionable evidences Leveraging the information in MISP to Make Threat Landscape Report Jupyter notebook used during the training session.2022-12-15T00:00:00+00:00https://www.misp-project.org/2022/11/30/MISP.2.4.166.released.html/MISP - MISP 2.4.166 released with many improvements, bugs fixed and security fixes.2022-11-30T00:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.166 with new features and fixes, including two critical security fixes.2022-11-30T00:00:00+00:00https://www.misp-project.org/2022/11/21/MISP.2.4.165.released.html/MISP - MISP 2.4.165 released with many improvements, bugs fixed and security fixes.2022-11-21T00:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.165 with many improvements in workflows but also performance improvements.2022-11-21T00:00:00+00:00https://www.misp-project.org/2022/11/14/curation-with-org-confidence-level.html/MISP - Curate events with an organisation confidence level2022-11-14T00:00:00+00:00Quality of threat intelligence When you receive threat intelligence from different sources you quickly realise there is a big difference in the quality of the received information.2022-11-14T00:00:00+00:00https://www.misp-project.org/2022/10/27/SACTI_Secure_aggregation_of_cyber_threat_intelligence.html/MISP - SACTI - Secure aggregation of cyber threat intelligence2022-10-27T01:00:00+00:00SACTI: Secure aggregation of cyber threat intelligence Overview Communities can share cyber threat intelligence on platforms, such as MISP. In the H2020 project Prometheus TNO has developed a way to securely aggregate cyber threat intelligence and publish the result on MISP.2022-10-27T01:00:00+00:00https://www.misp-project.org/2022/10/10/MISP.2.4.164.released.html/MISP - MISP 2.4.164 released with new tag relationship feature, improvements and a security fix2022-10-10T01:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.164 with a new tag relationship features, many improvements and a security fix.2022-10-10T01:00:00+00:00https://www.misp-project.org/2022/09/26/MISP.2.4.163.released.html/MISP - MISP 2.4.163 released with improved periodic notification system and many improvements2022-09-26T01:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.163 with an updated periodic notification system and many improvements.2022-09-26T01:00:00+00:00https://www.misp-project.org/2022/09/12/2022-09-12_periodic_notifications.html/MISP - Periodic summaries - Visualize summaries of MISP data2022-09-12T01:00:00+00:00Periodic summaries - Visualize summaries of MISP data As of version 2.4.162, MISP includes a periodic summary feature allowing users to consult a summary based on a requested time-frame for data the user has access to.2022-09-12T01:00:00+00:00https://www.misp-project.org/2022/09/13/misp-guard.html/MISP - MISP Guard2022-09-13T01:00:00+00:00Let’s say that by no means should an attribute of type passport-number leave your MISP instance. Aside from the analyst following best practices when encoding the data, MISP does not have a built-in mechanism to prevent these leaks to happen, but now you can achieve this by using a third-party tool called misp-guard.2022-09-13T01:00:00+00:00https://www.misp-project.org/2022/09/13/MISP.2.4.162.released.html/MISP - MISP 2.4.162 released with a new periodic notification system, workflow updates and many improvements2022-09-13T01:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.162 with a new periodic notification system, workflow updates and many improvements.2022-09-13T01:00:00+00:00https://www.misp-project.org/2022/08/11/MISP.2.4.161.released.html/MISP - MISP 2.4.161 released with small improvements and bugs fixed2022-08-11T01:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.161.
Small improvements A new option added to log the last API request of an API key.2022-08-11T01:00:00+00:00https://www.misp-project.org/2022/08/08/MISP-scraper.html/MISP - MISP web scraper2022-08-08T01:00:00+00:00MISP web scraper There are a lot of websites that regularly publish reports on new threats, campaigns or actors with useful indicators, references and context information.2022-08-08T01:00:00+00:00https://www.misp-project.org/2022/08/08/MISP.2.4.160.released.html/MISP - MISP 2.4.160 released with new workflow feature, new correlation engines and many major improvements2022-08-08T01:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.160. With the August summer-holiday season kicking into high gear, we have a very special release for you all, containing a long list of major new features, improvements and general quality of life improvements.2022-08-08T01:00:00+00:00https://www.misp-project.org/past-events/MISP - Past MISP-related events2022-08-04T04:00:05.402935+00:00Past conferences Past conferences featuring MISP core members talking about MISP and/or threat intelligence. Some links include video recordings.
2021 Video: MISP Fundamentals2022-08-04T04:00:05.402935+00:00https://www.misp-project.org/sizing-your-misp-instance/MISP - Sizing your MISP instance2022-07-01T04:00:05.063063+00:00Sizing your MISP instance Sizing a MISP instance highly depends on how the instance will be used. The number of users, data ingested, data points used, number of events, number of correlations and API usage are all parameters which should be considered while sizing your instance.2022-07-01T04:00:05.063063+00:00https://www.misp-project.org/2022/05/30/MISP.2.4.159.released.html/MISP - MISP 2.4.159 released with many improvements including performance2022-05-30T01:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.159. This releases includes many improvements, bug fixes and improvements concerning performance on large datasets.2022-05-30T01:00:00+00:00https://www.misp-project.org/2022/04/20/MISP.2.4.158.released.html/MISP - MISP 2.4.158 security fix and general improvement release2022-04-20T01:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.158. This release includes a series of security fixes and as such we highly encourage everyone to update to this version as soon as possible.2022-04-20T01:00:00+00:00https://www.misp-project.org/2022/03/25/MISP.2.4.157.released.html/MISP - MISP 2.4.157 released including some usability fixes following the large changes of 2.4.156 along with some improvements2022-03-25T00:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.157, following a series of bug fixes as a quick follow up to 2.2022-03-25T00:00:00+00:00https://www.misp-project.org/2022/03/02/MISP.2.4.154.released.html/MISP - MISP 2.4.154 released including tools for managing rapidly changing communities2022-03-02T00:00:00+00:00MISP 2.4.154 released with a host of new features and fixes, including some new tools that help us navigate the current geo-political landscape when sharing information.2022-03-02T00:00:00+00:00https://www.misp-project.org/2022/03/03/MISP.2.4.155.released.html/MISP - MISP 2.4.155 - quick bugfix release2022-03-03T00:00:00+00:00This release is a rapid follow up to v2.4.154, addressing several rather annoying issues
Bugfixes Various bugfixes to the sharing group blueprint system (especially to it being more restrictive than intended) Updating the DB schema to avoid the diagnostics complaining Fixed an issue with organisation meta fields defaulting to null rather than ’’ (causing the blueprint issue mentioned above) Rework of the DB schema dumper Fixes to the Kali Linux installer Acknowledgement We would like to thank all the contributors, reporters and users who have helped us in the past months to improve MISP and information sharing at large.2022-03-03T00:00:00+00:00https://www.misp-project.org/2022/03/18/MISP.2.4.156.released.html/MISP - MISP 2.4.156 released including a new synchronisation event signing mechanism and many new features2022-03-18T00:00:00+00:00We are pleased to announce the immediate availability of MISP v2.4.156 - a release bringing several new features and fixes two critical vulnerabilities.2022-03-18T00:00:00+00:00https://www.misp-project.org/commercial-support/MISP - MISP Commercial Support2022-02-08T05:00:03.423943+00:00MISP Commercial Support is an overview of trusted commercial partners providing support for MISP.
MISP project also provides MISP Professional Services (MSP) if you want to directly support the MISP project and ensure its sustainability.2022-02-08T05:00:03.423943+00:00https://www.misp-project.org/2022/02/04/MISP.2.4.153.released.html/MISP - MISP 2.4.153 released with improvements and bugs fixes2022-02-04T00:00:00+00:00MISP 2.4.153 released MISP UI translation in Thai added. Improved the debugging of the synchronisation, including more meaningful messages in debug logs.2022-02-04T00:00:00+00:00https://www.misp-project.org/who/MISP - Who2022-02-02T05:00:03.991277+00:00Who is behind the MISP project? The core team behind the MISP project is composed of motivated people who think that information sharing can be improved and supported by creating practical open source tools, open format and practises.2022-02-02T05:00:03.991277+00:00https://www.misp-project.org/misp-summit/MISP - Virtual MISP Summit 0x06 - 21st October 20212022-02-02T05:00:03.987122+00:00Virtual MISP Summit 0x06 - Thursday 21st October 2021 On Thursday 21st October 2021, the 6th MISP summit will take place online.2022-02-02T05:00:03.987122+00:00https://www.misp-project.org/tools/MISP - Tools2022-02-02T05:00:03.982985+00:00Software and Tools Many open source and proprietary tools integrate MISP support (MISP format or API) in order to extend their tools or MISP itself.2022-02-02T05:00:03.982985+00:00https://www.misp-project.org/security/MISP - Security Advisories and Reporting Security Vulnerabilities2022-02-02T05:00:03.978495+00:00Reporting security vulnerabilities for MISP or related MISP project repositories Reporting security vulnerabilities is of great importance for us, as MISP is used in multiple critical infrastructures.2022-02-02T05:00:03.978495+00:00https://www.misp-project.org/hackathon/MISP - Open Source Security hackathon - Monday 25th October 2021 and Tuesday 26th October 20212022-02-02T05:00:03.974142+00:00Open Source Security hackathon - Monday 25th October 2021 and Tuesday 26th October 2021 CIRCL in collaboration with the MISP Project is organising the 5th Open Source Security Software Hackathon, which will take place over two days, on Monday 25th October 2021 and Tuesday 26th October 2021.2022-02-02T05:00:03.974142+00:00https://www.misp-project.org/research-projects/MISP - MISP, research projects2022-02-02T05:00:03.969911+00:00Project (1) Pauline Bourmeau - The Social Perspective in the Intelligence Activity among Information Sharing Communities - CNAM Paris (Supervisor Philippe Baumard).2022-02-02T05:00:03.969911+00:00https://www.misp-project.org/press/MISP - MISP, press2022-02-02T05:00:03.961379+00:00Announcements and press releases The general purpose announcements that we publish are available on the news page. Write us an email at info@misp-project.2022-02-02T05:00:03.961379+00:00https://www.misp-project.org/license/MISP - MISP, Overview of the licenses used in the MISP Project (software, libraries and knowledge base)2022-02-02T05:00:03.957044+00:00MISP, Overview of the licenses used in the MISP Project (software, libraries and knowledge base) The MISP project is a large open source project, aiming to support and improve information sharing and threat intelligence analysis at large.2022-02-02T05:00:03.957044+00:00https://www.misp-project.org/professional-services/MISP - MISP Professional Services2022-02-02T05:00:03.952628+00:00MISP Professional Services (MPS) is a program handled by the lead developers of MISP Project, in order to offer highly skilled services around MISP and to support the sustainability of the MISP project.2022-02-02T05:00:03.952628+00:00https://www.misp-project.org/openapi/MISP - MISP OpenAPI spec2022-02-02T05:00:03.948076+00:002022-02-02T05:00:03.948076+00:00https://www.misp-project.org/governance/MISP - MISP Model of Governance2022-02-02T05:00:03.943766+00:00MISP Model of Governance MISP project is a large open source project with the goal to make viable tools and format to improve information sharing at large.2022-02-02T05:00:03.943766+00:00https://www.misp-project.org/features/MISP - MISP features and functionalities2022-02-02T05:00:03.939443+00:00Features of MISP, the open source threat sharing platform. A threat intelligence platform for sharing, storing and correlating Indicators of Compromise of targeted attacks, threat intelligence, financial fraud information, vulnerability information or even counter-terrorism information.2022-02-02T05:00:03.939443+00:00https://www.misp-project.org/documentation/MISP - MISP Documentation and Support2022-02-02T05:00:03.934867+00:00MISP Documentation The MISP documentation is maintained in the misp-book project. The documentation is in git book format and we welcome contribution.2022-02-02T05:00:03.934867+00:00https://www.misp-project.org/feeds/MISP - MISP Default Feeds2022-02-02T05:00:03.930510+00:00MISP includes a set of public OSINT feeds in its default configuration. The feeds can be used as a source of correlations for all of your events and attributes without the need to import them directly into your system.2022-02-02T05:00:03.930510+00:00https://www.misp-project.org/datamodels/MISP - MISP data models - MISP core format - MISP taxonomies2022-02-02T05:00:03.926124+00:00MISP is not only a software but also a series of data models created by the MISP community. MISP includes a simple and practical information sharing format expressed in JSON that can be used with MISP software or by any other software.2022-02-02T05:00:03.926124+00:00https://www.misp-project.org/contributors/MISP - MISP contributors per repository2022-02-02T05:00:03.921541+00:00Contributors
Top contributors per commit
MISP The repository MISP is part of the MISP project and has the following top contributors2022-02-02T05:00:03.921541+00:00https://www.misp-project.org/communities/MISP - MISP Communities and MISP Feeds2022-02-02T05:00:03.917196+00:00MISP Communities MISP is an open source software and it is also a large community of MISP users creating, maintaining and operating communities of users or organizations sharing information about threats or cyber security indicators worldwide.2022-02-02T05:00:03.917196+00:00https://www.misp-project.org/compliance/ISO-IEC-27010/MISP - MISP as supporting platform for sharing information, following ISO/IEC 27010:20152022-02-02T05:00:03.912924+00:00MISP as supporting platform for sharing information, following ISO/IEC 27010:2015 Malicious cyber actors are becoming more organised, growing smarter and becoming more sophisticated, which is rendering traditional defence methods and tools significantly less effective in dealing with the constantly new threats appearing on the horizon.2022-02-02T05:00:03.912924+00:00https://www.misp-project.org/compliance/GDPR/MISP - Information sharing and cooperation enabled by GDPR2022-02-02T05:00:03.908402+00:00Information sharing and cooperation enabled by GDPR Version: 1.1 - Tuesday, 30 January 2018
Introduction The General Data Protection Regulation (GDPR) aims to reduce legal uncertainty and limit the interpretations by setting out clear rules and conditions for the processing and sharing of personal data as well as the protection of natural persons with regard to the processing of personal data.2022-02-02T05:00:03.908402+00:00https://www.misp-project.org/compliance/NISD/MISP - How MISP enables stakeholders identified by the NISD to perform key activities2022-02-02T05:00:03.904213+00:00How MISP enables stakeholders identified by the NISD to perform key activities Network and Information Security (NIS) means ‘the ability of a network or an information system to resist accidental events or unlawful or malicious actions that compromise the availability, authenticity, integrity and confidentiality of data and the related services’ .2022-02-02T05:00:03.904213+00:00https://www.misp-project.org/support/MISP - Help, Support, and Forums2022-02-02T05:00:03.899911+00:00Help, Support, and Forums Help and support for MISP is available from the documentation, GitHub issues, and Gitter rooms which are explained below.2022-02-02T05:00:03.899911+00:00https://www.misp-project.org/events-webinar/MISP - Events around MISP - Next webinar with partners2022-02-02T05:00:03.882208+00:00CRAWL, WALK, RUN series – Farsight Security / MISP webinars In this three-parts webinar series Farsight Security and CIRCL will provide an overview of Farsight’s Passive DNS data, how historical Passive DNS objective observations can be used to uncover malicious activities going back in time.2022-02-02T05:00:03.882208+00:00https://www.misp-project.org/events/MISP - Events around MISP2022-02-02T05:00:03.877932+00:00MISP Events Want to join us at an event, discuss opportunities or projects around the MISP project, share your experience about threat intelligence or discuss how MISP could be improved to support security professionals?2022-02-02T05:00:03.877932+00:00https://www.misp-project.org/download/MISP - Download2022-02-02T05:00:03.873695+00:00Download and Install MISP MISP source code is available on GitHub including documentation and scripts for installation.
ChangeLog contains a detailed list of updates for each software release in the core of the MISP software.2022-02-02T05:00:03.873695+00:00https://www.misp-project.org/covid-19-misp/MISP - COVID-19 MISP2022-02-02T05:00:03.869208+00:00COVID-19 MISP Information Sharing Community COVID-19 MISP is a MISP instance retrofitted for a COVID-19 information sharing community, focusing on two areas of sharing:2022-02-02T05:00:03.869208+00:00https://www.misp-project.org/contributing/MISP - Contributing to MISP Project2022-02-02T05:00:03.864940+00:00Contributing to MISP Project MISP project is a large free software project composed of multiple sub-projects which are contributed by different contributors who are generally active users of the MISP project.2022-02-02T05:00:03.864940+00:00https://www.misp-project.org/2016/07/22/MISP-2.4.49-released.html/MISP - MISP 2.4.49 released with many improvements and fixes2016-07-22T01:00:00+00:00A version of MISP has been released: 2.4.49 including many bug fixes, updates and improvements.
Updates to the MISP module interface to allow a timeout on hover modules and allowing to timeout slow modules queries.2016-07-22T01:00:00+00:00https://www.misp-project.org/2016/08/01/MISP-1st-Hackathon.html/MISP - MISP Hackathon 20162016-08-01T01:00:00+00:00MISP Hackathon 2016 The 4th August 2016, a MISP hackathon will take place in Luxembourg (at the local hackerspace) and also remotely.2016-08-01T01:00:00+00:00https://www.misp-project.org/2016/08/10/MISP-2.4.50-released.html/MISP - MISP 2.4.50 released including new features, security and bug fixes.2016-08-10T01:00:00+00:00A version of MISP has been released: 2.4.50 including many bug fixes, updates and improvements.
New export and import MISP module framework in MISP.2016-08-10T01:00:00+00:00https://www.misp-project.org/2016/08/11/MISP-Training-in-Brussels.html/MISP - MISP training, “the Brussels Edition”, CIRCL in collaboration with CERT.EU - September 5th 20162016-08-11T01:00:00+00:00On September 5th 2016 and after 3 successful editions, the MISP (Malware Information and Threat Sharing Platform) training is traveling to Brussels.2016-08-11T01:00:00+00:00https://www.misp-project.org/2016/08/12/Building-an-OCR-import-module-in-MISP.html/MISP - Building an OCR import module in MISP2016-08-12T01:00:00+00:00Building an Optical Character Recognition module in MISP When collecting information from different places, analysts need sometime to perform OCR on documents (like report, faxes, images) to import and correlate the information in their MISP instance.2016-08-12T01:00:00+00:00https://www.misp-project.org/2016/08/29/MISP-2.4.51-released.html/MISP - MISP 2.4.51 released including new features and many bug fixes.2016-08-29T01:00:00+00:00A version of MISP has been released: 2.4.51 including many new features, bug fixes and improvements.
New Internal MISP sync mode to allow a set of MISP instances belonging to the same organisation to replicate data (useful when a single organisation has multiple MISP instances).2016-08-29T01:00:00+00:00https://www.misp-project.org/2016/10/21/MISP-Internet-Drafts-Published.html/MISP - MISP Internet Drafts Published2016-10-21T01:00:00+00:00We recently released two Internet-Drafts describing the MISP format:
misp-core-format - the core JSON format of MISP which describes the Event format including meta-information, attributes, shadow attributes.2016-10-21T01:00:00+00:00https://www.misp-project.org/2016/10/22/MISP-2.4.53-released.html/MISP - MISP 2.4.53 released2016-10-22T01:00:00+00:00A new version 2.4.53 of MISP including several security fixes has been released.
We strongly recommend to update to this latest version as soon as possible.2016-10-22T01:00:00+00:00https://www.misp-project.org/2016/11/04/MISP-2.4.54-released.html/MISP - MISP 2.4.54 released2016-11-04T00:00:00+00:00A new version 2.4.54 of MISP including new features, bug and security fixes.
We strongly recommend to update to this latest version.2016-11-04T00:00:00+00:00https://www.misp-project.org/2016/11/16/Independence-and-Threat-Intelligence-Platforms.html/MISP - Independence and Threat Intelligence Platforms2016-11-16T00:00:00+00:00After the recent news of a Threat Intelligence Platform vendor stopping its activities, we have received some questions about our strategies as a Threat Intelligence Platform.2016-11-16T00:00:00+00:00https://www.misp-project.org/2016/11/22/MISP-2.4.55.released.html/MISP - MISP 2.4.55 released2016-11-22T00:00:00+00:00A new version of MISP 2.4.55 has just been released, including bug fixes and improvements.
This release is a transient release before the galaxy release (TTP-like support) coming up soon.2016-11-22T00:00:00+00:00https://www.misp-project.org/2016/12/07/MISP.2.4.56.released.html/MISP - MISP 2.4.56 released2016-12-07T00:00:00+00:00A new version of MISP 2.4.56 has been released, including bug fixes and improvements.
This is the first version introducing the misp-galaxy.2016-12-07T00:00:00+00:00https://www.misp-project.org/2016/12/19/MISP.2.4.57.released.html/MISP - MISP 2.4.57 released2016-12-19T00:00:00+00:00A new version of MISP 2.4.57 has been released, including bug fixes and improvements.
Two major new features were introduced in 2.2016-12-19T00:00:00+00:00https://www.misp-project.org/2016/12/22/MISP.2.4.58.released.html/MISP - MISP 2.4.58 released2016-12-22T00:00:00+00:00A new version of MISP 2.4.58 has been released, including bug fixes and a specific improvement to the correlation feature.2016-12-22T00:00:00+00:00https://www.misp-project.org/2017/01/16/Information-Sharing-Maturity-Model.html/MISP - Information Sharing Maturity Model2017-01-16T00:00:00+00:00Here at the MISP project, we are practical oriented people. We create software (from MISP core to MISP workbench), develop data models (such as taxonomies, warning-lists and galaxies) and build practical standards to solve information sharing challenges and improve the general state of information sharing.2017-01-16T00:00:00+00:00https://www.misp-project.org/2017/01/17/MISP.2.4.60.released.html/MISP - MISP 2.4.60 released2017-01-17T00:00:00+00:00A new version of MISP 2.4.60 has been released, including bug fixes and the long awaited attribute-level tagging feature.
All tags (local or from taxonomies) can now be also applied at the attribute level.2017-01-17T00:00:00+00:00https://www.misp-project.org/2017/01/22/MISP.2.4.61.released.html/MISP - MISP 2.4.61 released2017-01-22T00:00:00+00:00A new version of MISP 2.4.61 has been released, including a critical bug fix, new features and minor updates. We strongly recommend to update MISP to this latest version.2017-01-22T00:00:00+00:00https://www.misp-project.org/2017/01/26/MISP.2.4.62.released.html/MISP - MISP 2.4.62 and PyMISP 2.4.62 released2017-01-26T00:00:00+00:00A new version of MISP 2.4.62 has been released, including bug fixes and new features.
MISP feed has been expanded to support local feed allowing users to import feeds from local directories (if MISP format) or local files (like free-text or CSV import) in addition to the network feeds.2017-01-26T00:00:00+00:00https://www.misp-project.org/2017/02/01/MISP.2.4.63.released.html/MISP - MISP 2.4.63 released2017-02-01T00:00:00+00:00A new version of MISP 2.4.63 has been released, including bug fixes and new features.
New features in the API:2017-02-01T00:00:00+00:00https://www.misp-project.org/2017/02/09/MISP.2.4.65.released.html/MISP - MISP 2.4.65 released2017-02-09T00:00:00+00:00A new version of MISP 2.4.65 (and 2.4.64) has been released, including bug fixes and new features.
API access added to the MISP statistics providing additional statistics regarding information on contributions by organisation, attributes used and tags.2017-02-09T00:00:00+00:00https://www.misp-project.org/2017/02/16/Sighting-The-Next-Level.html/MISP - Sighting the next level2017-02-16T00:00:00+00:00Sighting is an endless topic of discussion. This is a required feature especially when information or indicators are regularly shared to gather feedback from users said shared data.2017-02-16T00:00:00+00:00https://www.misp-project.org/2017/02/24/MISP.2.4.67.released.html/MISP - MISP 2.4.67 released2017-02-24T00:00:00+00:00A new version of MISP 2.4.67 has been released, including improvements to the sighting feature, user management and activity visualisation.2017-02-24T00:00:00+00:00https://www.misp-project.org/2017/03/08/MISP.2.4.68.released.html/MISP - MISP 2.4.68 released2017-03-08T00:00:00+00:00A new version of MISP 2.4.68 has been released including multiple bug fixes and improvements.
Improvements and features added:
Enable sync permissions for read-only accounts.2017-03-08T00:00:00+00:00https://www.misp-project.org/2017/03/10/MISP.2.4.69.released.html/MISP - MISP 2.4.69 released2017-03-10T00:00:00+00:00A new version of MISP 2.4.69 has been released including multiple security bug fixes and minor improvements.
Improvements added:
User creation now shows a warning if the encrypted notification cannot be send due to encryption issue.2017-03-10T00:00:00+00:00https://www.misp-project.org/2017/03/26/MISP.2.4.70.released.html/MISP - MISP 2.4.70 released2017-03-26T00:00:00+00:00A new version of MISP 2.4.70 has been released including new features, improvements and important bug fixes.
A significant improvement has been introduced to the MISP user-interface to make it more accessible especially for visually impaired users.2017-03-26T00:00:00+00:00https://www.misp-project.org/2017/04/11/MISP.2.4.71.released.html/MISP - MISP 2.4.71 released2017-04-11T01:00:00+00:00A new version of MISP 2.4.71 has been released including new features, improvements and important bug fixes.
Distribution can now be set in the free-text and modules import.2017-04-11T01:00:00+00:00https://www.misp-project.org/2017/04/14/MISP.2.4.72.released.html/MISP - MISP 2.4.72 released2017-04-14T01:00:00+00:00A new version of MISP 2.4.72 has been released including improvements and important bug fixes.
Improvements have been introduced to better support large MISP instances:2017-04-14T01:00:00+00:00https://www.misp-project.org/2017/05/09/MISP.2.4.73.released.html/MISP - MISP 2.4.73 released2017-05-09T01:00:00+00:00A new version of MISP 2.4.73 has been released including new features, improvements and bug fixes.
A new module type Cortex has been introduced allowing for easy integration of MISP and Cortex.2017-05-09T01:00:00+00:00https://www.misp-project.org/2017/05/30/MISP.2.4.74.released.html/MISP - MISP 2.4.74 released2017-05-30T01:00:00+00:00A new version of MISP 2.4.74 has been released including new features, improvements and bug fixes.
The ZeroMQ pub-sub feature has been significantly improved in MISP to allow for a complete flexible notification scheme for a host of actions which take place within a MISP instance, such as:2017-05-30T01:00:00+00:00https://www.misp-project.org/2017/06/13/MISP.2.4.75.released.html/MISP - MISP 2.4.75 released2017-06-13T01:00:00+00:00A new version of MISP 2.4.75 has been released including bug fixes and a set of performance improvements.
In this release the most important improvement is performance tuning to improve the day-to-day life of the users.2017-06-13T01:00:00+00:00https://www.misp-project.org/2017/06/21/MISP.2.4.76.released.html/MISP - MISP 2.4.76 released2017-06-21T01:00:00+00:00A new version of MISP 2.4.76 has been released including bug fixes and a set of performance improvements at the ingestion level.2017-06-21T01:00:00+00:00https://www.misp-project.org/2017/07/12/MISP.2.4.77.released.html/MISP - MISP 2.4.77 released2017-07-12T01:00:00+00:00A new version of MISP 2.4.77 has been released including security fixes, bug fixes and various improvements.
This version includes multiple security fixes reported by cert.2017-07-12T01:00:00+00:00https://www.misp-project.org/2017/08/06/MISP.2.4.78.released.html/MISP - MISP 2.4.78 released2017-08-06T01:00:00+00:00A new version of MISP 2.4.78 has been released including an important security fix (if you use sharing groups), multiple bug fixes and some new functionalities.2017-08-06T01:00:00+00:00https://www.misp-project.org/2017/08/25/MISP.2.4.79.released.html/MISP - MISP 2.4.79 released2017-08-25T01:00:00+00:00A new version of MISP 2.4.79 has been released including an important security fix (persistent XSS on comment field), multiple bug fixes and new functionalities.2017-08-25T01:00:00+00:00https://www.misp-project.org/2017/09/18/MISP.2.4.81.released.html/MISP - MISP 2.4.81 released (aka new graphical visualisation and STIX 2.0 export)2017-09-18T01:00:00+00:00A new version of MISP 2.4.81 has been released including a significant rework of the graphical visualisation, support for STIX 2.2017-09-18T01:00:00+00:00https://www.misp-project.org/2017/09/18/MISP.2.4.80.released.html/MISP - MISP 2.4.80 released (aka MISP objects release)2017-09-18T01:00:00+00:00A new version of MISP 2.4.80 has been released including the most awaited MISP objects feature along with other new features, security fix CVE-2017-14337 and improvements.2017-09-18T01:00:00+00:00https://www.misp-project.org/2017/11/10/MISP.2.4.82.released.html/MISP - MISP 2.4.82 released (aka improved pub-sub ZMQ)2017-11-10T00:00:00+00:00A new version of MISP 2.4.82 has been released including an improved publish-subscribe ZMQ format, improvements in the feeds system, sightings are now ingested and synchronised among MISP instances, many bug fixes and export improvements.2017-11-10T00:00:00+00:00https://www.misp-project.org/2017/12/06/MISP.2.4.83.released.html/MISP - MISP 2.4.83 released (aka attributes-level tag filtering and more)2017-12-06T00:00:00+00:00A new version of MISP 2.4.83 has been released including attribute level tag filtering on synchronisation, full audit logging via ZMQ or Syslog, user email domain restriction at the org level, many more improvements and bug fixes.2017-12-06T00:00:00+00:00https://www.misp-project.org/2017/12/22/MISP.2.4.85.released.html/MISP - MISP 2.4.85 released (aka feeds and warning-lists improvement and more)2017-12-22T00:00:00+00:00A new version of MISP 2.4.85 has been released including improvements to the feed ingestion performance, warning-list handling and many bug fixes.2017-12-22T00:00:00+00:00https://www.misp-project.org/2018/01/09/Using-MISP-to-share-vulnerability-information-efficiently.html/MISP - Using MISP to share vulnerability information efficiently2018-01-09T00:00:00+00:00Using MISP to share vulnerability information efficiently Software and hardware vulnerabilities are often discussed, shared, prepared, analysed and reviewed before publication.2018-01-09T00:00:00+00:00https://www.misp-project.org/2018/01/16/MISP.2.4.86.released.html/MISP - MISP 2.4.86 released (aka sharing groups improvement, large information sharing communities support and more)2018-01-16T00:00:00+00:00A new version of MISP 2.4.86 has been released including improvements to the sharing groups and their respective APIs, granular access control of MISP-modules at an instance-level along with the usual set of bug fixes.2018-01-16T00:00:00+00:00https://www.misp-project.org/2018/01/28/MISP.2.4.87.html/MISP - MISP 2.4.87 released (aka translate everything, improvements everywhere and more)2018-01-28T00:00:00+00:00A new version of MISP 2.4.87 has been released including a massive contribution enabling support for internationalisation and localisation in the MISP UI (a huge thank to Steve Clement of CIRCL for the tedious work), as well as a host of improvements to the UI, feed and APIs, including bug fixes and speed improvements.2018-01-28T00:00:00+00:00https://www.misp-project.org/2018/02/21/MISP.2.4.88.released.html/MISP - MISP 2.4.88 released (aka Fuzzy hashing correlation, STIX 1.1 import and many API improvements)2018-02-21T00:00:00+00:00A new version of MISP 2.4.88 has been released including fuzzy hashing correlation (ssdeep), STIX 1.1 import functionality, various API improvements and many bug fixes2018-02-21T00:00:00+00:00https://www.misp-project.org/2018/03/23/MISP.2.4.89.released.html/MISP - MISP 2.4.89 released (aka Event graph viewer/editor)2018-03-23T00:00:00+00:00A new version of MISP 2.4.89 has been released including a new MISP event graph viewer/editor, many API improvements and critical bug fixes (including security related bug fixes).2018-03-23T00:00:00+00:00https://www.misp-project.org/2018/04/19/Extended-Events-Feature.html/MISP - Introducing The New Extended Events Feature in MISP2018-04-19T01:00:00+00:00Introducing Extended Events We have just released a new feature for MISP that allows users to build full blown events that extend an existing event, giving way to a combined event view that includes a sum total of the event along with all extending events.2018-04-19T01:00:00+00:00https://www.misp-project.org/2018/04/20/MISP.2.4.90.released.html/MISP - MISP 2.4.90 released (aka Extended Events release)2018-04-20T01:00:00+00:00A new version of MISP 2.4.90 has been released including the new extended events feature along with many updates in improvements in the API, user-interface (including many improvement in the graph editor) and many bug fixes.2018-04-20T01:00:00+00:00https://www.misp-project.org/2018/05/16/MISP.2.4.91.released.html/MISP - MISP 2.4.91 released (aka distribution visualisation, galaxy at attribute level and privacy notice list)2018-05-16T01:00:00+00:00A new version of MISP 2.4.91 has been released including new major features, improvements and bug fixes.
Distribution and sharing visualisation MISP 2.2018-05-16T01:00:00+00:00https://www.misp-project.org/2018/06/07/MISP.2.4.92.released.html/MISP - MISP 2.4.92 released (aka performance improvement)2018-06-07T01:00:00+00:00A new version of MISP 2.4.92 has been released including aggressive performance boosts, various improvements and bug fixes.
We received feedback from various users about the negative impact on performance when the MISP warning-lists are enabled (a feature allowing the detection and filtering of false positive attributes in MISP).2018-06-07T01:00:00+00:00https://www.misp-project.org/2018/06/27/MISP.2.4.93.released.html/MISP - MISP 2.4.93 released (aka ATT&CK integration)2018-06-27T01:00:00+00:00A new version of MISP 2.4.93 has been released including a much improved and tightly integrated MITRE ATT&CK interface, a new event locking functionality, initial support for a multilingual interface, various fixes including a security fix (CVE-2018-12649).2018-06-27T01:00:00+00:00https://www.misp-project.org/2018/08/06/MISP.2.4.94.released.html/MISP - MISP 2.4.94 released (aka summer improvements)2018-08-06T01:00:00+00:00A new version of MISP 2.4.94 has been released including an improved event graph interface, a new Elasticsearch plugin, various extensions and enhancements to the API, clean-ups and many improvements.2018-08-06T01:00:00+00:00https://www.misp-project.org/2018/09/06/MISP.2.4.95.released.html/MISP - MISP 2.4.95 released (aka API search improvement)2018-09-06T01:00:00+00:00A new version of MISP (2.4.95) has been released with the first stage of a complete rework and refactoring of the API exports, allowing for more flexibility, improved search capabilities, performance and extendability.2018-09-06T01:00:00+00:00https://www.misp-project.org/2018/10/09/MISP.2.4.96.released.html/MISP - MISP 2.4.96 released (aka API everywhere release)2018-10-09T01:00:00+00:00A new version of MISP (2.4.96) has been released with a complete rework, refactoring and simplification of the restSearch API, allowing for more flexibility, improved search capabilities, performance and extendability.2018-10-09T01:00:00+00:00https://www.misp-project.org/2018/10/30/MISP.2.4.97.released.html/MISP - MISP 2.4.97 released (aka so many new features)2018-10-30T00:00:00+00:00A new version of MISP (2.4.97) has been released with new features such as related tags, the sighting restSearch API, a new French localisation along with many improvements to the API and he import/export capabilities, such as improved support for DHS AIS STIX 1 files.2018-10-30T00:00:00+00:00https://www.misp-project.org/2018/11/26/MISP.2.4.98.released.html/MISP - MISP 2.4.98 released (aka usability improvements and SleuthKit mactime import)2018-11-26T00:00:00+00:00A new version of MISP (2.4.98) has been released with new features such as improved UI consistency (such as attributes search output), improved validation error messages, a new built-in experimental SleuthKit mactime import, new small features and many bugs fixed.2018-11-26T00:00:00+00:00https://www.misp-project.org/2018/12/06/MISP.2.4.99.released.html/MISP - MISP 2.4.99 released (aka API/UI fixes and critical security vulnerability fixed)2018-12-06T00:00:00+00:00A new version of MISP (2.4.99) has been released with improvements in the UI, API, STIX import and a fixed critical security vulnerability.2018-12-06T00:00:00+00:00https://www.misp-project.org/2019/01/01/MISP.2.4.100.released.html/MISP - MISP 2.4.100 released (aka happy new year release)2019-01-01T00:00:00+00:00Happy new year! We are so proud of our community which has supported us for the past year and we hope to do even better for 2019.2019-01-01T00:00:00+00:00https://www.misp-project.org/2019/01/20/MISP.2.4.101.released.html/MISP - MISP 2.4.101 released (aka 3 features for free)2019-01-20T00:00:00+00:00A new version of MISP (2.4.101) has been released with 3 main new features (tag collections, improved tag/galaxy selector and MISP instance caching), along with a host of improvements and bug fixes.2019-01-20T00:00:00+00:00https://www.misp-project.org/2019/02/02/MISP.2.4.102.released.html/MISP - MISP 2.4.102 released (aka bug fixes and FOSDEM release)2019-02-02T00:00:00+00:00A new version of MISP (2.4.102) has been released with several fixes, various UI improvements, new types and a praise to the open source community.2019-02-02T00:00:00+00:00https://www.misp-project.org/2019/03/04/MISP.2.4.103.released.html/MISP - MISP 2.4.103 released (aka UI improvements)2019-03-04T00:00:00+00:00A new version of MISP (2.4.103) has been released with significant UI improvements (including a new flexible attribute filtering tool at the event level), many bug fixes and a fix to a security vulnerability (CVE-2019-9482) which was affecting sighting visibility.2019-03-04T00:00:00+00:00https://www.misp-project.org/2019/03/26/MISP.2.4.104.released.html/MISP - MISP 2.4.104 released (aka too many new features)2019-03-26T00:00:00+00:00A new version of MISP (2.4.104) has been released with a host of new features such as new overlap feed comparator, a new graph visualisation of event and attribute distributions, a history/bookmark system for the REST client and many others.2019-03-26T00:00:00+00:00https://www.misp-project.org/2016/10/02/MISP-Upcoming-Activities.html/MISP - MISP Upcoming Activities in October and November 20162016-10-02T01:00:00+00:00The next months for the MISP core team, it is full of interesting activities and upcoming events.
We will participate to the following events:2016-10-02T01:00:00+00:00https://www.misp-project.org/2019/03/28/MISP.2.4.105.released.html/MISP - MISP 2.4.105 released (aka security fix for CVE-2019-10254)2019-03-28T00:00:00+00:00A new version of MISP (2.4.105) has been released to fix a security vulnerability (CVE-2019-10254) in addition to some minor improvements and a fix for the STIX 1.2019-03-28T00:00:00+00:00https://www.misp-project.org/2019/04/25/MISP.2.4.106.released.html/MISP - MISP 2.4.106 released (aka Too many improvements)2019-04-25T01:00:00+00:00A new version of MISP (2.4.106) has been released with a host of improvements, including new features such as a feed cache search, CLI tools to manage your MISP instance along with improved diagnostics.2019-04-25T01:00:00+00:00https://www.misp-project.org/2019/05/13/MISP.2.4.107.released.html/MISP - MISP 2.4.107 released (aka similar objects review, yara native export)2019-05-13T01:00:00+00:00A new version of MISP (2.4.107) has been released with a host of new features, improvements and security fixes. We strongly advise all users to update their MISP installation to this latest version.2019-05-13T01:00:00+00:00https://www.misp-project.org/2019/06/05/MISP.2.4.108.released.html/MISP - MISP 2.4.108 released (aka copy-paste-and-sync feature)2019-06-05T01:00:00+00:00A new version of MISP (2.4.108) has been released with a host of new features, improvements and bugs fixed. We strongly advise all users to update their MISP installations to this latest version.2019-06-05T01:00:00+00:00https://www.misp-project.org/2019/06/14/MISP.2.4.109.released.html/MISP - MISP 2.4.109 released (aka cool-attributes-to-object)2019-06-14T01:00:00+00:00MISP 2.4.109 released A new version of MISP (2.4.109) has been released with a host of new features, improvements, bug fixes and a minor security fix.2019-06-14T01:00:00+00:00https://www.misp-project.org/2019/07/08/MISP.2.4.110.released.html/MISP - MISP 2.4.110 released (aka local-tags and new MISP modules supporting MISP standard format)2019-07-08T01:00:00+00:00MISP 2.4.110 released A new version of MISP (2.4.110) has been released with a host of new features, improvements, many bugs fixed and one security fix.2019-07-08T01:00:00+00:00https://www.misp-project.org/2019/07/19/MISP.2.4.111.released.html/MISP - MISP 2.4.111 released (aka improved proposal sync)2019-07-19T01:00:00+00:00MISP 2.4.111 released A new version of MISP (2.4.111) has been released with an improved proposal sync, minor improvements and bugs fixed.2019-07-19T01:00:00+00:00https://www.misp-project.org/2019/08/01/MISP.2.4.112.released.html/MISP - MISP 2.4.112 released (aka summer fixes and improvement)2019-08-01T01:00:00+00:00MISP 2.4.112 released A new version of MISP (2.4.112) has been released with a host of API fixes, improvements and a security fix.2019-08-01T01:00:00+00:00https://www.misp-project.org/2019/08/19/MISP.2.4.113.released.html/MISP - MISP 2.4.113 released (aka the bugs fixing marathon)2019-08-19T01:00:00+00:00MISP 2.4.113 released A new version of MISP (2.4.113) with tons of fixes and small improvements. We strongly recommend to update to this version.2019-08-19T01:00:00+00:00https://www.misp-project.org/2019/08/31/MISP.2.4.114.released.html/MISP - MISP 2.4.114 released (aka the community care package release)2019-08-31T01:00:00+00:00MISP 2.4.114 released A new version of MISP (2.4.114) with some new features supporting collaboration and a list of fixes and small improvements.2019-08-31T01:00:00+00:00https://www.misp-project.org/2019/09/10/MISP.2.4.115.released.html/MISP - MISP 2.4.115 released (aka CVE-2019-16202 and sync speed improvement)2019-09-10T01:00:00+00:00MISP 2.4.115 released A new version of MISP (2.4.115) with a major security fix (CVE-2019-16202) and various small improvements has been released.2019-09-10T01:00:00+00:00https://www.misp-project.org/2019/09/12/Decaying-Of-Indicators.html/MISP - Decaying of Indicators - MISP improved model to expire indicators based on custom models2019-09-12T01:00:00+00:00An improved and flexible model to expire indicators This blog post aims to give a thorough introduction of a new functionality added in MISP 2.2019-09-12T01:00:00+00:00https://www.misp-project.org/2019/09/17/MISP.2.4.116.released.html/MISP - MISP 2.4.116 released (aka the new decaying feature)2019-09-17T01:00:00+00:00MISP 2.4.116 released A new version of MISP (2.4.116) has been release, including a long awaited major new feature that deals with decaying indicators in addition to a new ATT&CK sightings export and a new sync priority capability.2019-09-17T01:00:00+00:00https://www.misp-project.org/2019/09/25/hostev-vs-own-misp.html/MISP - Benefits of running your own MISP instance2019-09-25T01:00:00+00:00Benefits of running your own MISP instance One topic that regularly pops up during trainings and users that are just getting started with MISP in general is the question of running your own MISP versus using a hosted MISP instance.2019-09-25T01:00:00+00:00https://www.misp-project.org/2019/10/11/MISP.2.4.117.released.html/MISP - MISP 2.4.117 released (aka the the pre-conference season release)2019-10-11T01:00:00+00:00MISP 2.4.117 released A new version of MISP (2.4.117) has been release including major performance improvements in MISP and PyMISP, publish filter emails, throttling restSearch (very useful when you want to limit some users using the API of your MISP instance) and many more improvements.2019-10-11T01:00:00+00:00https://www.misp-project.org/2019/10/27/visualising_common_patterns_attack.html/MISP - Visualising common patterns using MISP and ATT&CK data2019-10-27T01:00:00+00:00Visualising common patterns using MISP and ATT&CK data Having access to a large amount of Threat information through MISP Threat Sharing communities gives you outstanding opportunities to aggregate this information and take the process of trying to understand how all this data fits together telling a broader story to the next level.2019-10-27T01:00:00+00:00https://www.misp-project.org/2019/11/10/MISP.2.4.118.released.html/MISP - MISP 2.4.118 released (aka the exclusivity tag release and SightingDB support)2019-11-10T00:00:00+00:00MISP 2.4.118 released A new version of MISP (2.4.118) has been release including a functionality that allows for tag exclusivity within taxonomies, the support for external Sighting sources via SightingDB and many fixes.2019-11-10T00:00:00+00:00https://www.misp-project.org/2019/12/04/MISP.2.4.119.released.html/MISP - MISP 2.4.119 released (aka the quality of life release)2019-12-04T00:00:00+00:00MISP 2.4.119 released A new version of MISP (2.4.119) has been released, including several functionalities that should make the operation of a MISP instance more convenient.2019-12-04T00:00:00+00:00https://www.misp-project.org/2020/01/21/MISP.2.4.120.released.html/MISP - MISP 2.4.120 released (aka the timeline release)2020-01-21T00:00:00+00:00MISP 2.4.120 released A new version of MISP (2.4.120) has been released, including an extension to the data-model adding the first_seen and last_seen values at the attribute and object levels.2020-01-21T00:00:00+00:00https://www.misp-project.org/2020/02/12/MISP.2.4.121.released.html/MISP - MISP 2.4.121 released (aka the security release)2020-02-12T00:00:00+00:00MISP 2.4.121 released A new version of MISP (2.4.121) has been released. This version is a security/bug fix release and users are highly encouraged to update as soon as possible.2020-02-12T00:00:00+00:00https://www.misp-project.org/2020/02/18/MISP.2.4.122.released.html/MISP - MISP 2.4.122 released (aka the bug fix release)2020-02-18T00:00:00+00:00MISP 2.4.122 released A new version of MISP (2.4.122) has been released. This version includes various fixes, minor new features and improvements.2020-02-18T00:00:00+00:00https://www.misp-project.org/2020/03/10/MISP.2.4.123.released.html/MISP - MISP 2.4.123 released (aka the dashboard and security fix release)2020-03-10T00:00:00+00:00MISP 2.4.123 released A new version of MISP (2.4.123) has been released. This version includes various security related fixed, and a new Dashboard system.2020-03-10T00:00:00+00:00https://www.misp-project.org/2020/03/27/cogsec-collab-misp-community.html/MISP - Cogsec Collab MISP Community - sharing group dedicated to misinformation and information campaigns2020-03-27T00:00:00+00:00We’re proud to announce the CogSec Collab MISP Community - the first public MISP sharing group dedicated to misinformation and information campaigns.2020-03-27T00:00:00+00:00https://www.misp-project.org/2020/04/06/MISP.2.4.124.released.html/MISP - MISP 2.4.124 released (aka the dashboard, auditing improvements)2020-04-06T01:00:00+00:00MISP 2.4.124 released A new version of MISP (2.4.124) has been released. This version includes various improvements including a new multiline widgets in the dashboard, auditing improvements and many bugs fixed.2020-04-06T01:00:00+00:00https://www.misp-project.org/2020/05/06/MISP.2.4.125.released.html/MISP - MISP 2.4.125 released (aka self-registration feature and feed improvements release)2020-05-06T01:00:00+00:00MISP 2.4.125 released A new version of MISP (2.4.125) has been released. This version includes various improvements including a major refactoring of the feed system, the addition of OTP, a new inbox system to allow for self-registration, sightings in the timeline visualisation and many more improvements.2020-05-06T01:00:00+00:00https://www.misp-project.org/2020/06/04/MISP.2.4.126.released.html/MISP - MISP 2.4.126 released (Spring release edition)2020-06-04T01:00:00+00:00MISP 2.4.126 released A new version of MISP (2.4.126) has been released a while ago, though we have forgotten to publish a blog post about it - thanks to @coolacid for the reminder.2020-06-04T01:00:00+00:00https://www.misp-project.org/2020/06/19/MISP.2.4.127.released.html/MISP - MISP 2.4.127 released (decay updates release edition)2020-06-19T01:00:00+00:00MISP 2.4.127 released A new version of MISP (2.4.127) has been released with an improved version of attributes decaying, new set of widgets, many improvements and bugs fixed.2020-06-19T01:00:00+00:00https://www.misp-project.org/2020/06/24/MISP.2.4.128.released.html/MISP - MISP 2.4.128 released (STIX import/export refactored release edition)2020-06-24T01:00:00+00:00MISP 2.4.128 released A new version of MISP (2.4.128) has been released with a significant refactoring of the STIX import/export along with many improvements and bugs fixed.2020-06-24T01:00:00+00:00https://www.misp-project.org/2020/07/28/MISP.2.4.129.released.html/MISP - MISP 2.4.129 released (merge event improved, event block rule system, security fixes and many bugs fixed)2020-07-28T01:00:00+00:00MISP 2.4.129 released A new version of MISP (2.4.129) has been released with an improved merge functionality, a new event block rule system, many security fixes and bugs fixed.2020-07-28T01:00:00+00:00https://www.misp-project.org/2020/07/30/publishing-open-data-using-MISP.html/MISP - Publishing open data from MISP2020-07-30T01:00:00+00:00Publish data on Open data portals with MISP The Open data format Open data defines the idea of making some data freely available for everyone to use with a possibility of redistribution in any form.2020-07-30T01:00:00+00:00https://www.misp-project.org/2020/07/31/MISP-galaxy-101.html/MISP - Creating a MISP Galaxy, 1012020-07-31T01:00:00+00:00MISP Galaxies MISP Galaxies and Clusters are an easy way to add context to data. Compared to the relatively simple concept of tags and taxonomies, they allow you to add more complex data structures.2020-07-31T01:00:00+00:00https://www.misp-project.org/2020/08/18/MISP-Monitoring-with-OpenNMS.html/MISP - MISP service monitoring (and a bit of healing) with OpenNMS2020-08-18T01:00:00+00:00MISP service monitoring (and a bit of healing) with OpenNMS Introduction: Many organisations adore how quick and easy MISP can be set up.2020-08-18T01:00:00+00:00https://www.misp-project.org/2020/08/21/MISP.2.4.130.released.html/MISP - MISP 2.4.130 released (Various fixes, performance improvements and new features)2020-08-21T01:00:00+00:00MISP 2.4.130 released A new version of MISP (2.4.130) has been released with performance improvements, multiple bugs fixed and new features.2020-08-21T01:00:00+00:00https://www.misp-project.org/2020/08/22/MISP-Monitoring-with-Cacti.html/MISP - MISP service monitoring with Cacti2020-08-22T01:00:00+00:00MISP service monitoring with Cacti Introduction A previous post covered how to do MISP service monitoring with OpenNSM. Because having different options is good, this post covers how to achieve similar results with Cacti.2020-08-22T01:00:00+00:00https://www.misp-project.org/2020/09/08/MISP.2.4.131.released.html/MISP - MISP 2.4.131 released (improvements, bug fixes and major update to JavaScript dependencies)2020-09-08T01:00:00+00:00MISP 2.4.131 released A new version of MISP (2.4.131) has been released with improvements, bug fixes and a major update to JavaScript libraries.2020-09-08T01:00:00+00:00https://www.misp-project.org/2020/09/21/MISP.2.4.132.released.html/MISP - MISP 2.4.132 released (security fix CVE-2020-25766 and bugs fixed)2020-09-21T01:00:00+00:00MISP 2.4.132 released A new version of MISP (2.4.132) has been released with several bugs fixed including an important security fix CVE-2020-25766.2020-09-21T01:00:00+00:00https://www.misp-project.org/2020/09/30/How-To-Make-A-MISP-Import-Script.html/MISP - Create an import script for MISP , step-by-step tutorial2020-09-30T01:00:00+00:00Create an import script for MISP in Python, step-by-step tutorial Script description Example add_github_user.py Here the goal is to push to MISP information gathered on Github.2020-09-30T01:00:00+00:00https://www.misp-project.org/2020/10/08/Event-Reports.html/MISP - Event Report - A convenient mechanism to edit, visualize and share reports2020-10-08T01:00:00+00:00Event Report: A convenient mechanism to edit, visualize and share reports MISP is widely known as a powerful tool to gather, correlate and share information.2020-10-08T01:00:00+00:00https://www.misp-project.org/2020/10/16/MISP.2.4.133.released.html/MISP - MISP 2.4.133 released (major improvements such as the markdown report feature and many UI improvements)2020-10-16T01:00:00+00:00MISP 2.4.133 released with major improvements such as the markdown report feature and many UI improvements. Unstructured/semi-structured report feature MISP is widely known as a powerful tool to gather, correlate and share information.2020-10-16T01:00:00+00:00https://www.misp-project.org/2020/11/10/MISP.2.4.134.released.html/MISP - MISP 2.4.134 released (new import extractor for the event report, various improvements and fixes)2020-11-10T00:00:00+00:00MISP 2.4.134 released In the previous version of MISP, the new Event Report functionality has been introduced to edit, visualise and share reports in Markdown format, which includes the ability to reference elements from within a MISP event.2020-11-10T00:00:00+00:00https://www.misp-project.org/2020/12/16/MISP.2.4.135.released.html/MISP - MISP 2.4.135 released (galaxy 2.0)2020-12-16T00:00:00+00:00MISP 2.4.135 released Don’t let the minor version number change fool you, this release is a game changer for MISP and information sharing in general.2020-12-16T00:00:00+00:00https://www.misp-project.org/2021/01/18/MISP.2.4.136.released.html/MISP - MISP 2.4.136 released (Cerebrate project integration)2021-01-18T00:00:00+00:00MISP 2.4.136 released Though we’re rather late with the release notes, we did have some goodies to share for the winter festivities, bundled neatly into the 2.2021-01-18T00:00:00+00:00https://www.misp-project.org/2021/01/20/MISP.2.4.137.released.html/MISP - MISP 2.4.137 released (New exclusion module for the correlation engine, many improvements and security vulnerabilities resolved)2021-01-20T00:00:00+00:00MISP 2.4.137 released We have released 2.4.137, a security and bug fix release including a collection of fixes and improvements collected over the past month.2021-01-20T00:00:00+00:00https://www.misp-project.org/2021/02/10/MISP.2.4.138.released.html/MISP - MISP 2.4.138 released (Many improvements including CISA.gov AIS dynamic marking functionality, RSIT galaxy added)2021-02-10T00:00:00+00:00MISP 2.4.138 released We have released 2.4.138, the latest release for MISP along with an update of the JSON libraries.2021-02-10T00:00:00+00:00https://www.misp-project.org/2021/02/16/MISP.2.4.139.released.html/MISP - MISP 2.4.139 released (Quality of life and bugfix release)2021-02-16T00:00:00+00:00MISP 2.4.139 released We have released 2.4.139, the latest release for MISP squashes a set of pretty annoying bugs, whilst also adding some shiny new features to play with, along with the usual update of the JSON libraries.2021-02-16T00:00:00+00:00https://www.misp-project.org/2021/03/10/MISP.2.4.140.released.html/MISP - MISP 2.4.140 released (OpenID support, cross object references in extended events and many improvements)2021-03-10T00:00:00+00:00MISP 2.4.140 released We have released 2.4.140, the latest release for MISP, introducing a host of new features, including integrations with various authentication systems, various improvements to the handling of objects, CLI improvements as well as a package containing general bug fixes, along with the usual update of the JSON libraries.2021-03-10T00:00:00+00:00https://www.misp-project.org/2021/03/17/MISP-Objects-101.html/MISP - Creating a MISP Object, 1012021-03-17T00:00:00+00:00MISP Objects MISP objects are containers around contextually linked attributes. They support analysts in grouping related attributes and describing the relations that exist between the data points in a threat event.2021-03-17T00:00:00+00:00https://www.misp-project.org/2021/03/29/MISP.2.4.141.released.html/MISP - MISP 2.4.141 released (Many improvements from email notification, UI, API and installation scripts)2021-03-29T01:00:00+00:00MISP 2.4.141 released MISP 2.4.141 released including many improvements from email notification, UI, API and installation scripts.
User-Interface [UI] Render galaxy cluster description as markdown.2021-03-29T01:00:00+00:00https://www.misp-project.org/2021/04/27/MISP.2.4.142.released.html/MISP - MISP 2.4.142 released (with new correlation features, UI sync functionality improved and new dashboard widgets)2021-04-27T01:00:00+00:00MISP 2.4.142 released MISP 2.4.142 released including many new features, a security fix and a long list of quality of life improvements.2021-04-27T01:00:00+00:00https://www.misp-project.org/2021/05/15/MISP.2.4.143.released.html/MISP - MISP 2.4.143 released (10 year anniversary edition)2021-05-15T01:00:00+00:00MISP 2.4.143 released MISP 2.4.143 released including a new audit subsystem, various quality of life improvements and bug fixes.
10 year anniversary MISP has, as of the 15th of May, turned 10, to celebrate the occasion we have a celebratory MISP logo acting as a temporary replacement of the usual one for the duration of this release.2021-05-15T01:00:00+00:00https://www.misp-project.org/2021/06/07/MISP.2.4.144.released.html/MISP - MISP 2.4.144 released (Document all the things!)2021-06-07T01:00:00+00:00MISP 2.4.144 released MISP 2.4.144 released including a massive update to the documentation along with CyCAT.org integration, improvements and fixes including security related fixes.2021-06-07T01:00:00+00:00https://www.misp-project.org/2021/07/05/MISP.2.4.145-and-2.4.146.released.html/MISP - MISP 2.4.145 and 2.4.146 released (Improved warning-lists)2021-07-05T01:00:00+00:00MISP 2.4.145 and 2.4.146 released MISP 2.4.145 and 2.4.146 released including a massive update to the MISP warning-lists, various improvements and security fixes.2021-07-05T01:00:00+00:00https://www.misp-project.org/2016/10/07/MISP-2.4.52-released.html/MISP - MISP 2.4.52 released including new features and major improvements2016-10-07T01:00:00+00:00We are glad to announce MISP 2.4.52 including new features, improvements and bug fixes.
The following new features were introduced:2016-10-07T01:00:00+00:00https://www.misp-project.org/2021/08/09/MISP.2.4.148.released.html/MISP - MISP 2.4.148 released (summer time release)2021-08-09T01:00:00+00:00MISP 2.4.148 released MISP 2.4.148 released including many bugs fixed along with security fixes. This release fixes CVE-2021-37742 and CVE-2021-37743.2021-08-09T01:00:00+00:00https://www.misp-project.org/2021/10/11/MISP.2.4.149.released.html/MISP - MISP 2.4.149 released (Autumn care-package - STIX 2.1 support and Cerebrate integration)2021-10-11T01:00:00+00:00MISP 2.4.149 released MISP 2.4.149 released including many bugs fixed along with some new and improved functionalities
New features First stage of a massive rework of our STIX integration Various improvements to the integration with Cerebrate New STIX libraries The first version of a long ongoing project to rework our entire STIX integration has finally been merged, thanks to the tireless work of @chrisr3d Our converter libraries have embarked on a path of their own, becoming a standalone repository included by default in MISP, but also serving as a useful tool for anyone looking for a clean way of converting between the MISP standard format and various STIX versions (1.2021-10-11T01:00:00+00:00https://www.misp-project.org/2021/10/12/MISP.2.4.150.html/MISP - MISP 2.4.150 released (The "Bloody PKI again" hotfix release)2021-10-12T01:00:00+00:00MISP 2.4.150 released MISP 2.4.150 released, including a new CA bundle to combat the issues with the Letsencrypt root CA expiration.2021-10-12T01:00:00+00:00https://www.misp-project.org/2021/11/23/MISP.2.4.151.released.html/MISP - MISP 2.4.151 released (Black friday threat intel rush release)2021-11-23T00:00:00+00:00MISP 2.4.151 released MISP 2.4.151 released including a host of bug fixes and a bunch of new features
New features New background processor by @righel Improvements to the CLI tools Bug fixes and improvements New background processor MISP has been using CakeResque for its background jobs for the better part of a decade.2021-11-23T00:00:00+00:00https://www.misp-project.org/2021/12/22/MISP.2.4.152.released.html/MISP - MISP 2.4.152 released with timeline improvements, optional filtering on sync, LinOTP improvements and more.2021-12-22T00:00:00+00:00MISP 2.4.152 released MISP 2.4.152 released with timeline improvements, optional filtering on sync, LinOTP improvements and more.
The LinOTP authentication module has been improved to include a mixed mode where both OTP and MISP’s usual password authentication can be used together.2021-12-22T00:00:00+00:00https://www.misp-project.org/2021/12/22/MISP.2.4.152.releasedMISP - MISP 2.4.152 released with timeline improvements, optional filtering on sync, LinOTP improvements and more.2021-12-21T23:00:00+00:00<h1 id="misp-24152-released">MISP 2.4.152 released</h1>
<p>MISP 2.4.152 released with timeline improvements, optional filtering on sync, LinOTP improvements and more.</p>
<p>The LinOTP authentication module has been improved to include a mixed mode where both OTP and MISP’s usual password authentication can be used together.</p>
<p>The timelining has been improved in several ways, such as the inclusion of images from objects, as well as various improvements in the timeline’s sighting view. Several bugs were affecting this feature have also been fixed.</p>
<p>A new optional synchronisation filtering has been added to allow for the removal of specific attribute or object types when syncing. The functionality is meant to be used by the final recipient organisations of a synchronisation chain, in order to filter out specific types of information due to legal or specific internal policies. The filtering feature is disabled by default and needs to be enabled in the general configuration. This feature is for ISACs or consumer organisations, not redistributing information to other MISP communities.</p>
<p>A new STIX 1 and 2 export for attribute restSearch has been added in complement to the existing event export in STIX 1 and 2. The export works just like the other event level STIX export, all you need to do is specify the given STIX format as the return type when querying the attribute restSearch endpoint.</p>
<p>Many internal improvements and bugs fixed.</p>
<h1 id="misp-modules">MISP Modules</h1>
<ul>
<li>New <a href="https://misp.github.io/misp-modules/expansion/#qintel_qsentry">Qintel sentry module</a> added.</li>
<li><a href="https://circl.lu/services/hashlookup/">CIRCL hashlookup expansion</a> SHA-256 support added.</li>
</ul>
<p>The <a href="https://www.misp-project.org/Changelog-misp-modules.txt">MISP modules changelog is available</a>.</p>
<h1 id="misp-taxonomies">MISP Taxonomies</h1>
<ul>
<li>New <a href="https://www.misp-project.org/taxonomies.html#_political_spectrum">political spectrum taxonomy</a> added.</li>
<li>Improvement in exercise taxonomy.</li>
<li>New <a href="https://www.misp-project.org/taxonomies.html#_deception">deception taxonomy</a> added.</li>
</ul>
<p><a href="https://www.misp-project.org/Changelog-misp-taxonomies.txt">MISP Taxonomies changelog</a> is available.</p>
<h1 id="misp-galaxy">MISP Galaxy</h1>
<ul>
<li>New matrix <a href="https://www.misp-project.org/galaxy.html#_concordia_mobile_modelling_framework_attack_pattern">CONCORDIA Mobile Modelling Framework - Attack Pattern</a> added (thanks to <a href="https://www.concordia-h2020.eu/">Concordia H2020 project</a>).</li>
<li>Many update in threat actor, RAT and tools galaxy.</li>
</ul>
<p><a href="https://www.misp-project.org/Changelog-misp-galaxy.txt">MISP Galaxy changelog</a></p>
<h1 id="misp-objects">MISP Objects</h1>
<ul>
<li>New Concordia intrusion set object.</li>
<li>New temporal event object.</li>
<li>Many improvements in user, person, postal-address, email object.</li>
<li>New relationships added such as <code class="language-plaintext highlighter-rouge">found-in</code>, <code class="language-plaintext highlighter-rouge">works-with</code>, <code class="language-plaintext highlighter-rouge">drives</code>.</li>
</ul>
<p><a href="https://www.misp-project.org/Changelog-misp-objects.txt">MISP objects changelog</a></p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements in MISP core.</p>2021-12-21T23:00:00+00:00https://www.misp-project.org/2021/10/12/MISP.2.4.150MISP - MISP 2.4.150 released (The “Bloody PKI again” hotfix release)2021-10-11T23:00:00+00:00<h1 id="misp-24150-released">MISP 2.4.150 released</h1>
<p>MISP 2.4.150 released, including a new CA bundle to combat the issues with the Letsencrypt root CA expiration. This is a follow-up release to 2.4.149 and has no other major changes besides pointing to our own repository of the framework that includes the new CA bundle.</p>
<h1 id="sync-issues-due-to-the-expiration-of-a-letsencrypt-root-ca">Sync issues due to the expiration of a Letsencrypt root CA</h1>
<p>As described in their <a href="https://letsencrypt.org/docs/dst-root-ca-x3-expiration-september-2021/#:~:text=On%20September%2030%202021%2C%20there,accept%20your%20Let's%20Encrypt%20certificate">blog post</a>, Letsencrpyt had to retire an old Root CA, meaning that that SSL connections when synchronising MISP with other instances would fail if the remote side used letsencrypt. This update includes a new CA bundle that should help you avoid any issues with this.# Acknowledgement</p>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2021-10-11T23:00:00+00:00https://www.misp-project.org/2021/11/23/MISP.2.4.151.releasedMISP - MISP 2.4.151 released (Black friday threat intel rush release)2021-11-22T23:00:00+00:00<h1 id="misp-24151-released">MISP 2.4.151 released</h1>
<p>MISP 2.4.151 released including a host of bug fixes and a bunch of new features</p>
<h1 id="new-features">New features</h1>
<ul>
<li>New background processor by @righel</li>
<li>Improvements to the CLI tools</li>
<li>Bug fixes and improvements</li>
</ul>
<h1 id="new-background-processor">New background processor</h1>
<ul>
<li>MISP has been using CakeResque for its background jobs for the better part of a decade. Whilst it has served us well, the library has been stale for a long time and carries a (for us) unnecessary complexity and is generally the most difficult part of the application to debug</li>
<li>Luciano “@righel” Righetti has implemented a completely new, compatible background processing engine using Supervisord</li>
<li>Queue and execute jobs the same way as you are used to from before, monitor worker progress via the tools provided by supervisord in addition to MISP</li>
<li>No scheduling capabilities, these were an unnecessary overhead for us before as we relied on corn jobs as our preferred scheduling mechanism anyway</li>
<li>Expect more improvements to this library over the course of the next months, but feel free to switch to using it already now</li>
<li>Currently it is completely optional and the old background processor will still be supported for a while</li>
<li>Be aware that manual setup steps are required to get the new processor working, refer to <a href="https://gist.github.com/righel/8ebc6c84341f2aea7d0bfa124e535ef8">the upgrade guide</a> on the procedure, if you decide to start using it already now</li>
</ul>
<h1 id="various-cli-changes">Various CLI changes</h1>
<ul>
<li>Jakub Onderka has been doing a fair bit of refactoring and improvement of the CLI libraries</li>
<li>additional administrative tools added to help monitor and manage your MISP instance (such as redis memory diagnostics, mysql table optimisation tool, etc)</li>
</ul>
<h1 id="option-to-move-the-system-settings-to-the-database">Option to move the system settings to the database</h1>
<ul>
<li>Traditionally all system config settings were stored in the config.php file, with a new configuration thanks to Jakub Onderka’s implementation the settings can be moved to the database rather than the file.</li>
<li>This should help with persistence for containerised installations</li>
</ul>
<h1 id="various-improvements">Various improvements</h1>
<ul>
<li>The previous version introduced a new STIX library as a replacement for the old one. This change did end up causing some update issues for some installations, the built in updater is now aware of this change and should allow you to easily update via the UI/API updater, with the new STIX library working as intended</li>
<li>A long list of improvements, thanks to all contributors! For a detailed list of changes, head over to the <a href="https://www.misp-project.org/Changelog.txt">changelog</a></li>
</ul>
<h1 id="misp-modules">MISP Modules</h1>
<ul>
<li>New <a href="https://github.com/D4-project/passive-ssh">Passive SSH expansion</a> expansion module.</li>
<li>Updated <a href="https://misp.github.io/misp-modules/expansion/#recordedfuture">Recorded Future</a> expansion module included links and related data.</li>
<li>New <a href="https://circl.lu/services/hashlookup/">CIRCL hashlookup expansion</a> module added.</li>
</ul>
<p>The <a href="https://www.misp-project.org/Changelog-misp-modules.txt">MISP modules changelog is available</a>.</p>
<h1 id="misp-taxonomies">MISP Taxonomies</h1>
<ul>
<li>Updated taxonomies for <a href="https://www.misp-project.org/taxonomies.html#_interactive_cyber_training_audience">Interactive Cyber Training setup and environment</a>.</li>
<li>Updated <a href="https://www.misp-project.org/taxonomies.html#_fr_classif">fr-classification</a> to match IGI1300.</li>
</ul>
<p><a href="https://www.misp-project.org/Changelog-misp-taxonomies.txt">MISP Taxonomies changelog</a> is available.</p>
<h1 id="misp-galaxy">MISP Galaxy</h1>
<ul>
<li>Updated to MITRE ATT&CK version 10.</li>
<li>Multiple updates in malpedia, threat actor galaxy and Office 365 techniques.</li>
</ul>
<p><a href="https://www.misp-project.org/Changelog-misp-galaxy.txt">MISP Galaxy changelog</a></p>
<h1 id="misp-objects">MISP Objects</h1>
<ul>
<li>New JA3 server object added.</li>
<li>New Security playbook object added.</li>
<li>New submarine object added</li>
<li>New Passive SSH object added.</li>
<li>Updated device object.</li>
<li>New hashlookup object added.</li>
<li>New edr-report object added.</li>
</ul>
<p><a href="https://www.misp-project.org/Changelog-misp-objects.txt">MISP objects changelog</a></p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2021-11-22T23:00:00+00:00https://www.misp-project.org/2021/10/11/MISP.2.4.149.releasedMISP - MISP 2.4.149 released (Autumn care-package - STIX 2.1 support and Cerebrate integration)2021-10-10T23:00:00+00:00<h1 id="misp-24149-released">MISP 2.4.149 released</h1>
<p>MISP 2.4.149 released including many bugs fixed along with some new and improved functionalities</p>
<h1 id="new-features">New features</h1>
<ul>
<li>First stage of a massive rework of our STIX integration</li>
<li>Various improvements to the integration with Cerebrate</li>
</ul>
<h1 id="new-stix-libraries">New STIX libraries</h1>
<ul>
<li>The first version of a long ongoing project to rework our entire STIX integration has finally been merged, thanks to the tireless work of @chrisr3d</li>
<li>Our converter libraries have embarked on a path of their own, becoming a standalone repository included by default in MISP, but also serving as a useful tool for anyone looking for a clean way of converting between the <a href="https://www.misp-standard.org/">MISP standard format</a> and various STIX versions (1.1.1, 1.2, 2.0, 2.1).</li>
<li>The libraries are still work in progress, but continuously improved, follow <a href="https://github.com/MISP/misp-stix">misp-stix</a></li>
<li>Included is also a detailed documentation, which also serves as a knowledge base for the mapping between the two formats, available under the <a href="https://github.com/MISP/misp-stix/tree/main/documentation">documentation</a> sub-directory</li>
<li>From this release on, you have more control over which STIX version is used when exporting STIX data from MISP, by specifying the “stix_version” to be returned (supported versions for STIX 1: 1.1.1 and 1.2. For STIX 2: 2.0 and 2.1)</li>
</ul>
<h1 id="cerebrate-integration">Cerebrate integration</h1>
<ul>
<li>Allow the fetching of sharing group data from Cerebrate instances, our new open source tool in development aiming to solve a host of issues revolving around community management and orchestration. Our first official release of the tool is scheduled for the MISP summit coming up this month</li>
<li>To follow the cerebrate project, head over to its <a href="https://github.com/cerebrate-project/cerebrate">github page</a></li>
<li>For the MISP summit to be held on the 21st of October, don’t forget to watch the <a href="https://www.misp-project.org/misp-summit">misp-summit</a>. You can still apply for the <a href="https://cfp.hack.lu/misp-2021/cfp">Call-for-Presentation</a>.</li>
</ul>
<h1 id="mail2misp-release-10">mail2misp release 1.0</h1>
<p>First <a href="https://github.com/MISP/mail_to_misp/releases/tag/v1.0">official release 1.0 of mail2misp</a>, it’s a tool to connect your mail infrastructure to MISP to create events based on the information contained within mail. The solution can be also used to feed MISP instance with honeypot receiving emails.</p>
<h1 id="various-improvements">Various improvements</h1>
<ul>
<li>A long list of improvements, massive thanks to @JakubOnderka for the continuous stream of improvements and quality of life changes</li>
<li>Thanks to the work of @righel, our <a href="https://www.misp-project.org/documentation/openapi.html">OpenAPI documentation</a> is becoming more and more complete, now covering a long list of the more exotic endpoints and options</li>
</ul>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2021-10-10T23:00:00+00:00https://www.misp-project.org/2021/08/09/MISP.2.4.148.releasedMISP - MISP 2.4.148 released (summer time release)2021-08-08T23:00:00+00:00<h1 id="misp-24148-released">MISP 2.4.148 released</h1>
<p>MISP 2.4.148 released including many bugs fixed along with security fixes. This release fixes <a href="https://cvepremium.circl.lu/cve/CVE-2021-37742">CVE-2021-37742</a> and <a href="https://cvepremium.circl.lu/cve/CVE-2021-37743">CVE-2021-37743</a>.</p>
<h1 id="new-feature">New feature</h1>
<ul>
<li>added option to block organisation changes at login on ApacheShibbAuth</li>
<li>Open data export has been refactored</li>
<li>Fix Suricata export concerning sticky buffers</li>
<li>ZMQ now includes misp_json_warninglist topic in the pub-sub channels</li>
</ul>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2021-08-08T23:00:00+00:00https://www.misp-project.org/2021/07/27/MISP.2.4.147.released.html/MISP - MISP 2.4.147 released (improvements and bug fixes release)2021-07-27T01:00:00+00:00MISP 2.4.147 released MISP 2.4.147 released including a massive number of small improvements, bug and security fixes. We strongly recommend all MISP users to upgrade as soon as possible.2021-07-27T01:00:00+00:00https://www.misp-project.org/2021/07/27/MISP.2.4.147.releasedMISP - MISP 2.4.147 released (improvements and bug fixes release)2021-07-26T23:00:00+00:00<h1 id="misp-24147-released">MISP 2.4.147 released</h1>
<p>MISP 2.4.147 released including a massive number of small improvements, bug and security fixes. We strongly recommend all MISP users to upgrade as soon as possible. This release fixes <a href="https://cvepremium.circl.lu/cve/CVE-2021-37534">CVE-2021-37534</a>.</p>
<h1 id="sync-improvements">Sync improvements</h1>
<p>Many improvements were done in the synchronisation such as:</p>
<ul>
<li>When saving sightings, only push the new sightings.</li>
<li>Filter out existing sightings if remote sever supports that method.</li>
<li>Check if event exists before pushing.</li>
<li>Check event existence before pushing sightings.</li>
<li>Optimise event filtering.</li>
</ul>
<h1 id="apicli">API/CLI</h1>
<p>Many improvements in the API and CLI.</p>
<p>This release also includes refactoring of various forms to support future major improvements in MISP.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2021-07-26T23:00:00+00:00https://www.misp-project.org/2021/07/05/MISP.2.4.145-and-2.4.146.releasedMISP - MISP 2.4.145 and 2.4.146 released (Improved warning-lists)2021-07-04T23:00:00+00:00<h1 id="misp-24145-and-24146-released">MISP 2.4.145 and 2.4.146 released</h1>
<p>MISP 2.4.145 and 2.4.146 released including a massive update to the MISP warning-lists, various improvements and security fixes.</p>
<h1 id="misp-warning-lists-improvements">MISP warning-lists improvements.</h1>
<p><a href="https://github.com/misp/misp-warninglists">Warning lists</a> system has been significantly improved (thanks to Jakub Onderka).</p>
<ul>
<li>Custom warning lists can be created and managed in the MISP user-interface</li>
<li>Warning lists can be now imported via the API</li>
<li>Warning lists changes are exported in the ZMQ channel</li>
<li>Warning lists include new categories to describe the scope</li>
</ul>
<h1 id="new-features">New features</h1>
<h2 id="summary-email-notification">Summary email notification</h2>
<p>Email notifications have received a new configuration setting: New event summaries only.
This feature publishes the normal alert reports excluding attributes and objects, thereby
only describing a summary of the alert. This can be used when encryption cannot be enabled
and organisations still require email alerting.</p>
<h2 id="documentation">Documentation</h2>
<p>New documentation has been added to describe the <a href="https://raw.githubusercontent.com/MISP/MISP/2.4/docs/generic/Authentication%20Diagram/MISP%20Authentication%20Diagram.png">session and cookie handling in MISP</a>.</p>
<h2 id="api">API</h2>
<ul>
<li>Thanks to a new feature, you can now create read only authentication keys (don’t forget to enable the advanced authentication key feature for this to work).</li>
</ul>
<h1 id="security-fixes">Security Fixes</h1>
<ul>
<li>Various fixes regarding XSS and potential escaping issues including <a href="https://cvepremium.circl.lu/cve/CVE-2021-35502">CVE-2021-35502</a>.</li>
</ul>
<p>Thanks to the reporters including Nicolas Vidal from TEHTRIS.</p>
<h1 id="various-improvements">Various improvements</h1>
<ul>
<li>[OpenAPI] - Missing return formats added to the documentation</li>
<li>[server caching] only push data to redis / logs if there’s something to push</li>
<li>[attribute] validation tightened for empty strings. A value containing only control characters will now be blocked from entry.</li>
<li>[feeds] Added 3 daily feeds (ssh bruteforce, telnet bruteforce, URLs seen) from the APNIC Community Honeynet Project</li>
</ul>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2021-07-04T23:00:00+00:00https://www.misp-project.org/2021/06/07/MISP.2.4.144.releasedMISP - MISP 2.4.144 released (Document all the things!)2021-06-06T23:00:00+00:00<h1 id="misp-24144-released">MISP 2.4.144 released</h1>
<p>MISP 2.4.144 released including a massive update to the documentation along with <a href="https://www.cycat.org/">CyCAT.org</a> integration, improvements and fixes including security related fixes.</p>
<h1 id="openapi-integration">OpenAPI integration</h1>
<p>We have a new core team member at MISP Project, Luciano (@righel), who kicked off his tenure with an impressive mapping of all the most important endpoints of MISP to OpenAPI. As of this release, the API documentation is directly available in MISP, along with example payloads and responses. You can also find <a href="https://www.misp-project.org/documentation/openapi.html">this information directly on the misp-project website</a>. To all integrators and developers wrangling with the API, we highly recommend you take a look at the API menu in MISP and we wish you happy and headache-free hacking!</p>
<h1 id="new-diagrams-and-descriptions">New diagrams and descriptions</h1>
<p>Thanks to the thorough investigations of @mokaddem, we now have the entire synchronisation and authentication flows of MISP mapped in an easy to understand graph - both of these are included as of now directly in your MISP installation, so if you’re in doubt about what’s going on under the hood, but don’t feel adventurous enough to replace your night time reading materials with a hefty chunk of PHP code, have a look at the new graphs!</p>
<ul>
<li><a href="https://github.com/MISP/MISP/tree/2.4/docs/generic/Authentication%20Diagram">Authentication Diagram</a></li>
<li><a href="https://github.com/MISP/MISP/tree/2.4/docs/generic/Synchronisation">Data visibility for Sync-users and MISP synchronisation</a></li>
</ul>
<h1 id="cycat-integration-v1">CyCAT integration v1</h1>
<p><img src="https://www.misp-project.org/assets/images/misp/blog/cycat-misp.png" alt="MISP and CyCAT integration" /></p>
<p>CyCAT is a new initiative built by a group of individuals with the aim of cataloguing all the techniques and libraries around cyber-security, mostly with the selfish desire to make their own confusing lives easier (along with all those that are in a similar situation). As of this release, you’ll be able to enable a first version of the CyCAT integration in MISP directly, allowing you to directly see relations to your galaxy clusters via CyCAT’s own relationship system, giving you an extra layer of background information with the clusters already in use.</p>
<p>If you are interested in CyCAT and what it can do for you, head over to the <a href="https://cycat.org/">CyCAT website</a>.</p>
<p>To enable the CyCAT integration, got to the Plugin settings <img src="https://www.misp-project.org/assets/images/misp/blog/cycat-enabled.png" alt="" /> and enable the feature.</p>
<h1 id="improvements">Improvements</h1>
<ul>
<li>Various quality of life improvements and bug fixes, related to synchronisation, sharing groups, event reports and more!</li>
<li>A security fix that would under certain circumstances result in attributes of an object being misassociated to the wrong sharing group after synchronisation. A massive thank you to Jeroen Pinoy for his diligent work in uncovering this issue!</li>
</ul>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2021-06-06T23:00:00+00:00https://www.misp-project.org/2021/05/15/MISP.2.4.143.releasedMISP - MISP 2.4.143 released (10 year anniversary edition)2021-05-14T23:00:00+00:00<h1 id="misp-24143-released">MISP 2.4.143 released</h1>
<p>MISP 2.4.143 released including a new audit subsystem, various quality of life improvements and bug fixes.</p>
<h1 id="10-year-anniversary">10 year anniversary</h1>
<p><a href="https://twitter.com/MISPProject/status/1393141380369821697">MISP has, as of the 15th of May, turned 10,</a> to celebrate the occasion we have a celebratory MISP logo acting as a temporary replacement of the usual one for the duration of this release.</p>
<p>It has been a long road since Christophe Vandeplas released the initial version of CyDefsig (later renamed to MISP) in 2011. We would hereby like to thank all contributors and supporters for making MISP what it is today. Looking back at how the tooling and the communities evolved over the decade, we can see how threats and threat intelligence has changed and evolved over the years, molding the platform in the process. Here’s to at least another 10 years of active sharing and bringing communities together!</p>
<h1 id="new-audit-system">New audit system</h1>
<p>Thanks to @JakubOnderka, we now have a whole new audit system, storing relevant audit logs in a more concise yet easily machine-parsable way (all changes will be logged as JSON objects). This feature is disabled by default and needs to be enabled in the server settings, though keep in mind that it will not convert existing entries. Especially for new instances, we highly recommend switching to the new system!</p>
<h1 id="event-republish-alert-flood-protection">Event republish-alert flood protection</h1>
<p>As our communities grow and we all build our own internal tooling for processing data in MISP, the more likely it is to run into some slightly frustrating issues. One such issue we’ve encountered recently came from a tool that seems to have regularly (and frequently!) modified certain events and republished them consecutively. This in itself is not an issue, however, it can generate a lot of noise in terms of alert emails. We have now added a protective measure to counter this, make sure you have a look at the appropriate settings to create lockout timers for alerts that can be issued for a single event.</p>
<h1 id="improvements">Improvements</h1>
<ul>
<li>Event report hints autocomplete while typing in the Markdown has been improved</li>
<li>Server rules element improved</li>
<li>MISP modules results now point to the original object itself</li>
</ul>
<h1 id="misp-modules">MISP Modules</h1>
<p>Two new MISP modules were introduced:</p>
<ul>
<li>cof2misp module to allow the import of Passive DNS in <a href="https://tools.ietf.org/id/draft-dulaunoy-dnsop-passive-dns-cof-08.html">JSON COF Format</a> into MISP</li>
<li>An improved <a href="https://github.com/MISP/misp-modules/blob/main/misp_modules/modules/expansion/onyphe.py">onyphe module</a> to do expansion in MISP with full MISP object support</li>
</ul>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2021-05-14T23:00:00+00:00https://www.misp-project.org/2021/04/27/MISP.2.4.142.releasedMISP - MISP 2.4.142 released (with new correlation features, UI sync functionality improved and new dashboard widgets)2021-04-26T23:00:00+00:00<h1 id="misp-24142-released">MISP 2.4.142 released</h1>
<p>MISP 2.4.142 released including many new features, a security fix and a long list of quality of life improvements.</p>
<h1 id="correlation-changes">Correlation changes</h1>
<p>One of the most annoying bottlenecks in how we use MISP currently is caused by low quality correlations, both in terms of usability and having a clear view on relevant relationships among data-points. These very often come from either sub-optimal strategies chosen on data creation/ingestion for certain types of attributes, but very often also on edge cases.</p>
<p>With the current release we’ve included two main tools to combat this:</p>
<h3 id="correlation-exclusions">Correlation exclusions</h3>
<p>We can now remove individual values from ever correlating again, so if you come across some typical noisy values (such as empty file hashes, registry values of 000000, internal IPs recurrinly encoded by your sandbox), you can add those to the exclusion list.</p>
<p>Once added, you can execute the cleaning of the existing correlations, to retroactively execute your exclusion rules. This is a background processed task and depending on the amount of correlations you have may take quite some time (it took us around 30 minutes on 25M correlations), so just fire it off and check back later whether the job has completed.</p>
<p>You can also comment your reason for removing an entry. In the future we plan on publishing community maintained default exclusion lists.</p>
<p><img src="https://www.misp-project.org/assets/images/misp/blog/correlation-exclusion.png" alt="Correlation exclusion in MISP" /></p>
<h3 id="top-correlations">Top correlations</h3>
<p>List the most correlating values in your instance - in order to evaluate which the most problematic correlations are, simply have a look at the most noisy correlations. We’ve had some surprising entries in our communities, so perfect time to do some spring cleaning.</p>
<p>Just hit the delete button on a correlation and it will add a rule to your correlation exclusion list - just don’t forget to run the historic cleanup from the correlation exclusion index to remove already existing correlations matching your newly added rules.</p>
<h1 id="server-sync-rule-management-rework">Server sync rule management rework</h1>
<p><img src="https://www.misp-project.org/assets/images/misp/blog/pull-rules.png" alt="MISP server sync rule management" /></p>
<p>One of the more painful aspects of managing servers has been the historically bad UI used to manage filter rules. This has now been completely revamped, both with a new look but familiar look and feel as well as some clever new tools to make it more usable.</p>
<p>For example, when creating pull filters, your instance will now attempt to contact the remote instance to retrieve a list of available tags, so that you no longer have to manually enter all of the filters when creating pull rules. The JSON rule field allowing custom filters now also uses a handy JSON parsing text entry, allowing you to avoid potential mistakes.</p>
<h1 id="new-dashboard-widgets">New dashboard widgets</h1>
<p>Thanks to Jeroen Pinoy, we have some new dashboard widgets meant to give you better oversight over how your instance is being used, showing some usage statistics as well as tools to monitor the growth of the user base of the community.</p>
<p><img src="https://www.misp-project.org/assets/images/misp/blog/evolution-usercount.png" alt="" /></p>
<h1 id="a-bunch-of-other-fixes-including-security-fixes">A bunch of other fixes including security fixes</h1>
<p>We have also a <a href="https://www.misp-project.org/security/">security</a> issue (CVE-2021-31780) causing a potential misalignment of sharing groups on synced attributes, so we highly encourage everyone to update their MISP instance.</p>
<p>Besides that we have introduced a long list of quality of life improvements as well as <a href="https://www.misp-project.org/Changelog.txt">many fixes</a>.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
. The MISP galaxy includes a major update in the Ransomware galaxy which now includes more than 1600 documented ransomware.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2021-04-26T23:00:00+00:00https://www.misp-project.org/2021/03/29/MISP.2.4.141.releasedMISP - MISP 2.4.141 released (Many improvements from email notification, UI, API and installation scripts)2021-03-28T23:00:00+00:00<h1 id="misp-24141-released">MISP 2.4.141 released</h1>
<p>MISP 2.4.141 released including many improvements from email notification, UI, API and installation scripts.</p>
<h1 id="user-interface">User-Interface</h1>
<ul>
<li>[UI] Render galaxy cluster description as markdown.</li>
<li>[UI] Show threat level icons on event index.</li>
<li>[eventgraph:viewPicture] Allow access to saved picture from the eventgraph history.</li>
<li>[eventGraph] Improved object coloring strategy.</li>
<li>[UI] fix debugon for debug = 1. fix #7131.</li>
<li>[UI] Show number of items in freetext feed.</li>
<li>[UI] Make feed event preview nicer.</li>
<li>[UI] It is 2021! Removed -moz and -webkit specific CSS properties.</li>
<li>[UI] Make some parts of MISP nicer.</li>
<li>[UI] Nicer pivots.</li>
<li>[UI] Simplify keyboard-shortcuts.js.</li>
<li>[UI] Use Page Visibility API.</li>
</ul>
<p>and many more updates check the <a href="https://www.misp-project.org/Changelog.txt">changelog for details</a>.</p>
<h1 id="email-notification">Email notification</h1>
<p>Email notification has been significantly improved and now support HTML emails.</p>
<ul>
<li>[email] New setting <code class="highlighter-rouge">MISP.event_alert_metadata_only</code>.</li>
<li>[email] Command for testing generated alert email.</li>
<li>[email] Allow to set email subject from template.</li>
<li>[email] Back-end support for sending HTML emails.</li>
</ul>
<p>This release includes many updates in the local and translation of the user-interface.</p>
<p>New default feeds were included in MISP such as the newest <a href="dataplane.org">DataPlane.org feeds</a>.</p>
<h1 id="installation-scripts-and-guides">Installation scripts and guides</h1>
<p>Many improvement in the RHEL7, 7.9 and CentOS8Stream. We thank all the users reporting issues with RHEL.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2021-03-28T23:00:00+00:00http://blog.thehive-project.org/?p=6033MISP - TheHive Reloaded: 4.1.0 is out2021-03-19T16:38:11+00:00We are proud and excited to annonce the availability of TheHive v4.1.0. This release is the new beginning of TheHive’s future, because all the upcoming features and enhancements will be based on this version, without the brakes. 4.1.0 is out after a significant work done during the last 6 months, interrupted by multiple events like: … <a href="https://blog.thehive-project.org/2021/03/19/thehive-reloaded-4-1-0-is-out/" class="more-link">Continue reading <span class="screen-reader-text">TheHive Reloaded: 4.1.0 is out</span> <span class="meta-nav">→</span></a>2021-03-19T16:38:11+00:00https://www.misp-project.org/2021/03/17/MISP-Objects-101MISP - Creating a MISP Object, 1012021-03-16T23:00:00+00:00<h2 id="misp-objects">MISP Objects</h2>
<p>MISP objects are containers around <strong>contextually linked</strong> attributes. They support analysts in grouping related attributes and describing the relations that exist between the data points in a threat event. Combining these objects and relations is something that can then be used to represent the story of what is being told in the threat event.</p>
<p>MISP supports a large list of objects such as</p>
<ul>
<li>AV-signature: an antivirus detection signature</li>
<li>Domain/IP: document a tuple domain, hostname and IP address</li>
<li>File: describing a file with meta information</li>
<li>Organization: an object to describe an organization</li>
</ul>
<p>All these objects are available via the <a href="https://github.com/MISP/misp-objects">MISP-Objects Github repository</a> and directly accessible within <a href="https://github.com/MISP/MISP">MISP</a>. Despite the large list of already available objects it’s always possible that these do not fully address your need.</p>
<p>So how to add your own objects?</p>
<h2 id="concepts">Concepts</h2>
<p>First some basic concepts</p>
<ul>
<li>To maintain uniformity, objects are described in a <strong>MISP object template format</strong>. So in order to add an object, you essentially need to add an object template file.</li>
<li>The MISP object template format uses <strong>JSON</strong> and is described in a <a href="https://www.misp-standard.org/rfc/misp-standard-object-template-format.txt">standard format</a>.</li>
<li>An object template contains a header section with <strong>meta information</strong> and then a <strong>list of attributes</strong>.</li>
<li>Relations between objects are not part of the object template.</li>
</ul>
<p>MISP objects are stored in the file location <code class="highlighter-rouge">/var/www/MISP/app/files/misp-objects/objects</code> (provided MISP is installed in a default location). Each object is stored in a separate directory and described in a template file called <code class="highlighter-rouge">definition.json</code>. As an example,</p>
<ul>
<li>The object <strong>domain-ip</strong> is stored in the directory <code class="highlighter-rouge">/var/www/MISP/app/files/misp-objects/objects/domain-ip/</code></li>
<li>This object is described in the file <code class="highlighter-rouge">definition.json</code> stored in that directory</li>
</ul>
<h2 id="demo">Demo</h2>
<p>In this demo I’ll explain how to add your own <strong>custom MISP object</strong> and make it available in the MISP interface. The easiest approach is to start from an already existing template but in order to have a good understanding of the object template format file let’s start an object template from scratch.</p>
<p>The demo object that we’ll create covers an internal corporate asset.</p>
<h3 id="object-template-file">Object template file</h3>
<h4 id="valid-json">Valid JSON</h4>
<p>An object template file needs to be a <strong>valid JSON</strong> file. If your template file is not valid JSON it will not be possible to use it within MISP. The error messages from MISP will not always indicate that there’s a problem with the JSON file format. The best advice is to use your editor to validate the JSON file or use an external resource such as <a href="https://jsonlint.com/">JSONLint</a>.</p>
<h4 id="directory-and-file">Directory and file</h4>
<p>The first step in creating the new object is creating a new directory in the objects directory and then add an empty file in this directory. After creating this directory and file we need to make sure that the file is readable by the web user.</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>mkdir /var/www/MISP/app/files/misp-objects/objects/demo-template/
touch /var/www/MISP/app/files/misp-objects/objects/demo-template/definition.json
chown -R www-data:www-data /var/www/MISP/app/files/misp-objects/objects/demo-template/
</code></pre></div></div>
<h3 id="object-template-header">Object template header</h3>
<p>Now open the template definition file (<code class="highlighter-rouge">definition.json</code>) and add a header which will contain the meta information. This includes</p>
<ul>
<li>A unique ID (<strong>uuid</strong>). You can generate such an UUID online via <a href="https://www.uuidgenerator.net/version4">UUIDGenerator</a> or on the command line with <code class="highlighter-rouge">uuidgen</code>.</li>
<li>A <strong>description</strong> and a <strong>name</strong> for your new object. These are human-readable strings describing the object.</li>
<li>A <strong>version</strong> number which is a numeric incrementing version of the object template. Whenever you update the object template, you have to increment the version.</li>
<li>A <strong>meta-category</strong> which represents the sub-category of objects that the object template belongs to. This meta-category is a string and is not tied to a fixed list. Example of meta-categories in the current objects include climate, file, financial, followthemoney, health, iot, misc, network and vulnerability.</li>
</ul>
<p>Apart from his meta information, the object template file also contains the rules, or requirements that apply to this object. These rules describe which attributes need to be part of the object to have a valid object.</p>
<ul>
<li><strong>Required</strong>, a JSON list with all the required attributes.</li>
<li><strong>requiredOneOf</strong>, a JSON list of attributes of which there needs to be at least one present.</li>
</ul>
<p>To summarize this, the below section of the object template file describes our header. This concerns an object <code class="highlighter-rouge">corporate-asset</code> with two required attributes, asset-type and asset-id.</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code> "description": "Corporate asset",
"meta-category": "misc",
"name": "corporate-asset",
"required": [
"asset-type",
"asset-id"
],
"uuid": "1a99327a-bbe6-493d-97da-fce83965eccd",
"version": 20210317
</code></pre></div></div>
<h3 id="object-template-attributes">Object template attributes</h3>
<p>Now that we’ve added our header, it’s time to add the list of attributes that we want to include in the object. These attributes are in a JSON list (called <strong>attributes</strong>) and are essentially a list of elements that under the hood reference MISP attributes.</p>
<p>How do you describe these individual attributes? Each attribute is referenced by an attribute name, which in turn contains a JSON list with these values</p>
<ul>
<li>A <strong>description</strong> which is the description of the given attribute in the context of the object.</li>
<li>The <strong>misp-attribute</strong> to which this attribute can be mapped. Note that in a lot of circumstances you might just want to link to the MISP attribute ‘text’.</li>
</ul>
<p>Apart from these values, there are some optional, but still interesting, values to include.</p>
<ul>
<li>The <strong>ui-priority</strong>, a numeric value to provide a priority in the object template visualisation.</li>
<li>An indication if you want to <strong>disable_correlation</strong> on the attribute.</li>
<li>Whether you allow <strong>multiple</strong> instances of the attribute to be present.</li>
<li>A list of predefined <strong>values_list</strong> from which the user has to choose.</li>
</ul>
<p>If we now convert this in a practical example we can list the attributes of this object as follows</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code> "attributes": {
"asset-type": {
"description": "Type of asset",
"disable_correlation": true,
"misp-attribute": "text",
"ui-priority": 3,
"values_list": [
"Server",
"Workstation",
"Printer",
"Network",
"Mobile",
"Monitor"
]
},
"asset-id": {
"description": "Asset identification",
"disable_correlation": true,
"misp-attribute": "target-machine",
"ui-priority": 0
},
"business-unit": {
"description": "Organizational business unit associated with the asset",
"disable_correlation": true,
"misp-attribute": "target-org",
"ui-priority": 2
},
"text": {
"description": "A description of the asset.",
"disable_correlation": true,
"misp-attribute": "text",
"ui-priority": 1
}
}
</code></pre></div></div>
<p>In this example we have two attributes in the object model which are built on top of the MISP attribute type ‘text’, one attribute on ‘target-machine’ and one attribute on ‘target-org’. The user is forced to do a selection from the supplied value list in asset-type.</p>
<h4 id="merge-file">Merge file</h4>
<p>Now it’s a matter of merging the object template file header with the list of attributes, resulting in the below result</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>{
"description": "Corporate asset",
"meta-category": "misc",
"name": "corporate-asset",
"required": [
"asset-type",
"asset-id"
],
"uuid": "1a99327a-bbe6-493d-97da-fce83965eccd",
"version": 20210317,
"attributes": {
"asset-type": {
"description": "Type of asset",
"disable_correlation": true,
"misp-attribute": "text",
"ui-priority": 3,
"values_list": [
"Server",
"Workstation",
"Printer",
"Network",
"Mobile",
"Monitor"
]
},
"asset-id": {
"description": "Asset identification",
"disable_correlation": true,
"misp-attribute": "target-machine",
"ui-priority": 0
},
"business-unit": {
"description": "Organizational business unit associated with the asset",
"disable_correlation": true,
"misp-attribute": "target-org",
"ui-priority": 2
},
"text": {
"description": "A description of the asset.",
"disable_correlation": true,
"misp-attribute": "text",
"ui-priority": 1
}
}
}
</code></pre></div></div>
<h3 id="update-misp">Update MISP</h3>
<p>We’re not done yet. We have created the new object but MISP is not yet aware of this new file. To make the new object available in the MISP interface we have to update our object definitions. To do so go to <strong>Global Actions</strong>, <strong>List Object Templates</strong> and then on the left of the screen select <strong>Update objects</strong>. This instructs MISP to scan the local file system for changes and import the new files, provided they fit the correct format.</p>
<p><img src="/assets/images/object101/object-templates2.jpg" alt="Objects update" /></p>
<p>If the import was successful, you can also review the object template definition via the MISP user interface.</p>
<p><img src="/assets/images/object101/object-templates3.jpg" alt="Objects detailed" /></p>
<h2 id="relations">Relations</h2>
<p>The MISP object model is open and allows user to use their own relationships. MISP provides a list of default relationships that can be used if you plan to share your events with other MISP communities. These relationships are defined in the file <code class="highlighter-rouge">/var/www/MISP/app/files/misp-objects/relationships/definition.json</code></p>
<h2 id="validation">Validation</h2>
<p>When you’re done with creating the object you can run validation scripts from within the MISP objects dirctory before doing a pull request.</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>./jq_all_the_things.sh
./validate_all.sh
</code></pre></div></div>
<p>If all looks good, you can do a pull request to make sure your object (and/or relation) is made available to the community.</p>2021-03-16T23:00:00+00:00https://www.misp-project.org/2021/03/10/MISP.2.4.140.releasedMISP - MISP 2.4.140 released (OpenID support, cross object references in extended events and many improvements)2021-03-09T23:00:00+00:00<h1 id="misp-24140-released">MISP 2.4.140 released</h1>
<p>We have released 2.4.140, the latest release for MISP, introducing a host of new features, including integrations with various authentication systems, various improvements to the handling of objects, CLI improvements as well as a package containing general bug fixes, along with the usual update of the JSON libraries.</p>
<h1 id="manage-my-identity">Manage my identity!</h1>
<p>MISP already had a host of integration options with various IDPs, but this release will give you some additional options, in the shape of <a href="https://github.com/MISP/MISP/tree/2.4/app/Plugin/OidcAuth">OpenID Connect authentication</a> and <a href="https://github.com/MISP/MISP/tree/2.4/app/Plugin/AadAuth">Azure Active Directory Authentication</a> integrations. Have a look at the various authentication plugins’ configuration in the MISP/app/Plugin directory.</p>
<h1 id="built-in-security-report-of-your-misp-instance">Built in security report of your MISP instance</h1>
<p>As of this release, you can get some guidance on the security posture and potential security impacting misconfigurations and best practices via the new security audit tool, locate in the diagnostics section of the server settings. Make sure you go through the tools findings and make any changes you find appropriate from the suggestions offered. When in doubt, feel free to start a discussion on the <a href="https://gitter.im/MISP/Support">support chat</a> hosted on gitter.</p>
<p>The audit also gives you a sanity check over your CSP posture, used in junction with the new settings and tightened security measures.</p>
<p>Massive kudos to @JakubOnderka for all this work!</p>
<h1 id="cross-referencing-objects-across-extended-events">Cross referencing objects across extended events</h1>
<p>Whilst extended events were the most flexible way of creating counter analyses in MISP as well as being able to provide additional information to a report, we were always lacking a crucial component to make this feature truly shine: The ability to build connected graphs of the data points contained in a set of events extending one another. This has now been added to MISP as of 2.4.140.</p>
<h1 id="cli-improvements">CLI improvements</h1>
<p>We want to make scripting and using the CLI in general a bit more straight-forward. Since the phasing out of the build in task scheduler, we find that there has been a massive uptick in the usage of these tools so expect more improvements in the future. For now, we have added tools to list the connect servers directly from the CLI, to be able to automate the sync process per connected server.</p>
<p>Additionally, a new set of CLI tools is being built for developers, to ease our lives when trying to modify MISP. The first tool for this toolkit allows us to massage the direct feed description dumps to the expected format for easier modification.</p>
<h1 id="new-types-added-in-misp">New types added in MISP</h1>
<p>New full-name, dkim and dkim-signature attribute types were added to MISP. Associated to <a href="https://www.misp-project.org/objects.html#_dkim">DKIM objects</a> were included to support tools such as Farsight Security dnsdb to add DKIM information in your investigations.</p>
<h1 id="security-vulnerability">Security Vulnerability</h1>
<p>An issue was discovered in app/Model/SharingGroupServer.php in MISP 2.4.139. In the implementation of Sharing Groups, the “all org” flag sometimes provided view access to unintended actors. Thanks to Jeroen Pinoy for the report. The vulnerability has <a href="https://cvepremium.circl.lu/cve/CVE-2021-27904">CVE-2021-27904</a> assigned.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2021-03-09T23:00:00+00:00https://www.misp-project.org/2021/02/16/MISP.2.4.139.releasedMISP - MISP 2.4.139 released (Quality of life and bugfix release)2021-02-15T23:00:00+00:00<h1 id="misp-24139-released">MISP 2.4.139 released</h1>
<p>We have released 2.4.139, the latest release for MISP squashes a set of pretty annoying bugs, whilst also adding some shiny new features to play with, along with the usual update of the JSON libraries.</p>
<p>Besides that, several usability and performance issues have been resolved along with a host of small improvements, additional API improvements, etc. Make sure that you read the detailed changelog to see all the improvements.</p>
<h1 id="misp-modules-are-now-event-report-aware">MISP modules are now Event Report aware!</h1>
<p>The Event Reports are the hot new feature of the past few weeks and we are working on ensuring that analyst reports are becoming the standard companions of the classic event format. For anyone that hasn’t played with them before, have a look at the <a href="https://www.misp-project.org/2020/10/08/Event-Reports.html">blog post</a> describing how you can create rich, interlinked reports to accompany your events.</p>
<p>The main update to the Event Report system is its inclusion in the module system as of this version, so if you are building integrations with MISP or simply want to build a convenient way to incorporate reports from your favourite information sources, this feature will make your life much easier.</p>
<h1 id="misp-modules-can-impose-options-for-the-event-fetcher">MISP modules can impose options for the event fetcher</h1>
<p>Want to restrict what parts of an event your module should receive from MISP? Would you like to include the decay score in your module? Pass parameters back to the fetcher so it can prepare an event that better fits your module’s needs!</p>
<h1 id="eventstream-widget">EventStream widget</h1>
<p><img src="/assets/images/misp/blog/dashb.png" alt="" /></p>
<p>The built in Dashboard system in MISP has been underutilised since its inception, partially due to its initial focus on a non CTI use-case. We have been working on remedying this over the past few months, including the addition of new widgets to monitor your instance’s health as an administrator, to gain high level insights into your sharing community’s sharing practices, etc.</p>
<p>Something that has been missing for a while though was the ability to monitor ongoing trends based on your own interests, such as any new events coming in that relate to a topic that you are interested in. The EventStream widget aims to solve that, by offering a customisable event index widget.</p>
<p>Users can set their interests in terms of organisation sources and applied tags (such as threat actor, tool and other names) to show the most recent additions that touch on the given subjects.</p>
<p>This widget also brings a flexible reusable UI layer with itself that widget developers can reuse for a host of other use-cases.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2021-02-15T23:00:00+00:00https://www.misp-project.org/2021/02/10/MISP.2.4.138.releasedMISP - MISP 2.4.138 released (Many improvements including CISA.gov AIS dynamic marking functionality, RSIT galaxy added)2021-02-09T23:00:00+00:00<h1 id="misp-24138-released">MISP 2.4.138 released</h1>
<p>We have released 2.4.138, the latest release for MISP along with an update of the JSON libraries.</p>
<p>Besides that, several usability and performance issues have been resolved along with a host of small improvements, additional API improvements, etc. Make sure that you read the <a href="https://www.misp-project.org/Changelog.txt">detailed changelog</a> to see all the improvements. Improvements include the use of the threat level for the alert filtering, many bugs fixed in the event graph and many others.</p>
<h1 id="nested-galaxy-element-generator">Nested Galaxy Element generator</h1>
<p>We have a new tool that allows you to take nested JSON documents and convert it to galaxy cluster elements using a dot delimited format. If you ever want to quickly encoding existing nested data for your custom galaxies, this should make your life easier. This functionality was integrated for the support of the <a href="https://www.cisa.gov/sites/default/files/publications/AIS%20Brokering%20Between%20the%20Non-Federal%20Entities%20Sharing%20Community%20and%20the%20Federal%20Entities%20Sharing%20Community.pdf">Automated Indicator Sharing (AIS) from DHS/CISA.gov</a> to include dynamic marking. The functionality can be reused for many different use-cases.</p>
<p><img src="https://raw.githubusercontent.com/MISP/misp-training/main/a.10-galaxy-2.0/pics/json-view.png" alt="" />
<img src="https://raw.githubusercontent.com/MISP/misp-training/main/a.10-galaxy-2.0/pics/tabular-view.png" alt="" /></p>
<h1 id="rsit-galaxy-added-with-mitre-attck">RSIT galaxy added with MITRE ATT&CK</h1>
<p><a href="https://github.com/enisaeu/Reference-Security-Incident-Taxonomy-Task-Force">Reference Security Incident Taxonomy Working Group</a>, is a joint initiative for CSIRTs to produce a reference taxonomy for the CSIRT community. A new version of RIST has been integrated into MISP along with a complete set of relationships with MITRE ATT&CK, thanks to the <a href="https://www.misp-project.org/2020/12/16/MISP.2.4.135.released.html">galaxy 2.0 feature</a> in MISP. Thanks to <a href="https://www.cudeso.be/">Koen Van Impe</a> for this new updated galaxy.</p>
<p><img src="https://www.misp-project.org/assets/images/misp/blog/rsit-3.png" alt="" />
<img src="https://www.misp-project.org/assets/images/misp/blog/rsit-3.png" alt="" />
<img src="https://www.misp-project.org/assets/images/misp/blog/rsit-3.png" alt="" /></p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2021-02-09T23:00:00+00:00https://www.misp-project.org/2021/01/20/MISP.2.4.137.releasedMISP - MISP 2.4.137 released (New exclusion module for the correlation engine, many improvements and security vulnerabilities resolved)2021-01-19T23:00:00+00:00<h1 id="misp-24137-released">MISP 2.4.137 released</h1>
<p>We have released 2.4.137, a security and bug fix release including a collection of fixes and improvements collected over the past month.</p>
<p>Building tools for the security community sure has its perks - over the past week we have received two independent security test results of two separate organisations, revealing several vulnerabilities. The update to this version is therefore highly recommended.</p>
<p>A little note on vulnerability - we <a href="https://www.misp-project.org/security/">always welcome organisations helping us secure MISP</a> and our tooling in general and would hereby like to thank everyone taking part in the process!</p>
<h1 id="several-vulnerabilities-resolved">Several vulnerabilities resolved</h1>
<ul>
<li>[CVE-2021-25324] Stored XSS via the galaxy cluster view - Discovered by Daniel Kubica of ESET, spol. s r.o.</li>
<li>[CVE-2021-25325] Stored XSS via the galaxy element index - Discovered by Daniel Kubica of ESET, spol. s r.o.</li>
<li>[CVE-2021-25323] Weak default password change request policy not requiring the entry of the current password - Discovered by Daniel Kubica of ESET, spol. s r.o.</li>
<li>[CVE-2021-3184] Reflected XSS via the set homepage button - Reported by an anonymous party</li>
</ul>
<h1 id="a-long-list-of-quality-of-life-improvements">A long list of quality of life improvements</h1>
<ul>
<li>The synchronisation now compresses the data exchanged, improving the transfer rates during the exchange</li>
<li>Additional metrics and comparison tools for the sync connections</li>
<li>Better management of API key usage along with logging</li>
<li>A new tool that allows the exclusion of certain values from the correlation engine (useful to avoid having regularly observed values recurring in a large number of events generating too much noise)</li>
</ul>
<p>Along with many other fixes. A special thank you to @JakubOnderka for providing a steady stream of QoL improvements, making MISP more pleasant to use by the day!</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2021-01-19T23:00:00+00:00https://www.misp-project.org/2021/01/18/MISP.2.4.136.releasedMISP - MISP 2.4.136 released (Cerebrate project integration)2021-01-17T23:00:00+00:00<h1 id="misp-24136-released">MISP 2.4.136 released</h1>
<p>Though we’re rather late with the release notes, we did have some goodies to share for the winter festivities, bundled neatly into the <a href="https://github.com/MISP/MISP/releases/tag/v2.4.136">2.4.136 release</a>.</p>
<p>Apart from the usual bug fixes and usability improvements, we’ve also added some new features to play with.</p>
<h1 id="first-integration-with-cerebrate">First integration with Cerebrate</h1>
<p><a href="https://github.com/cerebrate-project">Cerebrate</a> is an up and coming tool we’re developing as part of the <a href="https://ec.europa.eu/digital-single-market/en/news/open-platforms-collaborate-cyber-threats">MeliCERTes project</a>, aiming to ease the management of both larger sharing communities as well as a set of local tools. The tool is self-hosted and can be used to maintain information on organisations and individuals that we interact with along with sharing group metadata. We also want to use this to make the harmonisation of MISP related organisation metadata information between instances of an organisation or a community (such as UUIDs, public keys, meta-information, etc).</p>
<p>In addition it will also act as an orchestration platform, easing the interconnections between organisations for both MISP and other tools.</p>
<p>In this first iteration, we can use a Cerebrate instance as a lookup repository for organisation metadata in MISP, using a familiar preview/pull mechanism that we’re used to in MISP.</p>
<p>We also welcome contributions to that project, especially since the internals are aligned more and more with MISP and will act as the foundation for the next major MISP rework. For more information visit the <a href="https://github.com/cerebrate-project">Cerebrate on github</a></p>
<h1 id="a-host-of-quality-of-life-improvements-for-the-sharing-groups">A host of quality of life improvements for the sharing groups</h1>
<p>The larger our communities grow, the more it becomes important to be able to quickly and accurately find the information that we’re after in our sharing group repositories. Thanks to the tireless work of @JakubOnderka, we can now filter sharing groups, find events associated to a sharing group and more.</p>
<h1 id="even-though-testing-is-doubting-doubt-is-the-origin-of-wisdom">Even though testing is doubting, doubt is the origin of wisdom</h1>
<p>A new test suite was added by @JakubOnderka to enrich the CI suite with a set of tests aiming to detect potential security / ACL flaws in the system.</p>
<h1 id="installer-improvements">Installer improvements</h1>
<p>The <a href="https://misp.github.io/MISP/INSTALL.ubuntu2004/">MISP installer</a> has been significantly improved especially concerning the installation of the misp-modules and various refactoring to improve the capability of replaying the install process.</p>
<h1 id="release-management">Release management</h1>
<p>Finally a notice on a change we have made to our release management, we will from here on rely on an additional branch for development to ensure that half-baked features don’t make their way to the 2.4 branch. Until now the recommendation was to stick to tagged releases for stability and to just track the 2.4 branch for the quickest bug fixes.</p>
<p>This lead to both options having downsides (should I miss out on a potential bug fix or risk running non-finalised features in my system?).</p>
<p>With the current approach, all new development will go on the “develop” branch, which we purely recommend to be used by developers, the 2.4 branch will see the features merged from develop just prior to a release after the testing and readying the release is completed. Once that is done, the usual tagging of a new version will occur.</p>
<p>This allows us to still include hotfixes and urgent bugfixes on 2.4, without muddying the water with potentially risky new developments, as such we encourage all users to track the HEAD of the 2.4 branch from here on.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2021-01-17T23:00:00+00:00https://www.misp-project.org/2020/12/16/MISP.2.4.135.releasedMISP - MISP 2.4.135 released (galaxy 2.0)2020-12-15T23:00:00+00:00<h1 id="misp-24135-released">MISP 2.4.135 released</h1>
<p>Don’t let the minor version number change fool you, this release is a game changer for MISP and information sharing in general. Galaxy 2.0 brings about the ability to customise Galaxy clusters (threat-actors, @MITREattack or any knowledge base element) as well as to extend and share it within your community. This release also includes many new improvements such as a new authkey system to better handle your API keys in MISP.</p>
<p><img src="https://www.misp-project.org/assets/images/galaxy2.0/1.jpeg" alt="" />
<img src="https://www.misp-project.org/assets/images/galaxy2.0/2.jpeg" alt="" />
<img src="https://www.misp-project.org/assets/images/galaxy2.0/3.jpeg" alt="" />
<img src="https://www.misp-project.org/assets/images/galaxy2.0/4.jpeg" alt="" /></p>
<p>The galaxy 2.0 feature is large and provide many new features. For a complete overview, the <a href="https://www.misp-project.org/misp-training/a.10-galaxy-2.0.pdf">following slide deck</a> provides a good introduction to galaxy 2.0.</p>
<h1 id="new-advanced-api-authkeys">New Advanced API authkeys</h1>
<p>Advanced authkeys will allow each user to create and manage a set of authkeys for themselves, each with individual expirations and comments. API keys are stored in a hashed state and can no longer be recovered from MISP. Users will be prompted to note down their key when creating a new authkey. You can generate a new set of API keys for all users on demand in the diagnostics page, or by triggering the advanced upgrade. If you upgrade your MISP, you need to enable this new feature in the security configuration (Security.advanced_authkeys).</p>
<h1 id="jarm-fingerprint-format-added">JARM fingerprint format added</h1>
<p>MISP (and MISP standard format) now includes the support for <a href="https://github.com/salesforce/jarm">JARM</a>, active Transport Layer Security (TLS) server fingerprinting tool.</p>
<h1 id="stix-2-import-improvements">STIX 2 import improvements</h1>
<ul>
<li>Fixed parsing of objects mapped into galaxies for external STIX.</li>
<li>For objects from external STIX content that should be mapped as galaxies (such as malware, threat actor, and so on), we do not only test the perfect match with one of the galaxy names in the mapping dictionary, we also test now if the galaxy name is contained in any of the known galaxy names of the dictionary</li>
</ul>
<p>Additionally, a host of other improvements are documented in the <a href="https://www.misp-project.org/Changelog.txt">complete changelog</a>.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2020-12-15T23:00:00+00:00https://www.misp-project.org/2020/11/10/MISP.2.4.134.releasedMISP - MISP 2.4.134 released (new import extractor for the event report, various improvements and fixes)2020-11-09T23:00:00+00:00<h1 id="misp-24134-released">MISP 2.4.134 released</h1>
<p>In the previous version of MISP, the new <a href="https://www.misp-project.org/2020/10/08/Event-Reports.html">Event Report functionality</a> has been introduced to edit, visualise and share reports in Markdown format, which includes the ability to reference elements from within a MISP event.</p>
<p>In the current version, the Event Report has been extended to support the automatic discovery of attributes, galaxies and tags from any website captured.</p>
<video src="https://www.misp-project.org/assets/images/misp/blog/event-report-demo-extraction-from-url2.mp4" title="Overview video of the new MISP event report functionality and discover of elements" width="800" height="450" controls="" autoplay="" loop="">Video tag is not supported by your browser</video>
<p>This functionality allows the analysts to collect external reports and automatically discover information which can be used in MISP.
The Event Report fetching capabilities require the <a href="https://github.com/MISP/misp-modules">misp-modules</a> to be activated.</p>
<h1 id="optional-av-scanning-in-misp">Optional A/V scanning in MISP</h1>
<p>A new feature has been added to automatically scan attachments in MISP. The functionality is completely optional and can be enabled in the global configuration.</p>
<h1 id="attck-sub-techniques">ATT&CK sub-techniques</h1>
<p>MISP now includes the ATT&CK sub-techniques as a MISP galaxy.</p>
<h1 id="example-script-for-direct-stix-ingestion-into-misp">Example script for direct STIX ingestion into MISP</h1>
<p>A new <a href="https://github.com/MISP/MISP/tree/2.4/tools/ingest_stix">Ingest STIX</a> script is available to show how to easily ingest STIX 1 and 2 files in MISP while using the parsing functionality of MISP core.</p>
<h1 id="security-fix---cve-2020-28043">Security fix - CVE-2020-28043</h1>
<p>A security vulnerability <a href="https://cve.circl.lu/cve/CVE-2020-28043">CVE-2020-28043</a> has been fixed. MISP through 2.4.133 allows SSRF in the REST client via the use_full_path parameter with an arbitrary URL.</p>
<ul>
<li>by using the full path parameter in the rest client, users could issue queries to any server</li>
<li>this becomes especially problematic when the MISP server is able to query other internal servers,
as external users could trigger those</li>
<li>new server setting added that allows enabling the full path option, this is now disabled by default</li>
<li>new server setting added to add an override baseurl for the rest client, removing the need for the full
path option in the first place (for example for the training VM with its port forwarding)</li>
<li>Thanks to Heitor Gouvêa for reporting this vulnerability</li>
</ul>
<h1 id="many-bugs-fixed-and-small-improvements">Many bugs fixed and small improvements</h1>
<ul>
<li>Tag index has been improved with a simple view excludes eventtags / attributetags / sightings</li>
<li>Many UI improvements (thanks to Jakub Onderka for his continuous effort and attention to details)</li>
</ul>
<p>A host of other improvements are documented in the <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a>.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2020-11-09T23:00:00+00:00https://www.misp-project.org/2020/10/16/MISP.2.4.133.releasedMISP - MISP 2.4.133 released (major improvements such as the markdown report feature and many UI improvements)2020-10-15T23:00:00+00:00<h1 id="misp-24133-released-with-major-improvements-such-as-the-markdown-report-feature-and-many-ui-improvements">MISP 2.4.133 released with major improvements such as the markdown report feature and many UI improvements.</h1>
<h1 id="unstructuredsemi-structured-report-feature">Unstructured/semi-structured report feature</h1>
<p>MISP is widely known as a powerful tool to gather, correlate and share information. As a response to the growing information-sharing maturity of the community, more features have been introduced over the past few years to meet analyst skills and requirements.</p>
<p>MISP has evolved to support a richer data structure allowing analysts and operators to describe and visualize complex scenarios. Data stored in MISP can be adjusted and linked in a comprehensive manner turning them into explorable graphs or timelines representing their activity or events.</p>
<p>However, in the current threat intelligence scene, information is often explained and shared in the form of article and using MISP’s raw text comments is far from ergonomic and appealing. Consequently, a crucial piece of data structure was missing and had to be supported: Reports.</p>
<p>In MISP 2.4.133, the report feature has been introduced including a complete Markdown editor to edit one or more report(s) attach to an event. The report feature including
a complete editor to allow an interactive method to add structured information from the MISP event including attributes, objects, galaxies or tags into the report.</p>
<p><img src="https://www.misp-project.org/assets/images/misp/blog/event-reports/cm-hints.gif" alt="Editor hints" />
<img src="https://www.misp-project.org/assets/images/misp/blog/event-reports/cm-hints-tag.gif" alt="Editor hints tags" /></p>
<p>The report editor provides features such as:</p>
<ul>
<li>Markdown syntax shortcuts</li>
<li>Auto-completion</li>
<li>Synchronized scrolling between the text editor and the markdown viewer</li>
<li>Automatic markdown rendering when typing</li>
<li>Fullscreen and resizable interface</li>
<li>Time since last edit & quick save</li>
</ul>
<p><img src="https://www.misp-project.org/assets/images/misp/blog/event-reports/editor-full.png" alt="Event editor full" /></p>
<p>Event reports have all the standard properties regarding information sharing available MISP such as distribution level, sharing communities. A report can be shared to specific groups while structured information can be shared to a wider audience as an example.</p>
<p><em>Event reports</em> also offer a wide range of new possibilities that were not doable efficiently before. For example, Counter analysis on cases can be explained, resolution steps and recommendations can be supplied, and complete articles can be included inside an <em>event</em>.</p>
<p>For more details, check out our blog post: <a href="https://www.misp-project.org/2020/10/08/Event-Reports.html">Event Report: A convenient mechanism to edit, visualize and share reports</a>.</p>
<h1 id="new-features">New features</h1>
<h2 id="ui">UI</h2>
<ul>
<li>Add icons for threat levels.</li>
<li>Show organisation nationality flag.</li>
<li>Use flag icons from Twemoji.</li>
<li>Go directly to object reference when referenced object is on the same page.</li>
<li>Major improvements in the misp-modules view especially for the enrichment output.</li>
<li>Many more improvements. Thanks to Jakub Onderka for his continuous attention to the details.</li>
</ul>
<h2 id="recovery-of-deleted-events">Recovery of deleted events</h2>
<ul>
<li>A new feature has been added to recover deleted events available in the diagnostics page. The feature uses the event history.</li>
</ul>
<h1 id="new-attribute-types-and-changes">New attribute types and changes</h1>
<ul>
<li><code class="highlighter-rouge">filename-pattern</code> filename-pattern to describe a filename based on a pattern (to avoid ambiguity from the filename attribute).</li>
<li><code class="highlighter-rouge">cpe</code> attribute to share and describe <a href="https://nvd.nist.gov/products/cpe">CPE - Common Platform Enumeration</a> - and associated object like <a href="https://github.com/MISP/misp-objects/blob/main/objects/cpe-asset/definition.json">cpe-asset</a></li>
<li><code class="highlighter-rouge">telfhash</code> attribute type added and associate file object updated. For more details about <a href="https://github.com/trendmicro/telfhash">telfhash</a>.</li>
<li>Normalize <code class="highlighter-rouge">AS</code> type to asplain notation.</li>
</ul>
<h1 id="speedup-and-optimisation">Speedup and optimisation</h1>
<ul>
<li>Speedup sending module results.</li>
<li>Sighting saving optimisation.</li>
<li>[warninglist] Use faster method for fetching data from Redis.</li>
<li>[complextype] Speedup hash parsing from CSVs and freetexts.</li>
</ul>
<h1 id="many-bugs-fixed-and-small-improvements">Many bugs fixed and small improvements</h1>
<p>A host of other improvements are documented in the <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a>.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>
.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2020-10-15T23:00:00+00:00https://www.misp-project.org/2020/10/08/Event-ReportsMISP - Event Report - A convenient mechanism to edit, visualize and share reports2020-10-07T23:00:00+00:00<h1 id="event-report-a-convenient-mechanism-to-edit-visualize-and-share-reports">Event Report: A convenient mechanism to edit, visualize and share reports</h1>
<p>MISP is widely known as a powerful tool to gather, correlate and share information. As a response to the growing information-sharing maturity of the community, more features have been introduced over the past few years to meet analyst skills and requirements.</p>
<p>MISP has evolved to support a richer data structure allowing analysts and operators to describe and visualize complex scenarios. Data stored in MISP can be adjusted and linked in a comprehensive manner turning them into explorable graphs or timelines representing their activity or events.</p>
<p>However, in the current threat intelligence scene, information is often explained and shared in the form of article and using MISP’s raw text comments is far from ergonomic and appealing.
Consequently, a crucial piece of data structure was missing and had to be supported: Reports.</p>
<p>This article presents the most recently introduced feature to manipulate and share reports in MISP as well as provide tips and tricks on how to use it in the best possible way.</p>
<h2 id="new-feature-event-report">New feature: <em>Event report</em></h2>
<p><strong>Note</strong>: In order to have a meaningful example, excerpts of the article from welivesecurity.com about <a href="https://www.welivesecurity.com/2020/01/31/winnti-group-targeting-universities-hong-kong/">Winnti Group targeting universities in Hong Kong</a> have been encoded.
The full demo <em>event</em> along with the <em>event report</em> is available <a href="/assets/images/misp/blog/event-reports/misp.event-report-demo.json">here</a>.</p>
<h3 id="basic-operations-creation-deletion-and-synchronization">Basic operations: Creation, deletion and synchronization</h3>
<p>As the name <em>Event report</em> indicates, reports in MISP are contained inside an <em>event</em>. It is important to note that <em>events</em> can contain more than one report.</p>
<p><em>Event reports</em> can be revealed by clicking on the toggle button <code class="highlighter-rouge">Event reports</code> located in the event toolbar</p>
<p><img src="/assets/images/misp/blog/event-reports/event-toolbar.png" alt="Event toolbar" /></p>
<p>An <em>Event report</em> must have a name consisting of a few words summary about what you would expect in the report and a distribution level. The report’s content can also be set here, but it is optional as a dedicated editor interface is available.</p>
<p>Similar to <em>attributes</em>, reports can be either <code class="highlighter-rouge">soft-deleted</code> or <code class="highlighter-rouge">hard-deleted</code>. The advantage of <code class="highlighter-rouge">soft</code> over <code class="highlighter-rouge">hard</code> is that the delete directive will be propagated in the network of connected MISP instances whereas the other will only be effective locally.</p>
<p>To put it simply, <em>event reports</em> behave like attributes meaning that their distribution mechanism is identical.</p>
<h2 id="writing-an-event-report">Writing an <em>Event report</em></h2>
<p>A report’s content can be non-formatted raw text but the power of the feature comes from its markdown parser.
As a matter of fact, markdown format is <strong>highly recommended</strong> as it offers an easy-to-use syntax, a pleasant document, and if coupled with MISP custom directives, an easy-to-write pleasant interactive document!</p>
<p><img src="/assets/images/misp/blog/event-reports/report-modal.png" alt="Event report" /></p>
<p>The editor interface presents a menu where reports can be downloaded in different formats and markdown rules can be turned on and off.
Information on how to use the custom MISP markdown directives, supported markdown plugins and editor shortcuts can be found in the help menu.</p>
<p><img src="/assets/images/misp/blog/event-reports/edit-toolbar.png" alt="Event toolbar" /></p>
<p>When it comes to editing, the best way to write a report is to use the split-screen mode as it offers both a text editor and a markdown viewer at the same time, providing an intuitive WYSIWYG experience.</p>
<p><img src="/assets/images/misp/blog/event-reports/editor-full.png" alt="Event toolbar" /></p>
<p>The editor provides features such as:</p>
<ul>
<li>Markdown syntax shortcuts</li>
<li>Auto-completion</li>
<li>Synchronized scrolling between the text editor and the markdown viewer</li>
<li>Automatic markdown rendering when typing</li>
<li>Fullscreen and resizable interface</li>
<li>Time since last edit & quick save</li>
</ul>
<h3 id="custom-misp-markdown-directives">Custom MISP markdown directives</h3>
<p>The supported markdown format is similar to <a href="https://github.github.com/gfm/">GFM</a> with some differences:</p>
<ul>
<li>No html support, typographer & autolinker</li>
<li>An additional syntax to reference MISP Elements</li>
</ul>
<p>It means that you can use standard markdown syntax such as <em>italic</em>, <strong>bold</strong>, <code class="highlighter-rouge">code block</code> and tables, but it also supports custom commands to reference <em>attributes</em>, <em>objects</em> and <em>tags</em> called MISP elements.</p>
<p>In order to reference MISP elements, a syntax close to the markdown’s link syntax is used</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>@[scope](UUID)
</code></pre></div></div>
<p>Where <strong>scope</strong> represents the scope of the element being referenced and <strong>UUID</strong> is the actual UUID of the element.</p>
<p>Here are some examples with their UI appearance</p>
<ul>
<li>
<p><strong>attribute:</strong> <code class="highlighter-rouge">@[attribute](5f1accda-cde4-47fc-baf1-6ab8f331dc3b)</code></p>
<p><img src="../assets/images/misp/blog/event-reports/md-attribute.png" alt="attribute" /></p>
</li>
<li>
<p><strong>object:</strong> <code class="highlighter-rouge">@[object](e2293538-93a9-4c53-9c92-75ba75cfec3d)</code></p>
<p><img src="../assets/images/misp/blog/event-reports/md-object.png" alt="object" /></p>
</li>
<li>
<p><strong>object’s attribute:</strong> <code class="highlighter-rouge">@[attribute](5f5907a9-7bcc-4676-9bd2-4f330a00020f)</code></p>
<p><img src="../assets/images/misp/blog/event-reports/md-object-attribute.png" alt="object's attribute" /></p>
</li>
<li>
<p><strong>tag:</strong> <code class="highlighter-rouge">@[tag](tlp:green)</code></p>
<p><img src="../assets/images/misp/blog/event-reports/md-tag.png" alt="tag" /></p>
</li>
<li>
<p><strong>galaxy cluster:</strong> <code class="highlighter-rouge">@[tag](misp-galaxy:malpedia="ShadowPad")</code></p>
<p><img src="../assets/images/misp/blog/event-reports/md-cluster.png" alt="galaxy cluster" /></p>
</li>
<li>
<p><strong>galaxy matrix:</strong> <code class="highlighter-rouge">@[galaxymatrix](c4e851fa-775f-11e7-8163-b774922098cd)</code></p>
<p><img src="../assets/images/misp/blog/event-reports/md-galaxy-matrix.png" alt="galaxy matrix" /></p>
</li>
</ul>
<p><em>Attributes</em> containing an attachment of a picture can also be displayed in the report with the following syntax</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>@
</code></pre></div></div>
<p>Example:</p>
<ul>
<li><strong>Attribute picture:</strong> <code class="highlighter-rouge">@</code>
<ul>
<li>Will display the picture</li>
</ul>
</li>
</ul>
<p>With this special syntax, MISP elements can be referenced and reports become interactive by clicking on the rendered MISP elements.</p>
<p><img src="/assets/images/misp/blog/event-reports/md-popover.png" alt="MISP Element popover" /></p>
<h3 id="editor-autocompletion">Editor autocompletion</h3>
<p>The editor provides auto-completion for various types of datapoints. Once the <code class="highlighter-rouge">scope</code> is picked, suggestions are proposed based on the value provided in the <code class="highlighter-rouge">UUID</code> field. Once the hint is chosen, the provided value is replaced by the actual UUID of the element, the only exception being for tags.</p>
<ul>
<li>
<p>Hinting with the filename value</p>
<p><img src="/assets/images/misp/blog/event-reports/cm-hints.gif" alt="Editor hints" /></p>
</li>
<li>
<p>Hinting with the threat actor tag</p>
<p><img src="/assets/images/misp/blog/event-reports/cm-hints-tag.gif" alt="Editor hints tags" /></p>
</li>
</ul>
<h2 id="summary">Summary</h2>
<p>With the support of reports built-in in MISP, a new kind of knowledge can be used. Classical threat intelligence reports, malware analysis articles or even something of a completely different taste can be shared along with the actionable data.</p>
<p><em>Event reports</em> also offer a wide range of new possibilities that were not doable efficiently before. For example, Counter analysis on cases can be explained, resolution steps and recommendations can be supplied, and complete articles can be included inside an <em>event</em>.</p>
<p>Furthermore, it opens the door for new ways to create information in MISP. In the future, we could imagine doing it the other way around by extracting IoCs, threat actors and so on directly from the report.</p>2020-10-07T23:00:00+00:00https://www.misp-project.org/2020/09/30/How-To-Make-A-MISP-Import-ScriptMISP - Create an import script for MISP , step-by-step tutorial2020-09-29T23:00:00+00:00<h1 id="create-an-import-script-for-misp-in-python-step-by-step-tutorial">Create an import script for MISP in Python, step-by-step tutorial</h1>
<h2 id="script-description">Script description</h2>
<h3 id="example-add_github_userpy">Example add_github_user.py</h3>
<p>Here the goal is to push to MISP information gathered on Github. The script <a href="https://github.com/MISP/PyMISP/blob/main/examples/add_github_user.py">add_github_user.py</a> will be used as an example.</p>
<p>An <strong>import script</strong>, it’s different from a MISP module.</p>
<p>An import script is run from a terminal to push data into a MISP, but a MISP module runs into a MISP instance. For more information about MISP modules, see <a href="https://misp.github.io/misp-modules/">here</a></p>
<p>This script will add data from GitHub as object to an existing MISP event.</p>
<p><strong>Tips:</strong> in early phase or for testing purpose, it’s better to start with an import script to test the code and results. If it’s conclusive you can code a MISP module.</p>
<h3 id="pymisp-install">PyMISP install</h3>
<p>PyMISP is a Python library to access MISP with REST API. Install the <a href="https://github.com/MISP/PyMISP">PyMISP</a> library on your machine.</p>
<p>To do so, clone the <a href="https://github.com/MISP/PyMISP">repository</a> and install the library:</p>
<div class="language-bash highlighter-rouge"><div class="highlight"><pre class="highlight"><code>git clone https://github.com/MISP/PyMISP
<span class="nb">cd </span>PyMISP
pip3 install <span class="nb">.</span>
</code></pre></div></div>
<h3 id="fork">Fork</h3>
<p>If you wish to contribute and push your code to the MISP community, you’ll need to fork the PyMISP library.</p>
<h3 id="meaningful-naming">Meaningful naming</h3>
<p>Where to put the files and what are their names?</p>
<p>The script will be in <strong><a href="https://github.com/MISP/PyMISP/tree/main/examples">PyMISP/examples</a></strong> and has the name of the imported service. A short key word is a good practice to describe the script action:</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>PyMISP/examples/add_github_user.py
</code></pre></div></div>
<p><strong>tips:</strong> before naming your script, consult the list of available scripts into the PyMISP/examples folder, in order to describe accurately what your import module does.</p>
<h3 id="keys-management">Keys management</h3>
<p>For all scripts , you need to have a single key file <strong>keys.py</strong>. The file is not to be committed and contains the credentials for connecting to the MISP instance: API key, URL, SSH validations.</p>
<ul>
<li>You create a file keys.py into the dir PyMISP/examples.</li>
</ul>
<p>References to this file will be later set in the script:</p>
<div class="language-python highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="kn">from</span> <span class="nn">keys</span> <span class="kn">import</span> <span class="n">misp_url</span><span class="p">,</span> <span class="n">misp_key</span><span class="p">,</span> <span class="n">misp_verifycert</span>
</code></pre></div></div>
<h3 id="required-libraries">Required libraries</h3>
<ul>
<li>PyMISP</li>
<li>request</li>
<li>sys</li>
<li>argparse</li>
</ul>
<h3 id="usage-block">Usage block</h3>
<p>We will go through the Python code and explain step-by-step each part.</p>
<p>It will be used by pyDoc, starts with “”” and ends with “””. You will here describe the usage for the script.</p>
<div class="language-python highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="s">"""
usage: add_github_user.py [-h] -e EVENT [-f] -u USERNAME
Fetch GitHub user details and add it in object in MISP
optional arguments:
-h, --help show this help message and exit
-e EVENT, --event EVENT
Event ID to update
-f, --force-template-update
-u USERNAME, --username USERNAME
GitHub username to add
"""</span>
</code></pre></div></div>
<h3 id="argument-parser">Argument parser</h3>
<p>The script needs to grab the event-id (-e), a force to update the template from the repository (-f), and here a user account (-u).</p>
<div class="language-python highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="n">parser</span> <span class="o">=</span> <span class="n">argparse</span><span class="o">.</span><span class="n">ArgumentParser</span><span class="p">(</span><span class="n">description</span><span class="o">=</span><span class="s">'Fetch GitHub user details and add it in object in MISP'</span><span class="p">)</span>
<span class="n">parser</span><span class="o">.</span><span class="n">add_argument</span><span class="p">(</span><span class="s">"-e"</span><span class="p">,</span> <span class="s">"--event"</span><span class="p">,</span> <span class="n">required</span><span class="o">=</span><span class="bp">True</span><span class="p">,</span> <span class="n">help</span><span class="o">=</span><span class="s">"Event ID to update"</span><span class="p">)</span>
<span class="n">parser</span><span class="o">.</span><span class="n">add_argument</span><span class="p">(</span><span class="s">"-f"</span><span class="p">,</span> <span class="s">"--force-template-update"</span><span class="p">,</span> <span class="n">required</span><span class="o">=</span><span class="bp">False</span><span class="p">,</span> <span class="n">action</span><span class="o">=</span><span class="s">"store_true"</span><span class="p">)</span>
<span class="n">parser</span><span class="o">.</span><span class="n">add_argument</span><span class="p">(</span><span class="s">"-u"</span><span class="p">,</span> <span class="s">"--username"</span><span class="p">,</span> <span class="n">required</span><span class="o">=</span><span class="bp">True</span><span class="p">,</span> <span class="n">help</span><span class="o">=</span><span class="s">"GitHub username to add"</span><span class="p">)</span>
<span class="n">args</span> <span class="o">=</span> <span class="n">parser</span><span class="o">.</span><span class="n">parse_args</span><span class="p">()</span>
</code></pre></div></div>
<h3 id="request">Request</h3>
<p>NOTE: If the user doesn’t exist, the script is interrupted.</p>
<div class="language-python highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="n">r</span> <span class="o">=</span> <span class="n">requests</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s">"https://api.github.com/users/{}"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">args</span><span class="o">.</span><span class="n">username</span><span class="p">))</span>
<span class="k">if</span> <span class="n">r</span><span class="o">.</span><span class="n">status_code</span> <span class="o">!=</span> <span class="mi">200</span><span class="p">:</span>
<span class="n">sys</span><span class="o">.</span><span class="nb">exit</span><span class="p">(</span><span class="s">"HTTP return is {} and not 200 as expected"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">r</span><span class="o">.</span><span class="n">status_code</span><span class="p">))</span>
<span class="k">if</span> <span class="n">args</span><span class="o">.</span><span class="n">force_template_update</span><span class="p">:</span>
<span class="k">print</span><span class="p">(</span><span class="s">"Updating MISP Object templates..."</span><span class="p">)</span>
<span class="n">update_objects</span><span class="p">()</span>
<span class="n">pymisp</span> <span class="o">=</span> <span class="n">PyMISP</span><span class="p">(</span><span class="n">misp_url</span><span class="p">,</span> <span class="n">misp_key</span><span class="p">,</span> <span class="n">misp_verifycert</span><span class="p">)</span>
</code></pre></div></div>
<p>The PyMISP connection is instantiated with following parameters coming from the file keys.py : <em>misp_url, misp_keys and misp_verifycert</em>.</p>
<h3 id="object-creation">Object creation</h3>
<p>We create a MISP object, the name is the object template name:</p>
<div class="language-python highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="n">misp_object</span> <span class="o">=</span> <span class="n">MISPObject</span><span class="p">(</span><span class="n">name</span><span class="o">=</span><span class="s">"github-user"</span><span class="p">)</span>
</code></pre></div></div>
<p><strong>tips:</strong> you can find the object template name is the <a href="https://github.com/MISP/misp-objects">MISP object template repository</a>.</p>
<p><strong>contributing:</strong> if an object template is missing, you can propose your own.</p>
<h3 id="user-data">User data</h3>
<p>User data from the GitHub API are transformed into a JSON in order to be parsed by the following commands:</p>
<div class="language-python highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="n">github_user</span> <span class="o">=</span> <span class="n">r</span><span class="o">.</span><span class="n">json</span><span class="p">()</span>
</code></pre></div></div>
<p>Following HTTP GET requests to obtain the following and followers sections of the GitHub user.</p>
<div class="language-python highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="n">rfollowers</span> <span class="o">=</span> <span class="n">requests</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="n">github_user</span><span class="p">[</span><span class="s">'followers_url'</span><span class="p">])</span>
<span class="n">followers</span> <span class="o">=</span> <span class="n">rfollowers</span><span class="o">.</span><span class="n">json</span><span class="p">()</span>
<span class="n">rfollowing</span> <span class="o">=</span> <span class="n">requests</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s">"https://api.github.com/users/{}/following"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">args</span><span class="o">.</span><span class="n">username</span><span class="p">))</span>
<span class="n">followings</span> <span class="o">=</span> <span class="n">rfollowing</span><span class="o">.</span><span class="n">json</span><span class="p">()</span>
</code></pre></div></div>
<p>Same things for the SSH public keys attached to the GitHub user:</p>
<div class="language-python highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="n">rkeys</span> <span class="o">=</span> <span class="n">requests</span><span class="o">.</span><span class="n">get</span><span class="p">(</span><span class="s">"https://api.github.com/users/{}/keys"</span><span class="o">.</span><span class="n">format</span><span class="p">(</span><span class="n">args</span><span class="o">.</span><span class="n">username</span><span class="p">))</span>
<span class="n">keys</span> <span class="o">=</span> <span class="n">rkeys</span><span class="o">.</span><span class="n">json</span><span class="p">()</span>
</code></pre></div></div>
<p>Then, filling of the object from the github_user json object:</p>
<div class="language-python highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="n">misp_object</span><span class="o">.</span><span class="n">add_attributes</span><span class="p">(</span><span class="s">"follower"</span><span class="p">,</span> <span class="o">*</span><span class="p">[</span><span class="n">follower</span><span class="p">[</span><span class="s">'login'</span><span class="p">]</span> <span class="k">for</span> <span class="n">follower</span> <span class="ow">in</span> <span class="n">followers</span><span class="p">])</span>
<span class="n">misp_object</span><span class="o">.</span><span class="n">add_attributes</span><span class="p">(</span><span class="s">"following"</span><span class="p">,</span> <span class="o">*</span><span class="p">[</span><span class="n">following</span><span class="p">[</span><span class="s">'login'</span><span class="p">]</span> <span class="k">for</span> <span class="n">following</span> <span class="ow">in</span> <span class="n">followings</span><span class="p">])</span>
<span class="n">misp_object</span><span class="o">.</span><span class="n">add_attributes</span><span class="p">(</span><span class="s">"ssh-public-key"</span><span class="p">,</span> <span class="o">*</span><span class="p">[</span><span class="n">sshkey</span><span class="p">[</span><span class="s">'key'</span><span class="p">]</span> <span class="k">for</span> <span class="n">sshkey</span> <span class="ow">in</span> <span class="n">keys</span><span class="p">])</span>
<span class="n">misp_object</span><span class="o">.</span><span class="n">add_attribute</span><span class="p">(</span><span class="s">'bio'</span><span class="p">,</span> <span class="n">github_user</span><span class="p">[</span><span class="s">'bio'</span><span class="p">])</span>
<span class="n">misp_object</span><span class="o">.</span><span class="n">add_attribute</span><span class="p">(</span><span class="s">'link'</span><span class="p">,</span> <span class="n">github_user</span><span class="p">[</span><span class="s">'html_url'</span><span class="p">])</span>
<span class="n">misp_object</span><span class="o">.</span><span class="n">add_attribute</span><span class="p">(</span><span class="s">'user-fullname'</span><span class="p">,</span> <span class="n">github_user</span><span class="p">[</span><span class="s">'name'</span><span class="p">])</span>
<span class="n">misp_object</span><span class="o">.</span><span class="n">add_attribute</span><span class="p">(</span><span class="s">'username'</span><span class="p">,</span> <span class="n">github_user</span><span class="p">[</span><span class="s">'login'</span><span class="p">])</span>
<span class="n">misp_object</span><span class="o">.</span><span class="n">add_attribute</span><span class="p">(</span><span class="s">'twitter_username'</span><span class="p">,</span> <span class="n">github_user</span><span class="p">[</span><span class="s">'twitter_username'</span><span class="p">])</span>
<span class="n">misp_object</span><span class="o">.</span><span class="n">add_attribute</span><span class="p">(</span><span class="s">'location'</span><span class="p">,</span> <span class="n">github_user</span><span class="p">[</span><span class="s">'location'</span><span class="p">])</span>
<span class="n">misp_object</span><span class="o">.</span><span class="n">add_attribute</span><span class="p">(</span><span class="s">'company'</span><span class="p">,</span> <span class="n">github_user</span><span class="p">[</span><span class="s">'company'</span><span class="p">])</span>
<span class="n">misp_object</span><span class="o">.</span><span class="n">add_attribute</span><span class="p">(</span><span class="s">'public_gists'</span><span class="p">,</span> <span class="n">github_user</span><span class="p">[</span><span class="s">'public_gists'</span><span class="p">])</span>
<span class="n">misp_object</span><span class="o">.</span><span class="n">add_attribute</span><span class="p">(</span><span class="s">'public_repos'</span><span class="p">,</span> <span class="n">github_user</span><span class="p">[</span><span class="s">'public_repos'</span><span class="p">])</span>
<span class="n">misp_object</span><span class="o">.</span><span class="n">add_attribute</span><span class="p">(</span><span class="s">'blog'</span><span class="p">,</span> <span class="n">github_user</span><span class="p">[</span><span class="s">'blog'</span><span class="p">])</span>
<span class="n">misp_object</span><span class="o">.</span><span class="n">add_attribute</span><span class="p">(</span><span class="s">'node_id'</span><span class="p">,</span> <span class="n">github_user</span><span class="p">[</span><span class="s">'node_id'</span><span class="p">])</span>
</code></pre></div></div>
<p>Finally, you add the new object created, then pushed to the specified event id, on your MISP instance:</p>
<div class="language-python highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="n">retcode</span> <span class="o">=</span> <span class="n">pymisp</span><span class="o">.</span><span class="n">add_object</span><span class="p">(</span><span class="n">args</span><span class="o">.</span><span class="n">event</span><span class="p">,</span> <span class="n">misp_object</span><span class="p">)</span>
</code></pre></div></div>
<p>Now it’s your turn, to do a MISP import script.</p>2020-09-29T23:00:00+00:00https://www.misp-project.org/2020/09/21/MISP.2.4.132.releasedMISP - MISP 2.4.132 released (security fix CVE-2020-25766 and bugs fixed)2020-09-20T23:00:00+00:00<h1 id="misp-24132-released">MISP 2.4.132 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.132">2.4.132</a>) has been released with several bugs fixed including an important <a href="https://www.misp-project.org/security/">security</a> fix <a href="https://cve.circl.lu/cve/CVE-2020-25766">CVE-2020-25766</a>.</p>
<h1 id="bugs-fixed-and-updates">Bugs fixed and updates</h1>
<ul>
<li>[bootstrap-datepicker] Updated to version 1.9.0</li>
<li>[tag filters] fixed a bug introduced with the previous filter fix, resulting in multiple OR tags being ignored as a valid filter.</li>
<li>[internal] Correctly handle positive tag filters for non site admins.</li>
<li>[sightings] anonymise pushed sightings using new Sightings_anonymise_as setting.</li>
</ul>
<h1 id="cve-2020-25766">CVE-2020-25766</h1>
<p>An issue was discovered in MISP before 2.4.132. This could lead to an unwanted actions (such as an event deletion) being triggered. Thanks to Michael Kerscher for the report.</p>
<p>It was discovered that under certain situations (resource exhaustion when retrieving sessions data for example), a user could incorrectly receive the login page as a response when paginating the event view’s attribute list. This in itself should not cause any issues, but due to a bug in the login form’s GET/POST exchange, the user actually having a valid session would instead retrieve the event index, on which the first form was submitted (which was an event deletion). In normal situations this is extremely rare and we have only identified a handful of such deletions on our most heavily used community instances.</p>
<p>Version 2.4.133 will include a new diagnostic tool that highlights deletions from the time period when the bug was active along with a recovery functionality.</p>
<h1 id="many-bugs-fixed-and-small-improvements">Many bugs fixed and small improvements</h1>
<p>A host of other improvements are documented in the <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a>.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2020-09-20T23:00:00+00:00https://www.misp-project.org/2020/09/08/MISP.2.4.131.releasedMISP - MISP 2.4.131 released (improvements, bug fixes and major update to JavaScript dependencies)2020-09-07T23:00:00+00:00<h1 id="misp-24131-released">MISP 2.4.131 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.131">2.4.131</a>) has been released with improvements, bug fixes and a major update to JavaScript libraries.</p>
<h1 id="improvements">Improvements</h1>
<ul>
<li>New types pgp-public-key/pgp-private-key/email/sha3 added.</li>
<li>Export format for Bro, Snort, OpenIOC updated to support new email type (in addition to the legacy email-src/email-dst attribute type)</li>
<li>A new filter “type” added for the internal fetcher which appends email as a type if email-src/email-dst are found.</li>
<li>[types] email added as a new type, affects #6281.</li>
<li>[diagnostic] Check if database index is unique.</li>
<li>New API export: added “count” returnFormat for the REST API which simply counts the number of attributes/events found (on each respective scope).</li>
<li>The ACL has been extended to allow host org users to block events. Also added a new special permission for the ACL system host_org_user - which will evaluate whether the user is in the org configured in the MISP.host_org_id directive</li>
<li>Major upgrade to jQuery (Bumped jQuery to version 3.5.1.) and related dependencies.</li>
<li>STIX 1 Importing test mechanisms from indicators as yara rules (as used by CISA).</li>
<li>The API GET requests on restsearch with no parameters are no longer allowed. warn the user of the use of GET queries with posted JSON bodies</li>
<li>STIX 2 import - Fixed external pattern types parsing.</li>
<li>Logging - Add the ability to customize the IP header field when logging.</li>
<li>New dasbhoard widget - Feature/achievements widget adding gamification to the information sharing.</li>
<li>New MISP-SNMP Monitor script.</li>
<li>Various fixes for accessibility for users of screen readers such as ARIA labels.</li>
</ul>
<h1 id="many-bugs-fixed-and-small-improvements">Many bugs fixed and small improvements</h1>
<p>A host of other improvements are documented in the <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a>.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2020-09-07T23:00:00+00:00https://blog.rootshell.be/?p=33864MISP - Monitoring MISP with Nagios2020-08-25T10:08:06+00:00<p>Yesterday, a very interesting article was published on the MISP blog by my friend Koen about a solution to monitor a MISP instance with Cacti. Monitoring your threat intelligence platform is always a good idea because many other tools depend on it. You can feed other tools with MISP data</p>
<p>The post <a rel="nofollow" href="https://blog.rootshell.be/2020/08/25/monitoring-misp-with-nagios/">Monitoring MISP with Nagios</a> appeared first on <a rel="nofollow" href="https://blog.rootshell.be">/dev/random</a>.</p>2020-08-25T10:08:06+00:00https://www.misp-project.org/2020/08/22/MISP-Monitoring-with-CactiMISP - MISP service monitoring with Cacti2020-08-21T23:00:00+00:00<h1 id="misp-service-monitoring-with-cacti">MISP service monitoring with Cacti</h1>
<h2 id="introduction">Introduction</h2>
<p>A previous post covered how to do <a href="/2020/08/18/MISP-Monitoring-with-OpenNMS.html">MISP service monitoring with OpenNSM</a>. Because having different options is good, this post covers how to achieve similar results with <a href="https://www.cacti.net/">Cacti</a>. For those not familiar with Cacti: it is a network graphing solution designed to harness the power of RRDTool’s data storage and graphing functionality.</p>
<p>We’ll monitor these aspects of a MISP server</p>
<ul>
<li>CPU, load average, memory usage and swap usage (based on default Cacti templates)</li>
<li>Interface statistics, logged in users and running processes (based on default Cacti templates)</li>
<li>MISP workers and job count</li>
<li>MISP event, attribute, users and organisation statistics</li>
<li>HTTP response time</li>
</ul>
<p>Interesting to know is that MISP already also has built-in features to monitor your system resources via <a href="https://www.misp-project.org/misp-training/a.a-widget-dev.pdf">widgets and dashboards</a>. There are widgets for monitoring system resources, MISP statistics and sightings.</p>
<h2 id="cacti-monitoring">Cacti monitoring</h2>
<h3 id="install-snmp">Install SNMP</h3>
<p>Cacti provides out of the box a lot of default templates to monitor system data. The data acquisition is mostly done via <strong>SNMP</strong>, or the Simple Network Management Protocol. You do not need additional client software but it does mean you have to install SNMP on the MISP server, and allow access on udp/161 from your Cacti host to the MISP server.</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>sudo apt-get install snmpd
sudo ufw allow proto udp from <cactihost> to any port 161
</code></pre></div></div>
<p>When SNMP is installed, make sure you set a read-only community string if you use version 2c or configure user authentication with version 3. Note that for version 2c the community string is sent in <em>clear</em> text. Cacti supports both SNMP versions 2c and version 3.</p>
<h3 id="add-a-device">Add a device</h3>
<p>You can find plenty of good writeups on how to monitor a Linux host with Cacti at <a href="https://www.sysadmin.md/monitoring-linux-and-windows-hosts-with-snmp-and-cacti.html">sysadmin.md</a> and <a href="https://nsrc.org/workshops/2019/mnnog1/nmm/netmgmt/en/cacti/cacti-from-packages.pdf">NSRC</a>.</p>
<p>The key items to remember are</p>
<ul>
<li>Choose <strong>Net-SNMP Device</strong> as device template</li>
<li>Set the correct SNMP Community String or SNMP User Authentication</li>
</ul>
<p>Once you added your MISP server as a device in Cacti, add these Graph Template</p>
<ul>
<li>Host MIB - Logged in Users</li>
<li>Host MIB - Processes</li>
<li>Net-SNMP - CPU Utilization</li>
<li>Net-SNMP - Load Average</li>
<li>Net-SNMP - Memory Usage</li>
</ul>
<p>And finally, add these Data Queries</p>
<ul>
<li>Net-SNMP - Get Monitored Partitions</li>
<li>SNMP - Get Mounted Partitions</li>
<li>SNMP - Get Processor Information</li>
<li>SNMP - Interface Statistics</li>
</ul>
<p>Afterwards click on <strong>Create Graphs for this Device</strong> to get an overview of available graphs. Then select the desired graphs and click on <strong>Create</strong>.</p>
<p><img src="/assets/images/monitor-cacti/add-graph-template.jpg" alt="Add Graphs" /></p>
<p>Allow it a bit of time so that Cacti can create the RRD files (RRDs are little ‘databases’ containing the statistics data) and poll sufficient information. If all goes well, you should have graphs similar to the ones below.</p>
<p><img src="/assets/images/monitor-cacti/default-cacti.jpg" alt="Default Cacti Graphs" /></p>
<h2 id="misp-workers-and-statistics">MISP Workers and Statistics</h2>
<p>Now let’s work our way to more specific MISP monitoring. The MISP data isn’t directly available via SNMP. But one of the nicer features of SNMP is that you can extend it with your own scripts, and have it return whatever data your script has access to. In order to make this work you have to specify the script name, how it is called from within SNMP and have the script return the statistic values.</p>
<h3 id="snmp-configuration">SNMP configuration</h3>
<p>Open the config file /etc/snmp/snmpd.conf and add these lines to <strong>extend</strong> SNMP with data for misp-workers, misp-jobs, misp-stats and misp-users.</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>extend misp-workers /home/misp/misp-snmp/misp-snmp-monitor.py workers
extend misp-jobs /home/misp/misp-snmp/misp-snmp-monitor.py jobs
extend misp-stats /home/misp/misp-snmp/misp-snmp-monitor.py stats
extend misp-users /home/misp/misp-snmp/misp-snmp-monitor.py users
</code></pre></div></div>
<p>There are some extra things to consider. First, the script (misp-snmp-monitor.py) is not placed in the MISP working directory (commonly /var/www/MISP). The reason is that the script is called by the SNMP daemon, which on Ubuntu runs under the username <em>Debian-snmp</em>. By default, this user does not have access to the MISP working directory. You can choose to grant permissions for the SNMP daemon user to the MISP working directory (less desired), or you can put this script in a dedicated directory and then set permissions there.</p>
<p>Second, Cacti will not call the keys ‘misp-workers’ or ‘misp-jobs’ directly, but will call them by their <strong>OID</strong>, or object identifiers. Simply put, an OID is a unique identifier mechanism to refer to (in this case) a value available in the SNMP database (this is an oversimplification of MIB). To access these values from within Cacti, you first have to translate them from the “string” value to the OID value. As it happens, SNMP has a tool for this.</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>snmptranslate -On 'NET-SNMP-EXTEND-MIB::nsExtendOutLine."misp-workers".1'
</code></pre></div></div>
<p>This will return the OID value <em>.1.3.6.1.4.1.8072.1.3.2.4.1.2.12.109.105.115.112.45.119.111.114.107.101.114.115.1</em>, which can then be used by Cacti. The last part of the OID, the .1, is the ID of the value returned. misp-snmp-monitor.py returns these values</p>
<ul>
<li>misp-workers: .1.3.6.1.4.1.8072.1.3.2.4.1.2.12.109.105.115.112.45.119.111.114.107.101.114.115.x
<ul>
<li>x = 1 = Number of workers alive</li>
<li>x = 2 = Number of dead workers</li>
</ul>
</li>
<li>misp-jobs: .1.3.6.1.4.1.8072.1.3.2.4.1.2.9.109.105.115.112.45.106.111.98.115.x
<ul>
<li>x = 1 = Total number of jobs in all worker queues</li>
</ul>
</li>
<li>misp-stats: .1.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.105.115.112.45.115.116.97.116.115.x
<ul>
<li>x = 1 = Number of new events this month</li>
<li>x = 2 = Number of new attributes this month</li>
</ul>
</li>
<li>misp-users: .1.3.6.1.4.1.8072.1.3.2.4.1.2.10.109.105.115.112.45.117.115.101.114.115.x
<ul>
<li>x = 1 = Number of users in the MISP instance</li>
<li>x = 2 = Number of organisations in the MISP instance</li>
</ul>
</li>
</ul>
<h3 id="snmp-script">SNMP Script</h3>
<p>Now install the misp-snmp-monitor script. The source code is available via <a href="https://github.com/MISP/MISP/pull/6221/files">Github PR-6221</a>. There are a couple of configuration settings:</p>
<ul>
<li><strong>misp_key</strong> : A MISP API key</li>
<li><strong>misp_url</strong> : The URL to your MISP instance</li>
<li><strong>misp_cachefile</strong> : A location where it can store cached data. The script is called via the SNMP daemon, as such, the SNMP user (for Ubuntu Debian-snmp) needs write permissions to this path. Also give it a full path, not a relative location.</li>
</ul>
<p>The cache can be built manually, but it’s more interesting to have this generated automatically. Add a crontab entry which to <strong>update</strong> the cached data.</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>*/30 * * * * misp /home/misp/misp-snmp/misp-monitor.py update
</code></pre></div></div>
<h3 id="test-it-first">Test it first</h3>
<p>Before we jump to Cacti, it’s safe to first test that the flow MISP > monitor script > SNMP works. Do not forget to restart the SNMPD service! Then issue this command</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>snmpget -v2c -c <SNMP community string> <MISP host - misp_url> .1.3.6.1.4.1.8072.1.3.2.4.1.2.12.109.105.115.112.45.119.111.114.107.101.114.115.1
</code></pre></div></div>
<p>This calls the OID corresponding with the first (.1) value of the key misp-workers: the number of live workers. If all is well you should receive an answer similar to</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>iso.3.6.1.4.1.8072.1.3.2.4.1.2.12.109.105.115.112.45.119.111.114.107.101.114.115.1 = STRING: "6"
</code></pre></div></div>
<p>The answer above indicates that there are 6 workers alive. Do the same for all the other keys.</p>
<h3 id="configure-cacti">Configure Cacti</h3>
<p>Next is configuring Cacti. You first have to configure a <strong>data source</strong> template, then a <strong>graph template</strong> and then add a new graph based on these templates to your device.</p>
<h4 id="data-source-template">Data Source Template</h4>
<p>To add the data source, click on <strong>Data Source</strong> under Templates, and then in the upper right corner the <strong>+</strong> to add a new template. Then complete these values</p>
<ol>
<li>A data source <strong>template</strong> name, for example MISP SNMP Workers Alive</li>
<li>The <strong>name</strong> for the data source, it is best to choose something similar as |host_description| - MISP SNMP Workers Alive. This will replace the data source name with the name of your device</li>
<li>Select the <strong>data input</strong> method <strong>Get SNMP Data</strong></li>
<li>An <strong>internal name</strong> for the data source, such as misp_workers_alive</li>
<li>Set the <strong>minimum</strong> and <strong>maximum</strong> value to no minimum/no maximum with <strong>U</strong></li>
<li>Add the OID corresponding with the SNMP value, this is the OID you retrieved via the snmptranslate command in the previous step.</li>
</ol>
<p><img src="/assets/images/monitor-cacti/data-source1.jpg" alt="Add Data Source Template" /></p>
<p>You have to complete this step for all the data you’d like to be monitored, for example the job count, statistics, users, etc.</p>
<h4 id="graph-template">Graph Template</h4>
<p>Add the graph template via <strong>Graph</strong> under Templates, and then in the upper right corner the <strong>+</strong> to add a new template. Then select these values</p>
<ol>
<li>Add the two new data source templates to the graph template</li>
<li>Select <strong>Area</strong> as graph type for workers alive, and <strong>Line 2</strong> as graph type for dead workers. Adding them will also automatically add them as <strong>graph item inputs</strong>.</li>
<li>Add a text label to display the number of workers alive and dead. Choose <strong>GPrint:LAST</strong> and the LAST value type.</li>
</ol>
<p>You can leave all the other values to their default settings.</p>
<p><img src="/assets/images/monitor-cacti/graph-source1.jpg" alt="Add Graph Template" /></p>
<p>You have to complete this step for all the data you’d like to be graphed, based on the previous created data sources.</p>
<h4 id="add-to-device">Add to device</h4>
<p>The final step is to add this graph template to your monitoring device. Under Management, Devices choose the MISP device and scroll down to Associated Graph Templates. If all is good, the newly created Graph Template should be available under Add Graph Template. Select it and click Add.</p>
<p><img src="/assets/images/monitor-cacti/add-graphtemplate.jpg" alt="Add Graph Template to Device" /></p>
<p>Then click <strong>Create Graphs for this Device</strong>, select the newly added graph and click Create.</p>
<p><img src="/assets/images/monitor-cacti/add-graph.jpg" alt="Add Graph Template to Device" /></p>
<p>Similar as with the previous Cacti graphs, you need to give it some time before the values are collected and represented in the graphs.</p>
<h2 id="misp-http-response-time">MISP HTTP Response time</h2>
<p>The final item we’d like to monitor is the HTTP response time of our MISP server. This response time also gives an indication if the (web) server is still properly running or not. We will use <strong>curl</strong> to get the statistics back from our server.</p>
<h3 id="http-monitor-with-curl">HTTP Monitor with Curl</h3>
<p>The standard install of Cacti does not have an HTTP response monitor but you can easily add this yourself. On the Cacti server, in the directory cacti/scripts add a <strong>bash file</strong> with the name http_response.sh and this content</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="c">#!/bin/sh</span>
curl <span class="nt">-o</span> /dev/null <span class="nt">-s</span> <span class="nt">-w</span> <span class="s2">"time_total:%{time_total} time_connect:%{time_connect}"</span> <span class="nv">$1</span>
</code></pre></div></div>
<p>This bash script takes one parameter ($1) for the curl command. Curl will then return the total transaction time (time_total) and the connection time (time_connect).</p>
<h4 id="data-collector">Data Collector</h4>
<p>Add a new <strong>Data Collector</strong> under Data Collection. This new data collector will start the bash script and return the data to Cacti.</p>
<ol>
<li>Select Script/Command as input type</li>
<li>Point it to the script you just added.</li>
<li>Add two output fields, which should point to the two fields returned by the script (time_connect and time_total).</li>
</ol>
<p><img src="/assets/images/monitor-cacti/collector1.jpg" alt="Data Collector" /></p>
<h4 id="graph-template-and-add-to-device">Graph Template and add to device</h4>
<p>Now similar as for the graphing of MISP information, add a new graph template and include the HTTP response code data source. Afterwards add the graph template to your device, and create a new graph based on this template.</p>
<p><img src="/assets/images/monitor-cacti/httpresponse.jpg" alt="HTTP Response" /></p>
<h2 id="dashboard">Dashboard</h2>
<p>If all goes well, you should be able to build a dashboard in Cacti, representing the crucial MISP values.</p>
<p><img src="/assets/images/monitor-cacti/dashboard.jpg" alt="Cacti Dashboard" /></p>2020-08-21T23:00:00+00:00https://www.misp-project.org/2020/08/21/MISP.2.4.130.releasedMISP - MISP 2.4.130 released (Various fixes, performance improvements and new features)2020-08-20T23:00:00+00:00<h1 id="misp-24130-released">MISP 2.4.130 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.130">2.4.130</a>) has been released with performance improvements, multiple bugs fixed and new features.</p>
<h1 id="speed-improvements">Speed improvements</h1>
<ul>
<li>[internal] cache tags instead of loading them over and over via the
event fetcher, fixes #6201.
<ul>
<li>should speed things up for exports of datasets that have a lot of recurring tags</li>
<li>moved the caching of some internals to the appmodel level to make it more generic</li>
</ul>
</li>
<li>[internal] Update correlations in one query.
Before, for every event saving action, four queries for updating correlations were generated</li>
<li>[correlations] Faster loading related attributes.</li>
<li>[sync] drop the republishing of events when the modification is merely
a timestamp bump.
<ul>
<li>due to an already fixed issue still lingering, invalid event edits keep getting synchronised between instances</li>
<li>these events still generate publish alerts erroneously</li>
<li>this fix compares the previous state of the event to the modification, if there are no material changes (attributes, objects, object relations, event tags added/updated) then the publishing is dropped.</li>
</ul>
</li>
</ul>
<h1 id="api-improvements">API improvements</h1>
<ul>
<li>Allow tag deletion for an event on update</li>
<li>Allow for attribute tag deletion via Event or Attribute edit. Clean and return the attribute tags on response from editing an attribute, update code to remove legacy</li>
<li>[opendata export] Parsing portal url parameter + slight parameters
parsing changes.
<ul>
<li>As the possibility of specifying the url of the
Open data portal to use instead of the default
one, we support here this parameter and adapt
the way we build the command that will launch
the python script</li>
<li>Slight changes to replace some isset tests by
empty tests to make sure the concerned fields
are not only set, but also contain a value</li>
</ul>
</li>
</ul>
<h1 id="improvements">Improvements</h1>
<ul>
<li>[UI] Show event preview when merging.</li>
<li>[attribute] Add support for IDN domains.</li>
<li>New: [freetext] Convert <code class="highlighter-rouge">[at]</code> to <code class="highlighter-rouge">@</code> and <code class="highlighter-rouge">hxtp</code> and <code class="highlighter-rouge">htxp</code> to <code class="highlighter-rouge">http</code></li>
<li>[widgets] Additional widgets for sharing statistics and layouts.</li>
<li>[CLI] Allow to fetch remove event by UUID.</li>
<li>[stix import] Fixed port in ip-port objects import to lose src and dst
context.</li>
<li>[stix export] Fixed the slight difference between parsing x509
fingerprint attributes and x509 objects.</li>
<li>[stix export] Fixed x509 fingerprint attributes export & moved mapping
dictionaries to the mapping script
<ul>
<li>Only the x509-fingerprint-sha1 attribute was
exported, and as a standard sha1 attribute,
which was a loss of context, now the x509
fingerprint attributes (md5, sha1 & sha256) are
exported as expected within a x509 observable</li>
<li>Also moved the mapping dictionaries with the
appropriate indent to the mapping script, where
they should belong</li>
</ul>
</li>
</ul>
<h1 id="many-bugs-fixed-and-small-improvements">Many bugs fixed and small improvements</h1>
<p>Many other improvements are documented in the <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a>.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2020-08-20T23:00:00+00:00https://www.misp-project.org/2020/08/18/MISP-Monitoring-with-OpenNMSMISP - MISP service monitoring (and a bit of healing) with OpenNMS2020-08-17T23:00:00+00:00<h1 id="misp-service-monitoring-and-a-bit-of-healing-with-opennms">MISP service monitoring (and a bit of healing) with OpenNMS</h1>
<h2 id="introduction">Introduction:</h2>
<p>Many organisations adore how quick and easy MISP can be set up. Once it’s running, people start integrating it into their processes and begin to rely on it, for instance by exporting indicators and using them in security or network focused software. Usually this is the time when MISP becomes a fundamental part in the portfolio of fighting attacks, and the need for reliability grows rapidly.</p>
<p>This blog post shows how MISP as a service can be monitored easily with OpenNMS, in order to show outages or slowness in answering requests. But we don’t stop there. OpenNMS can also be used to repair components that might need a poke here and there</p>
<h2 id="requirements">Requirements:</h2>
<h3 id="misp">MISP</h3>
<p>Any (recent) MISP installation is perfectly fitting the requirements to reproduce what’s demonstrated in this article.</p>
<h3 id="opennms">OpenNMS</h3>
<p>The free and open source <a href="https://www.opennms.com/distributions/">OpenNMS Horizon</a> in version 26.1.1 is used for the purpose of this article.</p>
<h2 id="implementation">Implementation</h2>
<p>Assuming you have both a working MISP and an OpenNMS instance running, we can jump straight to the specific monitoring parts of the configuration process.</p>
<h3 id="icmp-monitoring">ICMP monitoring</h3>
<p>This is the most simple form of monitoring in OpenNMS. It will be enabled by default and checks if the machine hosting MISP will be answering ICMP (‘ping’) packets. ICMP monitoring acts more like an on/off-switch monitoring, but it can also tell you statistically and historically something about the load of the machine and the network conditions due to the recorded response times.</p>
<p><img src="/assets/images/opennms/sc-icmp-response_time.png" alt="ICMP Response time statistics" /></p>
<h3 id="https-monitoring">HTTP(S) monitoring</h3>
<p>HTTP and HTTPS monitoring are also built-in into OpenNMS and activated by default if the server exposed TCP ports 80 and 443 during the initial scan. This check is quite handy to see if the web server is running, but doesn’t tell you if the application behind this web server is acting properly.</p>
<p>As in ICMP monitoring, OpenNMS is collecting the data over time and is able to give us an historic view on the response times without any additional configuration.</p>
<p><img src="/assets/images/opennms/sc-http-s-response_time.png" alt="HTTP(S) Response time statistics" /></p>
<h3 id="application-monitoring">Application monitoring</h3>
<h4 id="simple-https-statusoutput-monitoring">Simple HTTPS status/output monitoring</h4>
<p>Here we are going into more detail. We would like to see if the Login screen of MISP (<code class="highlighter-rouge">url</code> key) returns an HTTP status code in the 200 range (<code class="highlighter-rouge">response</code> key) and if the content contains the word ‘Login’ (<code class="highlighter-rouge">response-text</code> key).</p>
<p>This configuration is to be adjusted (especially the <code class="highlighter-rouge">host-name</code> key) and to be put into <code class="highlighter-rouge">poller-configuration.xml</code></p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code> <service name="misppriv" interval="300000" user-defined="false" status="on">
<parameter key="retry" value="1"/>
<parameter key="timeout" value="3000"/>
<parameter key="port" value="443"/>
<parameter key="host-name" value="misppriv.circl.lu"/>
<parameter key="url" value="/users/login"/>
<parameter key="response" value="200-202,299"/>
<parameter key="response-text" value="~.*Login.*"/>
</service>
<monitor service="misppriv" class-name="org.opennms.netmgt.poller.monitors.HttpsMonitor"/>
</code></pre></div></div>
<p>After adding a service to <code class="highlighter-rouge">poller-configuration.xml</code> it is necessary to perform two additional steps:</p>
<ol>
<li>
<p>restart OpenNMS or execute the following command <code class="highlighter-rouge">/opt/opennms/bin/send-event.pl -p 'daemonName Pollerd' uei.opennms.org/internal/reloadDaemonConfig</code></p>
</li>
<li>
<p>Add in OpenNMS web interface’s <code class="highlighter-rouge">Provisioning Requisitions</code> the newly created service (<code class="highlighter-rouge">misppriv</code> in this example) as a service to the interface of the specific node, and synchronize the database.</p>
</li>
</ol>
<p>The first step is also needed every time a configuration change has been done to <code class="highlighter-rouge">poller-configuration.xml</code>.</p>
<h4 id="rest-interface-monitoring">REST interface monitoring</h4>
<p>We can also monitor if the underlying REST interface is working properly.</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code> <service name="misppriv-rest" interval="300000" user-defined="false" status="on">
<parameter key="script" value="/etc/opennms/monitoring-scripts/misp-rest.sh"/>
<parameter key="args" value="misppriv.circl.lu YOURAPIKEYHERE"/>
<parameter key="banner" value="OK"/>
<parameter key="retry" value="2"/>
<parameter key="timeout" value="10000"/>
<parameter key="rrd-base-name" value="monitoring-script"/>
<parameter key="rrd-repository" value="/var/lib/opennms/rrd/response"/>
</service>
<monitor service="misppriv-rest" class-name="org.opennms.netmgt.poller.monitors.SystemExecuteMonitor"/>
</code></pre></div></div>
<p>Since the following tests are a bit too specific for the default monitoring capabilities of OpenNMS, we are helping ourselves with an external monitoring script which is placed in the subdirectory <code class="highlighter-rouge">monitoring-scripts</code>. The content of the file is the following:</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="c">#!/bin/bash</span>
<span class="nv">HOST</span><span class="o">=</span><span class="s2">"</span><span class="nv">$1</span><span class="s2">"</span>
<span class="nv">KEY</span><span class="o">=</span><span class="s2">"</span><span class="nv">$2</span><span class="s2">"</span>
<span class="nv">RESP</span><span class="o">=</span><span class="k">$(</span>/usr/bin/curl <span class="nt">-H</span> <span class="s2">"Authorization: </span><span class="k">${</span><span class="nv">KEY</span><span class="k">}</span><span class="s2">"</span> <span class="nt">-H</span> <span class="s2">"Accept: application/json"</span> <span class="nt">-H</span> <span class="s2">"Content-type: application/json"</span> https://<span class="k">${</span><span class="nv">HOST</span><span class="k">}</span>/events/index/limit:60/page:1/searchminimal:1<span class="k">)</span>
<span class="k">if</span> <span class="o">[[</span> <span class="s2">"</span><span class="k">${</span><span class="nv">RESP</span><span class="k">}</span><span class="s2">"</span> <span class="o">=</span>~ <span class="s1">'uid'</span> <span class="o">]]</span><span class="p">;</span> <span class="k">then
</span><span class="nb">echo</span> <span class="s2">"OK"</span>
<span class="nb">exit </span>0
<span class="k">else
</span><span class="nb">echo</span> <span class="s2">"KO"</span>
<span class="nb">exit </span>1
<span class="k">fi</span>
</code></pre></div></div>
<p>It requests the REST equivalent of the Event Index view of MISP. If something goes wrong and the page doesn’t contain the term <code class="highlighter-rouge">uid</code> it will report a failure. Please note the <code class="highlighter-rouge">timeout</code> key whose value is set to <code class="highlighter-rouge">10000</code> (10 seconds). That means we give MISP a good amount of time to reply, even under heavy load.</p>
<h4 id="rest-interface-slow">REST interface slow</h4>
<p>We can use the same concept as in the example before to monitor if the REST interface is slow.</p>
<p>The sole difference is the <code class="highlighter-rouge">timeout</code> key’s value of <code class="highlighter-rouge">5000</code> or 5 seconds. If it takes longer, OpenNMS will show for you to know and to analyse the cause that the REST interface is slow.</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code> <service name="misppriv-rest-slow" interval="300000" user-defined="false" status="on">
<parameter key="script" value="/etc/opennms/monitoring-scripts/misp-rest.sh"/>
<parameter key="args" value="misppriv.circl.lu YOURAPIKEYHERE"/>
<parameter key="banner" value="OK"/>
<parameter key="retry" value="2"/>
<parameter key="timeout" value="5000"/>
<parameter key="rrd-base-name" value="monitoring-script"/>
<parameter key="rrd-repository" value="/var/lib/opennms/rrd/response"/>
</service>
<monitor service="misppriv-rest-slow" class-name="org.opennms.netmgt.poller.monitors.SystemExecuteMonitor"/>
</code></pre></div></div>
<h4 id="misp-worker-monitoring-and-a-bit-of-self-healing">MISP worker monitoring (and a bit of self-healing)</h4>
<p>MISP workers take care of the processing of various tasks around MISP. The most intuitive is the dispatching of Emails to all subscribed users once an event is published.
If can be annoying if MISP workers die and it’s not immediately observed and reacted to. This happens from time to time and can be fixed with a simple restart of the workers, for instance from the web interface.</p>
<p>To be able to react quickly to such an outage, we can configure a test in OpenNMS:</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code> <service name="misppriv-worker" interval="300000" user-defined="false" status="on">
<parameter key="script" value="/etc/opennms/monitoring-scripts/misp-worker.sh"/>
<parameter key="args" value="misppriv.circl.lu YOURAPIKEYHERE"/>
<parameter key="banner" value="OK"/>
<parameter key="retry" value="2"/>
<parameter key="timeout" value="5000"/>
<parameter key="rrd-base-name" value="monitoring-script"/>
<parameter key="rrd-repository" value="/var/lib/opennms/rrd/response"/>
</service>
<monitor service="misppriv-worker" class-name="org.opennms.netmgt.poller.monitors.SystemExecuteMonitor"/>
</code></pre></div></div>
<p>Again, this test is using an external script placed in <code class="highlighter-rouge">monitoring-scripts</code>. The file has the following content:</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="c">#!/bin/bash</span>
<span class="nv">HOST</span><span class="o">=</span><span class="s2">"</span><span class="nv">$1</span><span class="s2">"</span>
<span class="nv">KEY</span><span class="o">=</span><span class="s2">"</span><span class="nv">$2</span><span class="s2">"</span>
<span class="nv">RESP</span><span class="o">=</span><span class="k">$(</span>/usr/bin/curl <span class="nt">-H</span> <span class="s2">"Authorization: </span><span class="k">${</span><span class="nv">KEY</span><span class="k">}</span><span class="s2">"</span> <span class="nt">-H</span> <span class="s2">"Accept: application/json"</span> <span class="nt">-H</span> <span class="s2">"Content-type: application/json"</span> https://<span class="k">${</span><span class="nv">HOST</span><span class="k">}</span>/servers/getWorkers | jq <span class="s1">'.[].workers[].ok'</span><span class="k">)</span>
<span class="k">if</span> <span class="o">[[</span> <span class="s2">"</span><span class="k">${</span><span class="nv">RESP</span><span class="k">}</span><span class="s2">"</span> <span class="o">=</span>~ <span class="s1">'false'</span> <span class="o">]]</span><span class="p">;</span> <span class="k">then
</span><span class="nb">echo</span> <span class="s2">"KO"</span>
<span class="nb">exit </span>1 <span class="c"># to record the outage</span>
<span class="k">else
</span><span class="nb">echo</span> <span class="s2">"OK"</span>
<span class="nb">exit </span>0
<span class="k">fi</span>
</code></pre></div></div>
<p>This test is checking the worker’s status through the REST API. If the answer from the server contains the term <code class="highlighter-rouge">false</code>, OpenNMS will record an outage for you to react and restart the MISP workers.</p>
<p>It is also possible to let this OpenNMS monitoring script restart the workers once a failure has been recorded. Just modify the aforementioned script and add two lines:</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="c">#!/bin/bash</span>
<span class="nv">HOST</span><span class="o">=</span><span class="s2">"</span><span class="nv">$1</span><span class="s2">"</span>
<span class="nv">KEY</span><span class="o">=</span><span class="s2">"</span><span class="nv">$2</span><span class="s2">"</span>
<span class="nv">RESP</span><span class="o">=</span><span class="k">$(</span>/usr/bin/curl <span class="nt">-H</span> <span class="s2">"Authorization: </span><span class="k">${</span><span class="nv">KEY</span><span class="k">}</span><span class="s2">"</span> <span class="nt">-H</span> <span class="s2">"Accept: application/json"</span> <span class="nt">-H</span> <span class="s2">"Content-type: application/json"</span> https://<span class="k">${</span><span class="nv">HOST</span><span class="k">}</span>/servers/getWorkers | jq <span class="s1">'.[].workers[].ok'</span><span class="k">)</span>
<span class="nv">RESTART</span><span class="o">=</span><span class="k">$(</span>/usr/bin/curl <span class="nt">-d</span> <span class="s1">'{}'</span> <span class="nt">-H</span> <span class="s2">"Authorization: </span><span class="k">${</span><span class="nv">KEY</span><span class="k">}</span><span class="s2">"</span> <span class="nt">-H</span> <span class="s2">"Accept: application/json"</span> <span class="nt">-H</span> <span class="s2">"Content-type: application/json"</span> <span class="nt">-X</span> POST https://<span class="k">${</span><span class="nv">HOST</span><span class="k">}</span>/servers/restartDeadWorkers<span class="k">)</span>
<span class="k">if</span> <span class="o">[[</span> <span class="s2">"</span><span class="k">${</span><span class="nv">RESP</span><span class="k">}</span><span class="s2">"</span> <span class="o">=</span>~ <span class="s1">'false'</span> <span class="o">]]</span><span class="p">;</span> <span class="k">then
</span><span class="nb">echo</span> <span class="s2">"KO"</span>
<span class="k">${</span><span class="nv">RESTART</span><span class="k">}</span>
<span class="nb">exit </span>1 <span class="c"># to record the outage</span>
<span class="k">else
</span><span class="nb">echo</span> <span class="s2">"OK"</span>
<span class="nb">exit </span>0
<span class="k">fi</span>
</code></pre></div></div>
<p>The API call <code class="highlighter-rouge">/servers/restartDeadWorkers</code> will take care in most of the cases of your broken workers.</p>
<h2 id="summary">Summary</h2>
<p>MISP and OpenNMS is a grateful combination of Open Source projects. They play very well together and with moderate configuration effort it is possible to monitor services in great detail, tailored to the needs of the application owner. OpenNMS’ extensibility through external monitoring scripts and the open approach of MISP exposing health-checking functions (and a lot more) through it’s REST API are complementing the experience.</p>2020-08-17T23:00:00+00:00https://www.misp-project.org/2020/07/31/MISP-galaxy-101MISP - Creating a MISP Galaxy, 1012020-07-30T23:00:00+00:00<h2 id="misp-galaxies">MISP Galaxies</h2>
<p>MISP Galaxies and Clusters are an easy way to add context to data. Compared to the relatively simple concept of tags and taxonomies, they allow you to add more complex data structures. There is already a large list of galaxies and clusters available as a <a href="https://github.com/MISP/misp-galaxy">community effort</a>, and directly accessible within <a href="https://github.com/MISP/MISP">MISP</a>, but it’s always possible these do not fully address your needs.</p>
<p>So how to add your own cluster and galaxy? There are <a href="https://github.com/MISP/misp-galaxy/blob/main/CONTRIBUTE.md">contribution guidelines</a> but these do not describe how to start from scratch. This post attempts to get you started with developing your own MISP galaxy and cluster.</p>
<h2 id="concepts">Concepts</h2>
<p>First some basic concepts</p>
<ul>
<li>Galaxies are stored in <strong>namespaces</strong>;</li>
<li>A <strong>galaxy</strong> describes the <strong>data</strong>, it contains the metadata;</li>
<li>The <strong>cluster</strong> is the individual instance of the galaxy and contains the data elements;</li>
<li>A cluster consists of <strong>elements</strong>, which are the “real” data;</li>
<li>Besides their description and <strong>value</strong>, these elements can contain <strong>synonyms</strong> and <strong>references</strong> to other clusters (elements).</li>
</ul>
<p><img src="/assets/images/galaxy101/galaxy.jpg" alt="Galaxy concepts." /></p>
<p>There are two types of galaxies, the <strong>regular</strong> galaxy and the <strong>matrix</strong> galaxy.</p>
<p><img src="/assets/images/galaxy101/galaxy-regular.jpg" alt="Galaxy regular." /></p>
<p><img src="/assets/images/galaxy101/galaxy-matrix.jpg" alt="Galaxy matrix." /></p>
<p>The difference between both is already clear when you add them in the MISP interface. In essence the matrix style galaxies allow you to select -multiple- values in a matrix-style like (obvious, right?), whereas the regular galaxy is a straightforward element from a list. You will most likely recognise these matrix types from the galaxies used to represent the <a href="https://attack.mitre.org/">MITRE ATT&CK Framework</a></p>
<p>Galaxies and clusters are stored in JSON files, one in the <strong>directory galaxies</strong>, and one in the <strong>directory clusters</strong>.</p>
<p>The name of the JSON file in both directories needs to be the same.</p>
<h2 id="demo-case">Demo case</h2>
<p>For this demo I will use the Segregation (or separation) of Duties (SoD) Matrix for CSIRTs, LEA and Judiciary as an example to build a new matrix. The <a href="https://github.com/cudeso/SoD-Matrix">SoD matrix</a> is a method to assign for different actors their roles and duties during the cybercrime investigation lifecycle phases.</p>
<p>The SoD matrix consists of three phases (prior, during and post incident), four actors and then for each of these actors’different roles and duties.</p>
<h2 id="build-your-own-galaxy">Build your own galaxy</h2>
<h3 id="fork-the-repository">Fork the repository</h3>
<p>Because the goal is to contribute the new galaxy and cluster to the community, it’s best to first fork the <a href="https://github.com/MISP/misp-galaxy">Galaxy Github repository</a>, add the changes to the local copy and then submit the changes as a pull request.</p>
<h3 id="create-the-files">Create the files</h3>
<p>For this new galaxy there are two new files which need to be created. In a default MISP install you can find these files under <strong>/var/www/MISP/app/files/misp-galaxy</strong> but you can also use the location where you created the local copy of the Github repository.</p>
<div class="language-json highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="err">touch</span><span class="w"> </span><span class="err">galaxies/sod-matrix.json</span><span class="w">
</span><span class="err">touch</span><span class="w"> </span><span class="err">clusters/sod-matrix.json</span><span class="w">
</span></code></pre></div></div>
<h3 id="pick-your-namespace">Pick your namespace</h3>
<p>The first step is to select a <strong>namespace</strong>. A galaxy can be added to an existing namespace, or to a new one. From a functionality point there is no real difference. Consider the namespace as the container for the galaxy. Because there is no namespace which fits the SoD matrix, I will use a new namespace. This namespace is defined in the galaxy file.</p>
<div class="language-json highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="err">galaxies/sod-matrix.json</span><span class="w">
</span><span class="p">{</span><span class="w">
</span><span class="s2">"namespace"</span><span class="p">:</span><span class="w"> </span><span class="s2">"sod-matrix"</span><span class="w">
</span><span class="p">}</span><span class="w">
</span></code></pre></div></div>
<h3 id="matrix">Matrix</h3>
<p>The next step is to make sure this galaxy is a matrix galaxy type. They keyword to use is <strong>kill_chain_order</strong>. This field has to contain one or more named tables, with the category labels. Each table is one “tab” in the matrix. In the SoD example, there are three phases which will be represented in tabs (named tables), and each phase contains the four actors (category labels).</p>
<div class="language-json highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="err">galaxies/sod-matrix.json</span><span class="w">
</span><span class="p">{</span><span class="w">
</span><span class="s2">"kill_chain_order"</span><span class="p">:</span><span class="w"> </span><span class="p">{</span><span class="w">
</span><span class="s2">"during-incident-crime"</span><span class="p">:</span><span class="w"> </span><span class="p">[</span><span class="w">
</span><span class="s2">"CSIRT"</span><span class="p">,</span><span class="w">
</span><span class="s2">"LEA"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Judiciary"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Prosecutors"</span><span class="w">
</span><span class="p">],</span><span class="w">
</span><span class="s2">"post-incident-crime"</span><span class="p">:</span><span class="w"> </span><span class="p">[</span><span class="w">
</span><span class="s2">"CSIRT"</span><span class="p">,</span><span class="w">
</span><span class="s2">"LEA"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Judiciary"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Prosecutors"</span><span class="w">
</span><span class="p">],</span><span class="w">
</span><span class="s2">"prior-to-incident-crime"</span><span class="p">:</span><span class="w"> </span><span class="p">[</span><span class="w">
</span><span class="s2">"CSIRT"</span><span class="p">,</span><span class="w">
</span><span class="s2">"LEA"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Judiciary"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Prosecutors"</span><span class="w">
</span><span class="p">]</span><span class="w">
</span><span class="p">},</span><span class="w">
</span><span class="s2">"namespace"</span><span class="p">:</span><span class="w"> </span><span class="s2">"sod-matrix"</span><span class="w">
</span><span class="p">}</span><span class="w">
</span></code></pre></div></div>
<h3 id="universally-unique-identifier">Universally unique identifier</h3>
<p>All objects in MISP have a UUID, a universally unique identifier. Galaxies (and clusters) are no different. You can generate these UUIDs with the Linux command uuidgen.</p>
<div class="language-json highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="err">galaxies/sod-matrix.json</span><span class="w">
</span><span class="p">{</span><span class="w">
</span><span class="s2">"kill_chain_order"</span><span class="p">:</span><span class="w"> </span><span class="p">{</span><span class="w">
</span><span class="s2">"during-incident-crime"</span><span class="p">:</span><span class="w"> </span><span class="p">[</span><span class="w">
</span><span class="s2">"CSIRT"</span><span class="p">,</span><span class="w">
</span><span class="s2">"LEA"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Judiciary"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Prosecutors"</span><span class="w">
</span><span class="p">],</span><span class="w">
</span><span class="s2">"post-incident-crime"</span><span class="p">:</span><span class="w"> </span><span class="p">[</span><span class="w">
</span><span class="s2">"CSIRT"</span><span class="p">,</span><span class="w">
</span><span class="s2">"LEA"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Judiciary"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Prosecutors"</span><span class="w">
</span><span class="p">],</span><span class="w">
</span><span class="s2">"prior-to-incident-crime"</span><span class="p">:</span><span class="w"> </span><span class="p">[</span><span class="w">
</span><span class="s2">"CSIRT"</span><span class="p">,</span><span class="w">
</span><span class="s2">"LEA"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Judiciary"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Prosecutors"</span><span class="w">
</span><span class="p">]</span><span class="w">
</span><span class="p">},</span><span class="w">
</span><span class="s2">"namespace"</span><span class="p">:</span><span class="w"> </span><span class="s2">"sod-matrix"</span><span class="p">,</span><span class="w">
</span><span class="s2">"uuid"</span><span class="p">:</span><span class="w"> </span><span class="s2">"50104ead-7315-457c-b596-b4471cabf28b"</span><span class="w">
</span><span class="p">}</span><span class="w">
</span></code></pre></div></div>
<h3 id="galaxy-meta-data">Galaxy meta data</h3>
<p>The final step in creating the galaxy file is adding a <strong>description</strong>, <strong>name</strong>, <strong>version</strong> and <strong>icon</strong>. Description and name are text fields, version is a numeric field indicating the version of your galaxy. The icon is one of the Font Awesome icons, without the prefix ‘fa’.</p>
<p>An important meta data field is the <strong>type</strong> field. This has to have the same value as the galaxy and cluster file names and is what glues the galaxy file and cluster file together.</p>
<div class="language-json highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="err">galaxies/sod-matrix.json</span><span class="w">
</span><span class="p">{</span><span class="w">
</span><span class="s2">"description"</span><span class="p">:</span><span class="w"> </span><span class="s2">"SoD Matrix"</span><span class="p">,</span><span class="w">
</span><span class="s2">"icon"</span><span class="p">:</span><span class="w"> </span><span class="s2">"map"</span><span class="p">,</span><span class="w">
</span><span class="s2">"kill_chain_order"</span><span class="p">:</span><span class="w"> </span><span class="p">{</span><span class="w">
</span><span class="s2">"during-incident-crime"</span><span class="p">:</span><span class="w"> </span><span class="p">[</span><span class="w">
</span><span class="s2">"CSIRT"</span><span class="p">,</span><span class="w">
</span><span class="s2">"LEA"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Judiciary"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Prosecutors"</span><span class="w">
</span><span class="p">],</span><span class="w">
</span><span class="s2">"post-incident-crime"</span><span class="p">:</span><span class="w"> </span><span class="p">[</span><span class="w">
</span><span class="s2">"CSIRT"</span><span class="p">,</span><span class="w">
</span><span class="s2">"LEA"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Judiciary"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Prosecutors"</span><span class="w">
</span><span class="p">],</span><span class="w">
</span><span class="s2">"prior-to-incident-crime"</span><span class="p">:</span><span class="w"> </span><span class="p">[</span><span class="w">
</span><span class="s2">"CSIRT"</span><span class="p">,</span><span class="w">
</span><span class="s2">"LEA"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Judiciary"</span><span class="p">,</span><span class="w">
</span><span class="s2">"Prosecutors"</span><span class="w">
</span><span class="p">]</span><span class="w">
</span><span class="p">},</span><span class="w">
</span><span class="s2">"name"</span><span class="p">:</span><span class="w"> </span><span class="s2">"SoD Matrix"</span><span class="p">,</span><span class="w">
</span><span class="s2">"namespace"</span><span class="p">:</span><span class="w"> </span><span class="s2">"sod-matrix"</span><span class="p">,</span><span class="w">
</span><span class="s2">"type"</span><span class="p">:</span><span class="w"> </span><span class="s2">"sod-matrix"</span><span class="p">,</span><span class="w">
</span><span class="s2">"uuid"</span><span class="p">:</span><span class="w"> </span><span class="s2">"50104ead-7315-457c-b596-b4471cabf28b"</span><span class="p">,</span><span class="w">
</span><span class="s2">"version"</span><span class="p">:</span><span class="w"> </span><span class="mi">1</span><span class="w">
</span><span class="p">}</span><span class="w">
</span></code></pre></div></div>
<h2 id="create-the-cluster">Create the cluster</h2>
<h3 id="cluster-file">Cluster file</h3>
<p>It’s now time to start with the cluster file. For the SoD matrix, the elements will not contain synonyms or references to other objects.</p>
<h3 id="metadata">Metadata</h3>
<p>Before jumping to the meat of the cluster, the values (or elements), we first have to add some metadata for the cluster. This is similar as the information previously added for galaxies. It includes a description, name, version and UUID.</p>
<p>Besides this information, it also needs additional text fields such as <strong>author</strong>, <strong>category</strong> and <strong>source</strong>. The category can be any descriptive text you prefer. The source can point to an external resource providing more details on the content of the galaxy.</p>
<div class="language-json highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="err">clusters/sod-matrix.json</span><span class="w">
</span><span class="p">{</span><span class="w">
</span><span class="s2">"authors"</span><span class="p">:</span><span class="w"> </span><span class="p">[</span><span class="w">
</span><span class="s2">"Koen Van Impe"</span><span class="w">
</span><span class="p">],</span><span class="w">
</span><span class="s2">"category"</span><span class="p">:</span><span class="w"> </span><span class="s2">"sod-matrix"</span><span class="p">,</span><span class="w">
</span><span class="s2">"description"</span><span class="p">:</span><span class="w"> </span><span class="s2">"SOD Matrix"</span><span class="p">,</span><span class="w">
</span><span class="s2">"name"</span><span class="p">:</span><span class="w"> </span><span class="s2">"sod-matrix"</span><span class="p">,</span><span class="w">
</span><span class="s2">"source"</span><span class="p">:</span><span class="w"> </span><span class="s2">"https://github.com/cudeso/SoD-Matrix"</span><span class="p">,</span><span class="w">
</span><span class="s2">"type"</span><span class="p">:</span><span class="w"> </span><span class="s2">"sod-matrix"</span><span class="p">,</span><span class="w">
</span><span class="s2">"uuid"</span><span class="p">:</span><span class="w"> </span><span class="s2">"f0b6036d-020d-414b-9761-ee5a972d2362"</span><span class="p">,</span><span class="w">
</span><span class="s2">"version"</span><span class="p">:</span><span class="w"> </span><span class="mi">1</span><span class="w">
</span><span class="p">}</span><span class="w">
</span></code></pre></div></div>
<h3 id="add-the-matrix-values">Add the matrix values</h3>
<p>The next step is the biggest challenge, adding the values (elements) in a <strong>matrix format</strong> to the cluster. The values are stored in a table format.</p>
<div class="language-json highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="w"> </span><span class="s2">"values"</span><span class="p">:</span><span class="w"> </span><span class="p">[</span><span class="w">
</span><span class="p">]</span><span class="w">
</span></code></pre></div></div>
<p>The content of each element in that value table consists of a number of required fields. It should contain a <strong>description</strong>, a <strong>UUID</strong>, a <strong>value</strong> and <strong>metadata</strong>. Whereas the value is the label being displayed when you add the galaxy to an event, the description is only shown when you hover above the value in the matrix selection. Make the value as meaningful as possible as that’s the one being displayed on the event level. Also take into account that MISP sorts the values in the matrix alphabetically.</p>
<p>What remains is linking the values to the correct matrix tab and matrix column. This is achieved with the meta value <strong>kill_chain</strong>. The kill_chain field consists of two parts [“<strong>tab</strong>:<strong>column</strong>”]. The two parts are separated with a colon (:). When I created the galaxy, I used “during-incident-crime, post-incident-crime and prior-to-incident-crime” as the <strong>tabs</strong> and I set CSIRT, LEA, Judiciary, and Prosecutors as the <strong>columns</strong>. A sample of one value would then look like this</p>
<div class="language-json highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="w"> </span><span class="p">{</span><span class="w">
</span><span class="s2">"description"</span><span class="p">:</span><span class="w"> </span><span class="s2">"Development and distribution of tools for preventive and reactive mitigation"</span><span class="p">,</span><span class="w">
</span><span class="s2">"meta"</span><span class="p">:</span><span class="w"> </span><span class="p">{</span><span class="w">
</span><span class="s2">"kill_chain"</span><span class="p">:</span><span class="w"> </span><span class="p">[</span><span class="w">
</span><span class="s2">"prior-to-incident-crime:CSIRT"</span><span class="w">
</span><span class="p">]</span><span class="w">
</span><span class="p">},</span><span class="w">
</span><span class="s2">"uuid"</span><span class="p">:</span><span class="w"> </span><span class="s2">"70437783-b605-4721-9cdb-97083f99d8c1"</span><span class="p">,</span><span class="w">
</span><span class="s2">"value"</span><span class="p">:</span><span class="w"> </span><span class="s2">"Analysis of vulnerabilities and threats - CSIRT - [C]"</span><span class="w">
</span><span class="p">},</span><span class="w">
</span></code></pre></div></div>
<p>This will put “Analysis of vulnerabilities and threats” in the column “CSIRT” in the tab “prior-to-incident-crime”.</p>
<p><img src="/assets/images/galaxy101/cluster-value.jpg" alt="Cluster value." /></p>
<h2 id="automation-sort-of-">Automation, sort of …</h2>
<p>The SoD matrix consists of a lot of values per column, and per tab. The reason is that the SoD matrix can be different for each country or context. For example, the duty ‘delivering training’ can be done by actor CSIRT in a “R-Responsible” role in country A, whereas the same duty and actor might have the role “C-Consulted” in country B. In practice this meant that I had to add each combination of duty and role for all actors. Needless to say this is a lot of copy and paste work which is better left to a script.</p>
<p>The script that I use to create the cluster is inspired on <a href="https://github.com/enisaeu/Reference-Security-Incident-Taxonomy-Task-Force/blob/master/contrib/machinetag2human.py">machinetag2human.py</a> used to transform the Reference Security Incident Taxonomy from a machine readable format to a human readable format. I altered the <a href="https://github.com/cudeso/SoD-Matrix/blob/master/machinetag2human.py">code</a> a bit so that it can now write a human readable format of the SoD matrix, as well as create the JSON files for the galaxy and cluster. More info can be found in the repository of the <a href="https://github.com/cudeso/SoD-Matrix">SoD matrix</a>.</p>
<p>Automating the creation of the cluster (and galaxy) files is highly advised.</p>
<ol>
<li>Create one “master” JSON file which holds all the values you want to see in the matrix;</li>
<li>Create the galaxy and cluster from this “master” file.</li>
</ol>
<h2 id="validating-the-work">Validating the work</h2>
<p>Once the galaxy and cluster files are created, what’s left to do is to <strong>validate</strong> the JSON files. From within the folder misp-galaxy</p>
<div class="language-json highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="p">:</span><span class="err">/var/www/MISP/app/files/misp-galaxy#</span><span class="w"> </span><span class="err">./validate_all.sh</span><span class="w">
</span><span class="p">:</span><span class="err">/var/www/MISP/app/files/misp-galaxy#</span><span class="w"> </span><span class="err">./jq_all_the_things.sh</span><span class="w">
</span></code></pre></div></div>
<p>If no errors occur, it’s best to first test the result on your local MISP. Make sure that MISP recognises the newly created galaxies.</p>
<div class="language-json highlighter-rouge"><div class="highlight"><pre class="highlight"><code><span class="err">sudo</span><span class="w"> </span><span class="err">-u</span><span class="w"> </span><span class="err">www-data</span><span class="w"> </span><span class="err">/var/www/MISP/app/Console/cake</span><span class="w"> </span><span class="err">Admin</span><span class="w"> </span><span class="err">updateGalaxies</span><span class="w"> </span><span class="err">force</span><span class="w">
</span></code></pre></div></div>
<p>The newly created matrix should then be visible under <strong>Galaxies</strong>, <strong>List Galaxies</strong>.</p>
<p><img src="/assets/images/galaxy101/sodmatrix.jpg" alt="SoD Matrix." /></p>
<p>If all looks good, you can do a pull request to make sure the next galaxy is available for the MISP community.</p>2020-07-30T23:00:00+00:00https://www.misp-project.org/2020/07/30/publishing-open-data-using-MISPMISP - Publishing open data from MISP2020-07-29T23:00:00+00:00<h1 id="publish-data-on-open-data-portals-with-misp">Publish data on Open data portals with MISP</h1>
<h2 id="the-open-data-format">The Open data format</h2>
<p>Open data defines the idea of making some data freely available for everyone to use with a possibility of redistribution in any form.
The open data format provides metadata information describing the datasets along with resources stored within the portal.</p>
<p><strong>Datasets</strong> are the containers used to give a general description of the data stored within the resources.
A dataset has some mandatory fields that must be defined by its creator:</p>
<ul>
<li><strong>title</strong>: A one sentence description to identity the purpose of the dataset</li>
<li><strong>description</strong>: A short description giving more details about the dataset</li>
<li><strong>update frequency</strong>: The frequency of update for the dataset</li>
</ul>
<p>Some additional mandatory fields are generated by the portal at the creation or update of the dataset, such as the creation date, the date of last modification or update, the url to the dataset, etc.
Alongside those required fields, users can also add some optional pieces of information to add more specifications to the dataset, such as an acronym, the license used, a temporal or spatial coverage, or the resources.</p>
<p>Each dataset has 2 identifiers:</p>
<ul>
<li><strong>id</strong>: The unique id of the dataset that is set at the creation of the dataset and never changes</li>
<li><strong>slug</strong>: The dataset permalink string (its title in lowercase separated by dashes)</li>
</ul>
<p>Both of those identifiers can be used in a link to access to a dataset.</p>
<p><strong>Resources</strong> are the containers used within datasets to describe each data collection.
A resource also has mandatory fields:</p>
<ul>
<li><strong>title</strong>: A one sentence description of the data resource</li>
<li><strong>type</strong>: The resource type (documentation, main file, API, …)</li>
<li><strong>url</strong>: URL to the data itself</li>
<li><strong>format</strong>: Format of the data</li>
</ul>
<p>As for datasets, some optional fields can also be defined for resources, such as the description of the resource, its release date, its size in bytes, its mime type, etc.</p>
<p>A resource is identified by a unique <strong>id</strong>, that is set at the creation of the resource and never changes.</p>
<p>A dataset can contain multiple resources, and a resource always belongs to a dataset. You can find more information about the format, and the different fields within the <a href="#references">References part</a></p>
<hr />
<h2 id="use-misp-to-create-modify-or-delete-data">Use MISP to create, modify or delete data</h2>
<p>MISP can be used to make any collection of data from the given instance available on an open data portal.<br />
To do so, the MISP Search API is used (documentation available within the <a href="#references">References part</a> as well).<br />
Users can then create, modify or delete any dataset or resource (as long as they have the right to do so) in the chosen portal.</p>
<h3 id="general-instructions">General instructions</h3>
<p>Regardless of which use case you want to try out, there are a few instructions that must be considered in order to make the interaction with the Open data portal work.</p>
<p>The enpoint to query on MISP’s side will always be <code class="highlighter-rouge">opendata.</code></p>
<p>The way in which the interaction with the portal is initiated withing MISP is by the use of the MISP API.<br />
Some API queries, essentially GET calls, are available for everyone and do not require an authentication.<br />
In our case, we always modify already existing content or create new content on the portal, which requires knowledge about who the to be modified or the newly created data belongs to.<br />
Thus, an API key will always be needed in order to authenticate with the Open data portal.<br />
This API key will be provided in your MISP Search queries via the <code class="highlighter-rouge">auth</code> field (See examples below)</p>
<p>The Open data feature on MISP only supports the Luxembourgish portal for now (notes on the future improvements available <a href="#future-improvement">here</a>), but as soon as more portals will be supported, the passing of the corresponding urls will also be required.</p>
<h3 id="publish-data-in-an-open-data-portal">Publish data in an Open data portal</h3>
<p>Publishing data in an Open data portal implies the creation of both a dataset along with its resource(s) containing the actual data or alternatively, a link pointing to it (details of the format available above within the <a href="#the-open-data-format">Open data format</a> part).<br />
But it is also possible to create the dataset and to add resources later.</p>
<p>The <em>Relative path to query</em> value is either <code class="highlighter-rouge">/attributes/restSearch</code> to make available data collections of MISP attributes, or <code class="highlighter-rouge">/events/restSearch</code> for complete MISP events.</p>
<p>Here is an example of query that can be used to create a dataset with a resource:</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>{
"returnFormat": "opendata",
"type": "x509-fingerprint-md5",
"tags": "tlp:white",
"auth": "_YOUR_OPENDATA_PORTAL_API_KEY_",
"setup": {
"dataset": {
"description": "Dataset test from MISP containing data shared via a MISP platform.",
"title": "x509 certificates shared in MISP"
},
"resources": {
"title": "All x509 certificates shared with MISP",
"type": "api",
"format": "json"
}
},
"misp-url": "https://mispriv.circl.lu",
"portal-url": "data.public.lu"
}
</code></pre></div></div>
<p>In this example, we can see the minimum requirement of information needed to interact with the Open data portal:</p>
<ul>
<li><code class="highlighter-rouge">returnFormat</code> defines the MISP endpoint to query.<br />
<em>Required to be set to <code class="highlighter-rouge">opendata</code></em></li>
<li><code class="highlighter-rouge">type</code> and <code class="highlighter-rouge">tags</code> are examples of MISP Search specific fields used to filter the data that is going to be share in the Open data portal.<br />
<em>Optional non exhaustive list of filters (Look at the <a href="https://github.com/MISP/misp-book/tree/master/automation#search">MISP Search API Documentation</a> for more filter examples)</em></li>
<li><code class="highlighter-rouge">auth</code> contains the required Open data portal API key.<br />
<em>Required</em></li>
<li><code class="highlighter-rouge">setup</code> contains all the metadata information used to create the dataset and its resource.<br />
<em>Should contain at least the <a href="#the-open-data-format">required fields</a> for datasets (and potentially resources)</em></li>
<li><code class="highlighter-rouge">misp-url</code> is the address of the MISP server to use in the link pointing to the data.<br />
<em>If not set, the default external base url of the MISP server is used, if set, otherwise the default internal base url.</em></li>
<li><code class="highlighter-rouge">portal-url</code> is the address of the Open data portal to query.<br />
<em>If not set, the default one will be <code class="highlighter-rouge">data.public.lu</code>.</em></li>
</ul>
<p>Within the setup fields, <code class="highlighter-rouge">title</code> is the one that is used to identify the dataset and the resource.<br />
<strong>The Open data portal API deals with the datasets and resources <code class="highlighter-rouge">id</code> fields, but MISP handles this for us, so users only have to provide titles.</strong><br />
If a dataset with the same title already exists, it will either create a resource if none exist within the dataset with the same title, or modify the existing resource identified by this title.
In the end, the only difference between a creation and a modification of datasets or resources is defined by the existence (or lack thereof) of a dataset or resource with the same title.</p>
<p>MISP returns a confirmation message with the link of the newly created dataset or resource:</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>Your resource has been successfully created.
It is available under the following link: https://data.public.lu/en/datasets/5e8c91ddd2bfb230a62eb382/#resource-d15c86a9-c907-4977-8cc0-2312c915057e
You can also find the json format equivalent: https://data.public.lu/api/1/datasets/5e8c91ddd2bfb230a62eb382/resources/d15c86a9-c907-4977-8cc0-2312c915057e/
</code></pre></div></div>
<p>Both of the provided links are pointing to the metadata header of the dataset or resource (resource in the example used here).<br />
The link to the actual data is available then with the <code class="highlighter-rouge">url</code> field you can find in the metadata header.</p>
<p>If the dataset and/or resource already exists, the query will then post a modification to them, and the confirmation message will be mostly the same:</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>Your resource has been successfully updated.
It is available under the following link: https://data.public.lu/en/datasets/5e8c91ddd2bfb230a62eb382/#resource-d15c86a9-c907-4977-8cc0-2312c915057e
You can also find the json format equivalent: https://data.public.lu/api/1/datasets/5e8c91ddd2bfb230a62eb382/resources/d15c86a9-c907-4977-8cc0-2312c915057e/
</code></pre></div></div>
<p><strong>Important Note</strong>: Modifying a content (dataset or resource) requires the user to have the right to do so.</p>
<h3 id="delete-data-from-an-open-data-portal">Delete data from an Open data portal</h3>
<p>Deleting data from an Open data portal requires less information than what is needed to create or modify some content.<br />
The MISP server url does not matter anymore in the case of a deletion, but we can still specify which Open data portal to query.<br />
As we already explained that datasets and resources can be identified by their title, we only need then to identify which dataset or resource to delete and thus no longer need to add additional fields in the query.</p>
<p>Which gives us the following example:</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>{
"returnFormat": "opendata",
"auth": "_YOUR_OPENDATA_PORTAL_API_KEY_",
"setup": {
"dataset": "x509 certificates shared in MISP",
"resources": [
"x509 certificates (sha256) shared with MISP",
"x509 certificates (sha1) shared with MISP",
"x509 certificates (md5) shared with MISP"
],
},
"delete": 1,
"portal-url": "data.public.lu"
}
</code></pre></div></div>
<p>Only some required fields remain:</p>
<ul>
<li><code class="highlighter-rouge">returnFormat</code>, as always, to get to the correct MISP endpoint.<br />
<em>Required to be set to <code class="highlighter-rouge">opendata</code></em></li>
<li><code class="highlighter-rouge">auth</code>, as always.<br />
<em>Required</em></li>
<li><code class="highlighter-rouge">setup</code> which now only contains the dataset, and (and optionally resource(s)) title(s).<br />
<em>Should contain a valid dataset title (and valid resource titles if necessary)</em><br />
<em>Put resources titles into brackets for more than 1 resource, without brackets otherwise.</em></li>
<li><code class="highlighter-rouge">delete</code> in order to tell MISP that we want to execute a delete query.<br />
<em>Required to be set to 1</em></li>
<li><code class="highlighter-rouge">portal-url</code> to select the Open data portal to query.<br />
<em>If not set, <code class="highlighter-rouge">data.public.lu</code> is the default value</em></li>
</ul>
<p>Note that if only a dataset title is provided, the portal will be queried for a full dataset delete, which includes all of its resources.<br />
Alternatively, if at least 1 resource title is provided, it will only delete the referenced resources, and the dataset will still exist, with its potential resources that have not been deleted.</p>
<p>Again a small confirmation message shows the result of the delete query:</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>The resource x509 certificates (sha256) shared with MISP has been deleted from the open data portal.
The resource x509 certificates (sha1) shared with MISP has been deleted from the open data portal.
The resource x509 certificates (md5) shared with MISP has been deleted from the open data portal.
</code></pre></div></div>
<h3 id="search-data-stored-in-an-open-data-portal">Search data stored in an Open data portal</h3>
<p>Before updating or deleting some data from the Open data portal, you may want to check first the content of a dataset and/or resource.<br />
To do so, there is a search feature that can show the full content of a dataset and its resources, in json format, as it is stored and available on the portal.</p>
<p>This feature does not push any modification to the dataset or the resources on the platform and only sends a <code class="highlighter-rouge">GET</code> query to gather the content you want to show.<br />
Thus, it is the only case where the authentication is not needed.</p>
<p>This gives us the following example:</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>{
"returnFormat": "opendata",
"setup": {
"dataset": "x509 certificates shared in MISP",
"resources": "All x509 certificates shared with MISP"
}
"search": 1,
"portal-url": "data.public.lu"
}
</code></pre></div></div>
<p>Only a few fields are still required:</p>
<ul>
<li><code class="highlighter-rouge">returnFormat</code>, as always, to get to the correct MISP endpoint.<br />
<em>Required to be set to <code class="highlighter-rouge">opendata</code></em></li>
<li><code class="highlighter-rouge">setup</code> which now only contains the dataset (and optionally resource(s)) title(s).
<em>Should contain a valid dataset title (and valid resource titles if necessary)</em><br />
<em>Put resources titles into brackets for more than 1 resource, without brackets otherwise.</em></li>
<li><code class="highlighter-rouge">search</code> in order to tell MISP that we want to execute a search query.<br />
<em>Required to be set to 1</em></li>
<li><code class="highlighter-rouge">portal-url</code> to select the Open data portal to query.<br />
<em>If not set, <code class="highlighter-rouge">data.public.lu</code> is the default value</em></li>
</ul>
<p>In this case, the json format of the dataset and its resources is then displayed (with some warning when needed)</p>
<hr />
<h2 id="future-improvements">Future improvements</h2>
<p>List of non-exhaustive possible improvements for the implementation of the Open data feature:</p>
<ul>
<li>Make it available for more Open data portals. Status of the currently supported portals available <a href="https://github.com/MISP/misp-opendata/blob/main/portals_support.md">here</a>.</li>
<li>Allow users to upload data collections in the different supported data portals (and deal with the content size limit).</li>
<li>Enhancement of the parameters handling to support multiple datasets/resources creation in one MISP restSearch query.</li>
</ul>
<h2 id="example-of-dataset-created-with-misp">Example of dataset created with MISP</h2>
<p><img src="https://raw.githubusercontent.com/MISP/misp-opendata/main/luxembourgish_portal_example.png" alt="picture" /></p>
<h2 id="references">References</h2>
<ul>
<li><a href="https://data.public.lu/fr/apidoc/">data.public.lu API Documentation</a></li>
<li><a href="https://github.com/MISP/misp-book/tree/master/automation#search">MISP Search API Documentation</a></li>
<li><a href="https://github.com/MISP/misp-opendata">MISP opendata source code</a></li>
</ul>
<p><img src="https://raw.githubusercontent.com/MISP/misp-opendata/main/en_cef.png" alt="logo" /></p>2020-07-29T23:00:00+00:00https://www.misp-project.org/2020/07/28/MISP.2.4.129.releasedMISP - MISP 2.4.129 released (merge event improved, event block rule system, security fixes and many bugs fixed)2020-07-27T23:00:00+00:00<h1 id="misp-24129-released">MISP 2.4.129 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.129">2.4.129</a>) has been released with an improved merge functionality, a new event block rule system, many security fixes and bugs fixed.</p>
<h1 id="merge-functionality-improved">Merge functionality improved</h1>
<ul>
<li>handle objects, tags, etc via @chrisr3d’s module result parsing</li>
<li>handle sharing groups correctly</li>
<li>using standardised fetchers internally</li>
<li>API enabled (which will directly merge all contents of the source event into the target event)</li>
</ul>
<h1 id="event-block-rule-system-added">event block rule system added.</h1>
<ul>
<li>add simple tag filters to block events from being added.</li>
<li>it will not stop a manual creation of an event with subsequent adding of the tag in a later stage</li>
<li>it will however block synced events</li>
</ul>
<h1 id="many-bugs-fixed-and-small-improvements">Many bugs fixed and small improvements</h1>
<p>Many other improvements are documented in the <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a>.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2020-07-27T23:00:00+00:00https://blog.rootshell.be/?p=33840MISP - [SANS ISC] Simple Blacklisting with MISP & pfSense2020-07-23T11:02:26+00:00<p>I published the following diary on isc.sans.edu: “Simple Blacklisting with MISP & pfSense“: Here is an example of a simple but effective blacklist system that I’m using on my pfSense firewalls. pfSense is a very modular firewall that can be expanded with many packages. About blacklists, there is a well-known</p>
<p>The post <a rel="nofollow" href="https://blog.rootshell.be/2020/07/23/sans-isc-simple-blacklisting-with-misp-pfsense/">[SANS ISC] Simple Blacklisting with MISP & pfSense</a> appeared first on <a rel="nofollow" href="https://blog.rootshell.be">/dev/random</a>.</p>2020-07-23T11:02:26+00:00http://blog.thehive-project.org/?p=5429MISP - Cortex-Analyzers 2.8.0: to infinity and beyond!2020-06-30T21:20:07+00:00Thanks to the community and all the contributors, this release comes with 1 new Analyzer, 2 new Responders, lots of improvements and bug fixes. But there is more news from the front. Starting from this milestone, bugfixes and new Analyzers or Responders should be released in a smoother way as we are improving few processes. … <a href="https://blog.thehive-project.org/2020/06/30/cortex-analyzers-2-8-0-to-infinity-and-beyond/" class="more-link">Continue reading <span class="screen-reader-text">Cortex-Analyzers 2.8.0: to infinity and beyond!</span> <span class="meta-nav">→</span></a>2020-06-30T21:20:07+00:00https://www.misp-project.org/2020/06/24/MISP.2.4.128.releasedMISP - MISP 2.4.128 released (STIX import/export refactored release edition)2020-06-23T23:00:00+00:00<h1 id="misp-24128-released">MISP 2.4.128 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.128">2.4.128</a>) has been released with an improved version of attributes decaying, new set of widgets, many improvements and bugs fixed.</p>
<h1 id="improved-decaying-of-attributes-version-2">Improved decaying of attributes (version 2)</h1>
<p>In MISP 2.4.116, a decaying functionality was added to allow users and organisations to easily expire information depending on their personalised objectives and targets.</p>
<p>Based on the feedback of the organisations relying on the decaying feature, the following improvements were included:</p>
<ul>
<li>
<p>Added a new user setting, <code class="highlighter-rouge">default_restsearch_parameters</code>, allowing users to supply restSearch parameters that will be automatically passed to the export mechanism during API queries fetch. The main purpose of this new setting is to enable users to inject filters when integrating with third-party tools not offering the possibility to control the queries performed against MISP. This for example allow to set the default decaying parameters to all restSearch queries performed by the given user.</p>
</li>
<li>
<p>Added a new setting, <code class="highlighter-rouge">tag_numerical_value_override</code>, allowing users to override the <code class="highlighter-rouge">numerical_value</code> of tags. The main purpose of this new setting is to let users convey their own numerical values for tags. It does not constrain site-admins to the values provided by the official misp-taxonomy repositor, and instead allows them to define new values for entries not having a numerical value in the first place.</p>
</li>
</ul>
<h2 id="major-changes-in-decay-computation">Major changes in decay computation</h2>
<p>Attributes’ <code class="highlighter-rouge">last_seen</code> will now takes precedences over their <code class="highlighter-rouge">timestamp</code> if the former is set. In the decaying implementation prior to this version, if no sightings were recorded, the simulated last sighting was set on the <code class="highlighter-rouge">timestamp</code> value. However, in this new version, the <code class="highlighter-rouge">last_seen</code> value will be used instead. Users will be able to alter attributes (attach tags, modify <code class="highlighter-rouge">last_seen</code>, …) without refreshing the decaying score to its maximum value.</p>
<h1 id="new-widgets-added-to-misp">New widgets added to MISP</h1>
<p>Additional widgets (contributed by Koen Van Impe) were added in MISP with the following features:</p>
<ul>
<li>Widget to display system resources (df, cpu, mem)</li>
<li>Widget to display the latest sightings</li>
<li>Widget to display the false positive sightings above certain threshold</li>
</ul>
<p>Don’t hesitate to contribute your own widgets and take a look at the existing ones.</p>
<h1 id="various-improvements">Various improvements</h1>
<ul>
<li>[cli] Command for pulling from all remote servers.</li>
<li>[UI] Add event ID to page table.</li>
<li>[events:distributionGraph] Added close button in popover.</li>
<li>[correlations] Refactored correlation saving.
<ul>
<li>Always show other correlating value (useful for CIDR correlations)</li>
<li>Make correlation saving faster (move more work to database, do not fetch not necessary fields)</li>
<li>Fix some small bugs</li>
</ul>
</li>
</ul>
<p>Many other improvements are documented in the <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a>.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2020-06-23T23:00:00+00:00https://www.misp-project.org/2020/06/19/MISP.2.4.127.releasedMISP - MISP 2.4.127 released (decay updates release edition)2020-06-18T23:00:00+00:00<h1 id="misp-24127-released">MISP 2.4.127 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.127">2.4.127</a>) has been released with an improved version of attributes decaying, new set of widgets, many improvements and bugs fixed.</p>
<h1 id="improved-decaying-of-attributes-version-2">Improved decaying of attributes (version 2)</h1>
<p>In MISP 2.4.116, a decaying functionality was added to allow users and organisations to easily expire information depending on their personalised objectives and targets.</p>
<p>Based on the feedback of the organisations relying on the decaying feature, the following improvements were included:</p>
<ul>
<li>
<p>Added a new user setting, <code class="highlighter-rouge">default_restsearch_parameters</code>, allowing users to supply restSearch parameters that will be automatically passed to the export mechanism during API queries fetch. The main purpose of this new setting is to enable users to inject filters when integrating with third-party tools not offering the possibility to control the queries performed against MISP. This for example allow to set the default decaying parameters to all restSearch queries performed by the given user.</p>
</li>
<li>
<p>Added a new setting, <code class="highlighter-rouge">tag_numerical_value_override</code>, allowing users to override the <code class="highlighter-rouge">numerical_value</code> of tags. The main purpose of this new setting is to let users convey their own numerical values for tags. It does not constrain site-admins to the values provided by the official misp-taxonomy repositor, and instead allows them to define new values for entries not having a numerical value in the first place.</p>
</li>
</ul>
<h2 id="major-changes-in-decay-computation">Major changes in decay computation</h2>
<p>Attributes’ <code class="highlighter-rouge">last_seen</code> will now takes precedences over their <code class="highlighter-rouge">timestamp</code> if the former is set. In the decaying implementation prior to this version, if no sightings were recorded, the simulated last sighting was set on the <code class="highlighter-rouge">timestamp</code> value. However, in this new version, the <code class="highlighter-rouge">last_seen</code> value will be used instead. Users will be able to alter attributes (attach tags, modify <code class="highlighter-rouge">last_seen</code>, …) without refreshing the decaying score to its maximum value.</p>
<h1 id="new-widgets-added-to-misp">New widgets added to MISP</h1>
<p>Additional widgets (contributed by Koen Van Impe) were added in MISP with the following features:</p>
<ul>
<li>Widget to display system resources (df, cpu, mem)</li>
<li>Widget to display the latest sightings</li>
<li>Widget to display the false positive sightings above certain threshold</li>
</ul>
<p>Don’t hesitate to contribute your own widgets and take a look at the existing ones.</p>
<h1 id="various-improvements">Various improvements</h1>
<ul>
<li>[cli] Command for pulling from all remote servers.</li>
<li>[UI] Add event ID to page table.</li>
<li>[events:distributionGraph] Added close button in popover.</li>
<li>[correlations] Refactored correlation saving.
<ul>
<li>Always show other correlating value (useful for CIDR correlations)</li>
<li>Make correlation saving faster (move more work to database, do not fetch not necessary fields)</li>
<li>Fix some small bugs</li>
</ul>
</li>
</ul>
<p>Many other improvements are documented in the <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a>.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2020-06-18T23:00:00+00:00https://www.misp-project.org/2020/06/04/MISP.2.4.126.releasedMISP - MISP 2.4.126 released (Spring release edition)2020-06-03T23:00:00+00:00<h1 id="misp-24126-released">MISP 2.4.126 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.126">2.4.126</a>) has been released a while ago, though we have forgotten to publish a blog post about it - thanks to @coolacid for the reminder. This version includes a security fix and various quality of life improvements.</p>
<h1 id="security-fix---fixed-xss">Security fix - fixed XSS</h1>
<p><a href="https://cve.circl.lu/cve/CVE-2020-13153">Fixed a persistent XSS</a> (CVE-2020-13153) that could be triggered by correlating an attribute via the freetext import tool with an attribute that contains a javascript payload in the comment field. By hovering over the correlation, the analyst encoding the information would have the exploit triggered.</p>
<p>Thanks to @JakubOnderka for reporting it!</p>
<h1 id="tool-to-generate-the-communities-webpage">Tool to generate the communities webpage</h1>
<p>Being able to find the right communities is key when utilising MISP. Thanks to @cvandeplas for implementing this!</p>
<h1 id="experimental-cli-only-force-pull-method-added">experimental CLI only force pull method added</h1>
<p>It allows an administrator to issue a special kind of pull via the API that overwrites the local data with that on the remote, no matter which one is newer. No additional data gets deleted, but modifications will get reverted to the remote’s state. This tool is meant as a last resort if things have gone awry with unwanted local modifications.</p>
<h1 id="a-host-of-quality-of-life-fixes">A host of quality of life fixes</h1>
<p>A long list of improvements, fixes and new functionalities have been added, make sure to check out the changelog for an exhaustive list!</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2020-06-03T23:00:00+00:00http://blog.thehive-project.org/?p=5220MISP - Cortex-Analyzers 2.7.0: 5 Analyzers, 1 Responder2020-05-15T09:20:00+00:00Good morning (or evening if you are on that side of the planet) folks! We had a very busy week, packed with announcements. First, we released TheHive 4.0-RC2 which you’ve certainly taken to test, then we announced two patch releases for TheHive 3.4. And guess what? Here are some additional Cortex analyzers, a responder and … <a href="https://blog.thehive-project.org/2020/05/15/cortex-analyzers-2-7-0-5-analyzers-1-responder/" class="more-link">Continue reading <span class="screen-reader-text">Cortex-Analyzers 2.7.0: 5 Analyzers, 1 Responder</span> <span class="meta-nav">→</span></a>2020-05-15T09:20:00+00:00http://blog.thehive-project.org/?p=5292MISP - New TheHive 3.4 Patch Releases2020-05-12T16:55:36+00:00Last month (that should be… April… we are kinda losing track of time during the confinement), we made silently 2 patch releases for TheHive 3.4, our current stable version even if we have our hands full of soap and bleach as we are working on the eagerly awaited TheHive 4.0.0 final release: 3.4.1, shortly followed … <a href="https://blog.thehive-project.org/2020/05/12/new-thehive-3-4-patch-releases/" class="more-link">Continue reading <span class="screen-reader-text">New TheHive 3.4 Patch Releases</span> <span class="meta-nav">→</span></a>2020-05-12T16:55:36+00:00https://www.misp-project.org/2020/05/06/MISP.2.4.125.releasedMISP - MISP 2.4.125 released (aka self-registration feature and feed improvements release)2020-05-05T23:00:00+00:00<h1 id="misp-24125-released">MISP 2.4.125 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.125">2.4.125</a>) has been released. This version includes various improvements including a major refactoring of the feed system, the addition of OTP, a new inbox system to allow for self-registration, sightings in the timeline visualisation and many more improvements.</p>
<h1 id="new-inbox-system-and-self-registration-feature">new inbox system and self-registration feature</h1>
<p>If you operate a large community such as an ISAC, the creation of new users can be a tedious task. The new self-registration feature allows organisations to receive and review registration before creating the real user in MISP.</p>
<ul>
<li>if the feature is enabled, users can unauthenticated send a registration request to MISP
<ul>
<li>request includes information on desired org and some privileges (sync / org admin / publisher)</li>
</ul>
</li>
<li>requests land in the inbox, admins can inspect the registration requests
<ul>
<li>they can accept/discard them individually or en masse</li>
<li>users will be notified of their credentials automatically</li>
<li>quick user creation if the user asks for an org that doesn’t exist yet</li>
</ul>
</li>
</ul>
<h1 id="e-mail-based-otp">E-mail based OTP</h1>
<p>To add a second layer of security, OTP has been made available thanks to the contribution of @Golbark. If you would like to use this feature, please enable it via your security settings. Users will receive tokens via e-mail that they need to provide each time they authenticate and start a new session with MISP.</p>
<h1 id="feeds-index-refactoring-and-new-features">Feeds index refactoring and new features</h1>
<ul>
<li>added the ability to select an orgc ID for CSV/freetext feeds
<ul>
<li>all events created from this feed will carry the selected orgc_id</li>
</ul>
</li>
<li>Refactored the index fully
<ul>
<li>using the factories</li>
<li>better warnings against the dangerous new feed each pull setting</li>
<li>event index search added</li>
<li>several settings cleaned up / made more clear</li>
</ul>
</li>
<li>auto reload of default feed configuration disabled, fixes #2542, fixes #5789
<ul>
<li>added a button / endpoint to handle that instead to allow for the deleted default feeds to stay delete</li>
</ul>
</li>
</ul>
<h1 id="debugging-improvement">Debugging improvement</h1>
<ul>
<li>[database] New MySQL data source added for debugging.
<ul>
<li>MySQLObserver datasource added - prepends all queries with the requested controller/action and user ID for better debugging</li>
</ul>
</li>
</ul>
<p>May improvements were done in this MISP release, for a complete overview, you can have a look at the <a href="https://www.misp-project.org/Changelog.txt">complete changelog</a>.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2020-05-05T23:00:00+00:00http://blog.thehive-project.org/?p=5003MISP - Under the Mighty Hood of TheHive 42020-02-05T09:48:13+00:00We have been speaking about it for almost two years. We have been making it for more than twelve months. And the day (or rather the month in this case) has almost come for TheHive 4, our latest and greatest version, to be unleashed. While the first release candidate should be published by the end of … <a href="https://blog.thehive-project.org/2020/02/05/under-the-mighty-hood-of-thehive-4/" class="more-link">Continue reading <span class="screen-reader-text">Under the Mighty Hood of TheHive 4</span> <span class="meta-nav">→</span></a>2020-02-05T09:48:13+00:00http://blog.thehive-project.org/?p=4962MISP - Cortex-Analyzers 2.4.0: 138 Ways to Analyze, 10 Methods to Respond2020-02-10T08:45:00+00:00Guess what? TheHive Project is still alive and well, as Saâd already mentioned in a previous blog post. We’ve been certainly very busy lately, preparing the upcoming release of TheHive 4 and doing many other things beside working on our FOSS project. As a result, it took us a rather long time to merge several community … <a href="https://blog.thehive-project.org/2020/02/10/cortex-analyzers-2-4-0-138-ways-to-analyze-10-methods-to-respond/" class="more-link">Continue reading <span class="screen-reader-text">Cortex-Analyzers 2.4.0: 138 Ways to Analyze, 10 Methods to Respond</span> <span class="meta-nav">→</span></a>2020-02-10T08:45:00+00:00http://blog.thehive-project.org/?p=5145MISP - Cortex-Analyzers 2.6.0: 146 Analyzers, 18 Responders2020-03-25T17:54:07+00:00Amidst the ongoing COVID-19 crisis, we managed to release Cortex-Analyzers 2.6.0, which includes 4 new Analyzers, 2 new Responders, and a large number of bug fixes and improvements. We’d like to thank all the contributors for their awesome work! We truly appreciate the time they generously give away for helping our fellow cyberdefenders out there … <a href="https://blog.thehive-project.org/2020/03/25/cortex-analyzers-2-6-0-146-analyzers-18-responders/" class="more-link">Continue reading <span class="screen-reader-text">Cortex-Analyzers 2.6.0: 146 Analyzers, 18 Responders</span> <span class="meta-nav">→</span></a>2020-03-25T17:54:07+00:00https://www.misp-project.org/2020/02/12/MISP.2.4.121.releasedMISP - MISP 2.4.121 released (aka the security release)2020-02-11T23:00:00+00:00<h1 id="misp-24121-released">MISP 2.4.121 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.121">2.4.121</a>) has been released. This version is a security/bug fix release and users are highly encouraged to update as soon as possible. Besides that several issues were resolved and some new functionalities were added.</p>
<h1 id="security-issues">Security issues</h1>
<p>The new version includes fixes to a set of vulnerabilities, kindly reported by Dawid Czarnecki. For details, see the attached CVE information.</p>
<ul>
<li>A reflected XSS in the galaxy view <a href="https://cve.circl.lu/cve/CVE-2020-8893">CVE-2020-8893</a></li>
<li>ACL wasn’t always correctly adhered to for the discussion threads <a href="https://cve.circl.lu/cve/CVE-2020-8894">CVE-2020-8894</a></li>
<li>Potential time skew between web server and database would cause the brute force protection not to fire.<a href="https://cve.circl.lu/cve/CVE-2020-8890">CVE-2020-8890</a></li>
</ul>
<p>Whilst investigating the above, we have identified and resolved other issues with the brute force protection:</p>
<ul>
<li>Missing canonicalisation of the usernames before issuing the bruteforce entry.<a href="https://cve.circl.lu/cve/CVE-2020-8891">CVE-2020-8891</a></li>
<li>PUT requests for the login were skipping the protection. <a href="https://cve.circl.lu/cve/CVE-2020-8892">CVE-2020-8892</a></li>
</ul>
<p>Whilst the issues identified are not deemed critical, it is highly suggested to update and inform your peers to follow suit.</p>
<h1 id="additional-sync-pull-filters">Additional sync pull filters</h1>
<p>One of the most annoying side-effects of the synchronisation mechanism was the potential unfiltered flow of massive amounts of aged-out data when first pulling from a newly connected community. We have added a simple filter option when configuring sync connections to pass event index filters along with the sync requests. An example would be to limit the publish age of pulled data to the desired time frame (for example: Only fetch data that is at maximum 2 months old).</p>
<h1 id="new-background-worker-configuration-loading">New background worker configuration loading</h1>
<p>Background workers were loading the server wide configurations on startup, meaning that changes to server settings would not be reflected by any background processed job unless the workers were restarted. A new helper resolves this and loads the configuration on each job execution (Thanks to @RichieB2B for reporting the issue).</p>
<h1 id="memory-envelope-improvements">Memory envelope improvements</h1>
<p>When fetching data from MISP, it tries to cluster the data into smaller chunks and fetch it piece by piece to avoid memory exhaustion and to be able to serve the data anyway. The new release improves on the estimation, avoiding potential memory exhaustions with larger data-sets. Potential issues are also logged from here on.</p>
<h1 id="sql-schema-check-improvements">SQL schema check improvements</h1>
<p>Various improvements to both better inform administrators about potential issues along with remediation scripts</p>
<h1 id="a-host-of-other-improvements">A host of other improvements</h1>
<p>A massive list of improvements to the usability of MISP, with a special thank you to Jakub Onderka again for his endless stream of improvements.</p>
<h1 id="misp-objects-templates">MISP Objects templates</h1>
<p>We received a significant number of <a href="https://www.misp-project.org/objects.html">new object templates</a> to describe specific additional use cases including disinformation, media and also improved HTTP representation.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2020-02-11T23:00:00+00:00https://www.misp-project.org/2020/02/18/MISP.2.4.122.releasedMISP - MISP 2.4.122 released (aka the bug fix release)2020-02-17T23:00:00+00:00<h1 id="misp-24122-released">MISP 2.4.122 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.122">2.4.122</a>) has been released. This version includes various fixes, minor new features and improvements.</p>
<h1 id="log-user-ip-addresses-on-login">Log user IP addresses on login</h1>
<p>A new logging optional feature has been added to log user IPs on login.</p>
<p>The feature logs on successful login logs the associated user ID for a given IP (with a 30 day retention). It also logs the IP for the associated user ID (indefinite retention).</p>
<p>Two new command lines were added:</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>- Get IPs For User ID: `MISP/app/Console/cake Admin UserIP [user_id]`
- Get User ID For User IP: `MISP/app/Console/cake Admin IPUser [ip]`
</code></pre></div></div>
<h1 id="new-danish-community-added">New Danish community added</h1>
<p>We have a flexible system to announce information sharing communities directly in MISP - in 2.4.122, we have added a Danish MISP user-group community. If you would like to have your community added and announced to all MISP users, don’t hesitate to edit the <a href="https://github.com/MISP/MISP/blob/2.4/app/files/community-metadata/defaults.json">community JSON file</a> and perform a pull-request.</p>
<h1 id="correlation-bug-fixed">Correlation bug fixed</h1>
<p>A bug fix solves an issue where attribute edits could purge correlations. The bug was introduced by a merge gone wrong. The attribute edits that modify fields that do not affect the correlations (such as to_ids, comment, etc) would cause correlations to be purged</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2020-02-17T23:00:00+00:00https://www.misp-project.org/2020/03/10/MISP.2.4.123.releasedMISP - MISP 2.4.123 released (aka the dashboard and security fix release)2020-03-09T23:00:00+00:00<h1 id="misp-24123-released">MISP 2.4.123 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.123">2.4.123</a>) has been released. This version includes various security related fixed, and a new Dashboard system.</p>
<h1 id="security-fixes">Security fixes</h1>
<p>Thanks to a pentest conducted on behalf of the Centre for Cyber Security Belgium (CCB), we have received a list of ideas to improve our security posture along with 2 vulnerabilities:</p>
<ul>
<li>2 XSS vulnerabilities (reported and fixed, more info via <a href="/security">CVE-2020-10246</a> and <a href="/security">CVE-2020-10247</a>)</li>
<li>various improvements for our password policy</li>
<li>Improvements by adding preventative headers</li>
<li>Providing the more information to the users by revealing potential foul play</li>
</ul>
<p>We would hereby like to thank both the contracted part as well as CCB for sharing the results with us. We are always glad to receive pentest results, it’s a great way for organisations to improve the security of MISP and we highly encourage everyone to MISP for potential issues and to <a href="/security">let us know</a> - we will do our best to fix any identified issues as soon as possible.</p>
<h1 id="dashboard-system">Dashboard system</h1>
<p>As an outcome of the spread of COVID-19, we ourselves at the MISP-project team have spent a considerable amount of our free time over the past few weeks tracking the spread of and informing ourselves in regards to the outbreak.</p>
<p>As an outcome of quickly setting up a Coronavirus-sharing community via MISP for ourselves, in order to share and track information emerging about COVID-19, we have implemented a whole new Dashboarding functionality for MISP.</p>
<p>The new Dashboard is accessible directly in MISP and fully customisable by users.</p>
<ul>
<li>The system relies on bundled and custom widgets</li>
<li>widgets work similarly to other modular parts of MISP, design your own, drop it in the MISP directory to get started</li>
<li>For instructions on how to develop a basic widget visit <a href="https://www.misp-project.org/misp-training/a.a-widget-dev.pdf">The training slide repository</a></li>
<li>Under the hood it uses the user settings system, allowing for custom configurations per user</li>
<li>Dashboard templates can be saved and shared, both via MISP and via JSON configuration files</li>
<li>Widgets come with a host of support functionalities (ACL, caching, auto-reloading, configuration systems)</li>
</ul>
<p>We welcome contributions to our ever growing widget collection from our community, let us know if you want to get involved in the effort!</p>
<p>If you are interested in the covid-19 specific widgets, they are not included in the code-base directly, but are rather available via the new <a href="https://github.com/MISP/widget-collection">widget-collection</a> library.</p>
<h1 id="selecting-your-home-page-within-misp">Selecting your home page within MISP</h1>
<p>Users an now replace their landing page from it redirecting to the event index to any other page in MISP. We recommend the consideration of switching to the dashboard as the first point of entry. Simply navigate to the page you wish to bookmark and click on the little star icon in the header bar.</p>
<h1 id="a-bug-affecting-correlations-and-an-interesting-bug-hunt">A bug affecting correlations and an interesting bug hunt</h1>
<p>Due to a recently introduced bug, we had cases of correlations disappearing after an attribute edit under certain conditions (any edit not touching fields used to decide on whether to correlate an attribute). We have resolved the issue along with a full recorrelation being triggered on update, simply fetch the latest version of MISP and your instance should have the issue resolved once the job finishes.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2020-03-09T23:00:00+00:00https://www.misp-project.org/2020/03/26/cogsec-collab-misp-communityMISP - Cogsec Collab MISP Community - sharing group dedicated to misinformation and information campaigns2020-03-25T23:00:00+00:00<p>We’re proud to announce the CogSec Collab MISP Community - the first public MISP sharing group dedicated to misinformation and information campaigns.</p>
<h2 id="note-about-the-following-information">Note about the following information</h2>
<p>The below article has been kindly contributed by <a href="https://twitter.com/VV_X_7">VVX7</a> on behalf of the Cogsec Collab MISP Community. We at the MISP-Project team try out best to point those interested in topical information sharing in the right direction, with disinformation being one of the highly sought after topical communities. If you are coming from that particular field, get in touch with the folks at Cogsec Collab community. You can as of now also do that directly via your own MISP instance, simply navigate to the list of communities and send a request directly from there.</p>
<p>For more information about the Cogsec Collab MISP Community head over to <a href="https://www.cogsec-collab.org">the cogsec-collab.org</a>.</p>
<p><em>- the MISP-Project team</em></p>
<h1 id="a-community-dedicated-to-information-operations">A community dedicated to information operations</h1>
<p>We’re proud to announce the CogSec Collab MISP Community - the first public MISP sharing group dedicated to misinformation and information campaigns.</p>
<p>Our community seeks to connect misinformation researchers and responders by providing tools to streamline investigation and reporting on disinformation and information campaigns. By making our MISP instance available to the community we’re enabling researchers to generate and share information operations data in MISP JSON or STIX format at just a click of a drop-down menu.</p>
<p>We look forward to working with our partners to provide access to disinformation documentation and sharing standards, indicators, countermeasures and playbooks.</p>
<p>Send us an email to request access.</p>
<h2 id="misp">MISP</h2>
<p>The MISP Project started out as a way to share malware indicators. It’s grown to include much more - financial fraud, climate data and most recently COVID-19 cases.</p>
<p><a href="https://twitter.com/MISPProject/status/1239864641993551873">A dedicated MISP to share information about #COVID2019 https://covid-19.iglocska.eu - If you want access DM us on Twitter.</a></p>
<p>At its core MISP is an automated correlation engine. It assists analysts in finding interesting relationships between indicators and contextualising the data. For Cogsec Collab, it’s a means to provide structured threat intelligence to cross-sector partners with highly diverse requirements.</p>
<h2 id="amtt-misinformation-pattern-galaxy">AM!TT Misinformation Pattern Galaxy</h2>
<p><img src="/assets/images/cogsec/galaxy_list.png" alt="Descriptions of AMITT Techniques in the MISP Misinformation Pattern Galaxy." /></p>
<p>Our first achievement was the integration of the <a href="https://github.com/misinfosecproject/amitt_framework">AM!TT Framework</a> as a <a href="https://www.misp-project.org/galaxy.html#_misinformation_pattern">MISP Galaxy</a>. It contains the tags and definitions needed for describing the misinformation tactics and techniques present in a specific information operation.</p>
<h2 id="amtt-navigatord">AM!TT Navigatord</h2>
<p><img src="/assets/images/cogsec/amitt.png" alt="The MISP Project kindly developed this built-in technique navigator" /></p>
<p>Applying the AM!TT galaxy information to an event must be easy in order to encourage use by already overburdened information researchers. The MISP Project developers kindly created an inline AM!TT Navigator to respond to this need for conveniently tagging events with AM!TT techniques.</p>
<p>With this tool, analysts can simply click on the relevant techniques found in a report or sighting to include that information in the misinformation event data.</p>
<h2 id="dfrlab-dichotomies-of-disinformation">DFRLab Dichotomies of Disinformation</h2>
<p><img src="/assets/images/cogsec/dfrlab.png" alt="Atlantic Council's DFRLab Dichotomies of Disinformation" /></p>
<p>Also included in the CogSec Collab MISP is <a href="https://www.atlanticcouncil.org/programs/digital-forensic-research-lab/">Atlantic Council’s DFRLab</a> <a href="https://github.com/DFRLab/Dichotomies-of-Disinformation">Dichotomies of Disinformation</a> which is a new standard for describing information campaigns that can be used alone or in complement to the AM!TT framework.</p>
<p>The work of the DFRLab is included in MISP as a Taxonomy - a set of machine tags for describing indicators and events.</p>
<h2 id="future-work">Future Work</h2>
<p>From this point our next steps are to build elf communities and equip them with the tooling and training needed to be effective.</p>
<p>MISP will play an important role in distributing misinformation threat data but it’s just a tool; it’s the people who make the community of users that can make it great. If you work in the disinformation space, please reach out. Come talk to us.</p>
<p>As things develop we’ll have more to say about our disinformation sharing community. For now we’d like to thank the <a href="https://twitter.com/MISPProject">MISP Project</a> developers for their excellent work and commitment to FOSS threat intelligence tooling.</p>
<p>Thank you!</p>2020-03-25T23:00:00+00:00https://www.misp-project.org/2020/04/06/MISP.2.4.124.releasedMISP - MISP 2.4.124 released (aka the dashboard, auditing improvements)2020-04-05T23:00:00+00:00<h1 id="misp-24124-released">MISP 2.4.124 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.123">2.4.124</a>) has been released. This version includes various improvements including a new multiline widgets in the dashboard, auditing improvements and many bugs fixed.</p>
<h1 id="dashboard-and-widget-improved">Dashboard and widget improved</h1>
<p>The dashboard has been improved along with a host of bugs fixed. A UI for the multiline widget has been introduced.
<img src="/assets/images/misp/blog/2.4.124/multiline-demo.gif" alt="Multiline Demo" width="700" />
The new interface provides users a simple way to manipulate basic graph components. It includes legends, tooltips, auto-resize, clickable labels and a full support of the 2 most common x-axis: linear and time-based.</p>
<p>You can query the chart to see the delta between two datapoints by selecting the first then the last points. A summary will then be presented.
<img src="/assets/images/misp/blog/2.4.124/multiline-brush-delta.png" alt="Multiline delta between points" width="700" /></p>
<p>Finally, the widget styling is largely configurable. In addition to the <code class="highlighter-rouge">time_format</code> and the abscissa type, you can define other parameter influencing how the graph should be presented to the users
<img src="/assets/images/misp/blog/2.4.124/multiline-config.png" alt="Multiline Configuration sample" width="700" /></p>
<h1 id="auditing-individual-user-monitoring">(auditing) Individual user monitoring</h1>
<ul>
<li>Site admins can set the monitoring flag on a user if the feature is enabled on the instance</li>
<li>Monitored users will have all requests logged along with POST bodies</li>
<li>Keep in mind this functionality is quite heavy and intrusive - so use it with care. The idea is that this allows us to track potentially malicious users during an investigation</li>
</ul>
<h1 id="new-community-cogsec-collab-disinformation">New community CogSec Collab disinformation</h1>
<p>MISP includes the possibility to advertise your MISP information sharing community, don’t hesitate to propose your community to gain some visibility. We added “<a href="https://www.misp-project.org/2020/03/26/cogsec-collab-misp-community.html">The Cognitive Security Collaborative operates as a sharing community dedicated to information operations</a>”.</p>
<h1 id="covid-19-misp">COVID-19 MISP</h1>
<p>COVID-19 MISP is a MISP instance retrofitted for a COVID-19 information sharing community, focusing on two areas of sharing:</p>
<ul>
<li>Medical information</li>
<li>Cyber threats related to / abusing COVID-19</li>
</ul>
<p>The information sharing community has a low barrier of entry, everyone can contribute and use the data. By default, the information is classified as TLP:WHITE for broader distribution and usefulness. <a href="https://www.misp-project.org/covid-19-misp/">For more information and joining the COVID-19 MISP community</a></p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. This release includes multiple updates in <a href="https://www.misp-project.org/objects.html">misp-objects</a>, <a href="https://www.misp-project.org/taxonomies.html">misp-taxonomies</a> and <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a>.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2020-04-05T23:00:00+00:00https://www.misp-project.org/2020/01/21/MISP.2.4.120.releasedMISP - MISP 2.4.120 released (aka the timeline release)2020-01-20T23:00:00+00:00<h1 id="misp-24120-released">MISP 2.4.120 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.120">2.4.120</a>) has been released, including an extension to the data-model adding the first_seen and last_seen values at the attribute and object levels. The user-interface has been extended with a timeline view/editor per event, allowing users to see all occurrences of attributes and objects based on time. A new quick object edit tool has been added, enabling users to easily add new attributes to already existing objects. A long list of bugs were fixed and various improvements were made in the existing features.</p>
<h1 id="update-notes">Update notes</h1>
<p>Don’t forget to have background workers running before updating, there are some updates to the database which can take time depending on the size of your MISP instance. The
progress of the update can be verified via the interface of your MISP instance using the following endpoint: /servers/updateProgress .</p>
<h1 id="timeline-feature-and-improved-data-model">Timeline feature and improved data-model</h1>
<video src="/assets/images/misp/blog/timeline-video.mp4" title="Overview of the MISP timeline feature" width="800" height="450" controls="" autoplay="" loop="">Video tag is not supported by your browser</video>
<p><a href="https://www.misp-standard.org/">MISP standard format</a> has been extended to support first_seen and last_seen on any attribute or object in a MISP instance. This functionality is fully accessible via the restSearch API and via the user-interface of MISP. first_seen and last_seen can be set at the attribute and/or the object levels. A complete timeline viewer and editor has been added to allow users to:</p>
<ul>
<li>Quickly see the overall timeline of attributes and objects;</li>
<li>Zoom in and out in the timeline (alt + mouse wheel);</li>
<li>Edit and change the first_seen and last_seen by moving the attributes/objects directly on the timeline.</li>
</ul>
<p><img src="/assets/images/misp/blog/t-misp-overview.png" alt="The representation of spear phishing using the timeline function in MISP" /></p>
<p>As an example above, a spear phishing attack and their respective occurrences are displayed on the timeline. This new feature allows users to describe complex time-based information whilst using existing features such as object relationships.</p>
<h1 id="new-attribute-types">New attribute types</h1>
<ul>
<li>kusto-query attribute type added - Kusto query is the query language for the Kusto services in Microsoft Azure used to search large dataset. It’s used in Windows Defender ATP Hunting-Queries as well as Azure Sentinel (Cloud-native SIEM)</li>
<li>chrome-extension-id attribute type added - This attribute is used by Chrome to uniquely identify extensions. This helps the sharing of information about malicious extensions within a MISP sharing community.</li>
</ul>
<h1 id="misp-modules-version-24120">misp-modules version 2.4.120</h1>
<p>MISP modules have been improved and many new modules were added in the following related scopes: <a href="http://misp.github.io/misp-modules/expansion/">expansion</a>, <a href="http://misp.github.io/misp-modules/export_mod/">export</a> and <a href="http://misp.github.io/misp-modules/import_mod/">import</a>. Don’t forget to update the modules to benefit from the improvements and new features.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="https://www.misp-project.org/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2020-01-20T23:00:00+00:00https://www.misp-project.org/2019/12/04/MISP.2.4.119MISP - MISP 2.4.119 released (aka the quality of life release)2019-12-03T23:00:00+00:00# MISP 2.4.119 released
A new version of MISP ([2.4.119](https://github.com/MISP/MISP/tree/v2.4.119)) has been released, including several functionalities that should make the operation of a MISP instance more convenient.
# Vulnerability CVE-2019-19379 has been fixed
In app/Controller/TagsController.php in MISP 2.4.118, users can bypass intended restrictions on tagging data. The vulnerability has been fixed in 2.4.119 and assigned the following [CVE-2019-19379](https://cve.circl.lu/cve/CVE-2019-19379). We strongly recommend to update to this version. Thanks to Christophe Vandeplas for the reporting.
# Database diagnostics
There is a new sub-system in the diagnostics tool that will compare the current state of your MISP database to the reference db schema, highlighting potential issues / divergences. Keep in mind, not all issues are necessarily cause for concern, but generally it is recommended to fix the issues that are deemed critical. If you have doubts about why your DB looks different from what is expected, feel free to open up a github issue and we'll try to point you in the right direction.
On top of flagging diverging traits of your DB compared to the reference, the system also allows users to generate SQL queries that would rectify the potential issues. Please make sure that you back your database up before running the suggested queries and keep in mind that altering existing tables with high volumes of data can temporarily double the disk space requirements of the given table along with taking a long amount of time (especially true for large log, correlation and sighting tables).
# Improved timestamp filtering in MISP
attribute_timestamp flag added to attributes/restSearch. Now 4 different timestamp filters exist in MISP and can be used. An explanation of the 4 timestamp filters:
- timestamp: Filters on attribute AND event timestamp
- event_timestamp: Filters on event timestamp
- attribute_timestamp: Filters on attribute timestamp
- publish_timestamp: Filters on event.publish_timestamp
# API deprecation
The preparations for MISPs large refactor are well underway, this time we've added a new system that will start tracking deprecated endpoints in MISP and warning users of their state. The new system has the following functionalities:
- an internal list of deprecated endpoints is maintained
- any query against these endpoints increments a counter in redis
- if the deprecation is a confirmed hard deprecation, the user is warned via response headers (API) or flash messages (UI)
- for soft deprecations, we are collecting the information (locally on the instance only, it is up to the administrators to share the outcome with us on demand, outside of MISP, nothing is sent back automatically) on certain endpoints that we might consider deprecating based on usage. We are monitoring our instances to see if there's an interest to keep these features around - if you would like to submit your community's usage of these endpoints, reach out to us!
To view the results of the collection, just navigate to the diagnostics page.
# Export API refactor
All of the deprecated export APIs (such as /events/hids export, /events/stix or /events/xml) have been refactored and are using restSearch under the hood now. Nothing should change from a user perspective except for a size-able gain in peformance thanks to all of the restSearch optimisations.
If you do notice some of your legacy scripts misbehaving, please open a github issue and describe what went wrong.
# Sighting synchronisation
Sightings are now synchronising much more reliably, with a new sighting push setting being added to the server connection and a new publish sighting button being available for users with sighting rights on the event view.
# misp-modules version 2.4.119
MISP modules have been improved and many new modules were added in [expansion](http://misp.github.io/misp-modules/expansion/), [export](http://misp.github.io/misp-modules/export_mod/) and [import](http://misp.github.io/misp-modules/import_mod/). Don't forget to update the modules to benefit from the improvements and new features.
# Acknowledgement
We would like to thank all the [contributors](https://www.misp-project.org/contributors), reporters and users who have helped us in the past months to improve MISP and information sharing at large.
As always, a detailed and [complete changelog is available](https://www.misp-project.org/Changelog.txt) with all the fixes, changes and improvements.2019-12-03T23:00:00+00:00https://www.misp-project.org/2019/11/10/MISP.2.4.118MISP - MISP 2.4.118 released (aka the exclusivity tag release and SightingDB support)2019-11-09T23:00:00+00:00# MISP 2.4.118 released
A new version of MISP ([2.4.118](https://github.com/MISP/MISP/tree/v2.4.118)) has been release including a functionality that allows for tag exclusivity within taxonomies, the support for external Sighting sources via SightingDB and many fixes.
# Exclusive taxonomies
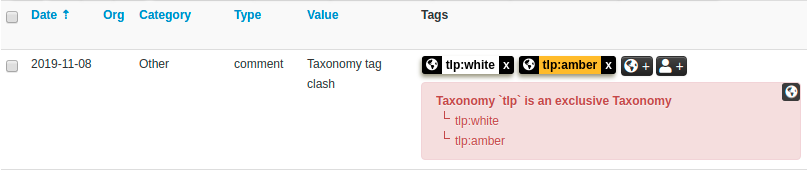
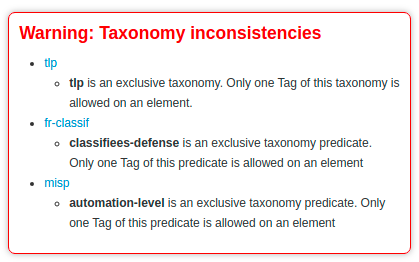
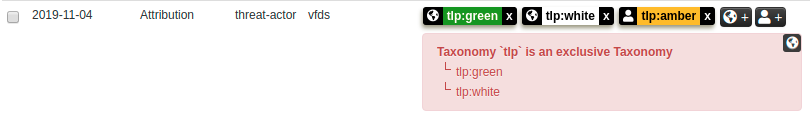
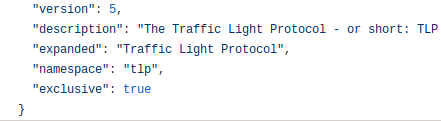
Some time ago, we've introduced the "exclusive" field in the MISP taxonomy format, in order to define rules of exclusivity within a given taxonomy predicate. As of this release, the MISP user-interface shows and enforces inconsistencies of exclusivity between tags assigned at the event and the attribute levels.
# SightingDB support
Over the course of the past years, the MISP Project has worked on improving the sighting capabilities of the platform in various ways when it comes to being able to provide contextualised sightings for information sharing. Most of the use-cases driving this type of sighting reporting were based on a need to encode intelligence gathered during incidents, as part of reporting or encoding the time-based aspects of intelligence. Being able to contextualise the sighting with information on the source, tie its release to the ACL rules governing the sighted data and describing the type of sighting were of a higher priority than performance.
After discussions with users looking for a completely diverging use-case, namely that of bulk, large-scale data/traffic analysis and correlation thereof with the threat information databases of their MISPs. Thanks to our friends at Devo, who have developed an open source system tackling these issues - the [SightingDB server](https://github.com/stricaud/sightingdb) - we had something to integrate into MISP as an alternate sightings system handling lookups against a large-scale sighting system.
Devo also decided for the standardisation of the SightingDB protocol format and we have decided to host it under the [misp-standard.org](https://www.misp-standard.org/) umbrella.
The SightingDB support includes the following:
- Added configuration tool
- Added lookups from the event view
- Added includeSightingdb flag for the restSearch searches
- Added SightingDB search tool
- Added SightingDB connection test tool
# Improved meta search in restSearch
The restSearch now supports the ability to search by creator organisation and also by the meta fields present in the galaxy clusters.
Such requests can now be done on any meta field within a galaxy:
~~~~
/attributes/restsearch/
{
"galaxy.cfr-suspected-victims": ["China", "Japan"],
"galaxy.cfr-target-category" : ["Government"]
}
~~~~
along with the various fields of the creator organisation object itself:
~~~~
/events/restsearch/
{
"galaxy.synonyms": "APT29",
"orgc.nationality": ["Hungary", "Belgium"]
}
~~~~
# Update module
The database schema model update has been improved in MISP and you can see the current inconsistencies of any past model change or the ongoing upgrade of the database model. This has been introduced because the next version of MISP will include a major improvement to the data model in order to add time references at several layers of the MISP data model. This update, coming in 2.4.119, includes an update of the attributes table which can take a significant amount of time depending of your MISP installation.
# MISP modules - many new modules with objects support
[Many new modules](http://misp.github.io/misp-modules/) were added such as the (event query language) EQL query module, Endgame EQL export module, OSINT.digitalside.it lookup module and many improvements to existing modules such as the CSV import module, IBM X-Force expansion module and more. Don't forget to update your modules to the latest version.
# Acknowledgement
We would like to thank all the [contributors](https://www.misp-project.org/contributors), reporters and users who have helped us in the past months to improve MISP and information sharing at large. Special thanks to Jakub Onderka for the continuous stream of excellent improvements, Sebastien Tricaud for the joint effort in the SightingDB support, [standard](https://raw.githubusercontent.com/MISP/misp-rfc/master/sightingdb-format/raw.md.txt) and [first implementation](https://github.com/stricaud/sightingdb).
As always, a detailed and [complete changelog is available](https://www.misp-project.org/Changelog.txt) with all the fixes, changes and improvements.2019-11-09T23:00:00+00:00https://www.misp-project.org/2019/10/27/visualising_common_patterns_attackMISP - Visualising common patterns using MISP and ATT&CK data2019-10-26T23:00:00+00:00<h1 id="visualising-common-patterns-using-misp-and-attck-data">Visualising common patterns using MISP and ATT&CK data</h1>
<p>Having access to a large amount of Threat information through MISP Threat Sharing communities gives you outstanding opportunities to aggregate this information and take the process of trying to understand how all this data fits together telling a broader story to the next level. We are transforming technical data or indicators of compromise (IOCs) into cyber threat intelligence. This is where the analytical challenge begins.</p>
<p>In his <a href="https://www.cia.gov/library/center-for-the-study-of-intelligence/csi-publications/books-and-monographs/psychology-of-intelligence-analysis/PsychofIntelNew.pdf">Psychology of Intelligence Analysis</a> book, Richards Heuer, a reference in intelligence analysis, describes some of the power and limitations our mental machinery has. While discussing the short term memory, long term memory and working memory he concludes the following:</p>
<blockquote>
<p>A well-known article written over 40 years ago, titled “The Magic Number Seven—Plus or Minus Two,” contends that <strong>seven—plus or minus two—is the number of things people can keep in their head all at once</strong>. That limitation on working memory is the source of many problems. People have difficulty grasping a problem in all its complexity. This is why we sometimes have trouble making up our minds. For example, we think first about the arguments in favor, and then about the arguments against, and we can’t keep all those pros and cons in our head at the same time to get an overview of how they balance off against each other.</p>
</blockquote>
<p>The recommended technique for coping with this limitation is to externalise the problem. We need to get it out of the human head into a form that simplifies the story, shows the main elements and how they relate to each other.
In this article we will be using visualisation techniques to help us better explore cyber threat information shared through <a href="https://github.com/MISP/MISP">MISP</a> and tagged with <a href="https://attack.mitre.org/">MITRE ATT&CK</a> techniques, all within a visualisation tool called <a href="https://www.paterva.com/buy/maltego-clients/maltego.php">Maltego</a>.</p>
<h2 id="getting-started">Getting started</h2>
<p>To get started you will need access to a MISP Threat Sharing community, or run your own instance. As a quickstart, you can use the <a href="https://www.misp-project.org/download/#virtual-images">MISP Training VM</a> and download data from the <a href="https://www.misp-project.org/feeds/#default-feeds-available-in-misp">CIRCL OSINT feed</a>.</p>
<p>You will want to download the <a href="https://www.paterva.com/buy/maltego-clients/maltego-ce.php">Maltego CE</a> (free, limited) or the <a href="https://www.paterva.com/buy/maltego-clients/maltego.php">classic</a> (paid) edition and install the open source <a href="https://github.com/MISP/MISP-maltego/blob/master/doc/README.md#installation">MISP-Maltego</a> transform.</p>
<h2 id="the-report">The report</h2>
<p>As an example, when looking at the report of attacks called “<a href="https://threatvector.cylance.com/en_us/home/pcshare-backdoor-attacks-targeting-windows-users-with-fakenarrator-malware.html">PcShare Backdoor Attacks Targeting Windows Users with FakeNarrator Malware</a>”, published by Cylance on the 25th of September 2019, and shared using MISP to ‘All Communities’ with the UUID <code class="highlighter-rouge">5d9b5ad3-6b64-4962-a63c-42ae73e10023</code>. They also attributed the attack to the <a href="https://attack.mitre.org/groups/G0081/">Tropic Trooper - G0081</a> actor.
<img src="/assets/images/misp/blog/visualisation_cylance_attack/tags.png" alt="associated ATT&CK techniques" /></p>
<h2 id="analysis-and-visualisation">Analysis and Visualisation</h2>
<p>In addition to the technical report of these attacks and the leveraged malware, the author documented 16 related ATT&CK techniques. Interestingly MITRE associated 18 ATT&CK techniques to this actor.
An avid reader will immediately notice the report has 2 techniques fewer than the actor described by MITRE.</p>
<p><strong>Is this correct or is the reality completely different?</strong></p>
<p>Keeping in mind the limitations of our working memory (7±2 items) we will need additional external support to compare the techniques. Whilst we could indeed take two papers and compare both lists for the duration of 5 minutes, let us do the exercise in a more visual and dynamic way.</p>
<p><strong>Open Maltego</strong> and create a <strong>MISPEvent entity</strong> with the MISP event number on your MISP server (for me this is <code class="highlighter-rouge">63423</code>). <strong>Right click</strong> on the event and choose <strong>“Event To Galaxies”</strong>.</p>
<p><img src="/assets/images/misp/blog/visualisation_cylance_attack/to_galaxies.png" alt="Event To Galaxies" /></p>
<p>We now have a first visual view of the tags that were attached to the report. Now, select the threat actor and choose <strong>Galaxy to Relations</strong> again, in order to expand this using MITRE ATT&CK relationships.
We now see a completely new graph which is much less readable. Make sure you configure Maltego to make collections of 4 or more similar entities. You can do this in the toolbar in the top: <img src="/assets/images/misp/blog/visualisation_cylance_attack/collections.png" alt="Collections" /></p>
<p><img src="/assets/images/misp/blog/visualisation_cylance_attack/actor_delta.png" alt="visual delta between the report and ATT&CK" /></p>
<p><strong>Suddenly our graph becomes much more readable and we see at a glance that our initial intuition of two missing techniques was actually completely wrong !</strong>
The Cylance report of these attacks does NOT have two (2) techniques fewer than expected. Actually, only five (5) are common with what MITRE documented! Thirteen (13) are only present in the MITRE documentation and eleven (11) are not associated with this actor by MITRE. Zooming in allows us to see the details:</p>
<p><img src="/assets/images/misp/blog/visualisation_cylance_attack/actor_delta_zoom.png" alt="visual delta between the report and ATT&CK" /></p>
<h2 id="what-does-this-mean">What does this mean?</h2>
<p>Does this mean Cylance or MITRE are wrong?
Not necessarily, many factors can explain this, for example:</p>
<ul>
<li>When creating and updating ATT&CK, MITRE only had incomplete knowledge of each actor. They only saw a piece of the puzzle.</li>
<li>Actors change their behaviour and their TTPs evolve over time.</li>
<li>We have also seen that tagging techniques can be a very subjective exercise. Additionally, the current techniques are sometimes very generic and their understanding is not universal. To address this challenge MITRE has been developing <a href="https://medium.com/mitre-attack/attack-sub-techniques-preview-b79ff0ba669a">sub-techniques</a>.</li>
<li>potentially others that are not covered in this article.</li>
</ul>
<h2 id="the-beginning-of-a-long-journey">The beginning of a long journey</h2>
<p>This example is only the beginning of a long journey of analysing and understanding the data which is available to us.</p>
<p>We always need to keep in mind that we only see a fragment of the entire story. Only by combining what you see in your network or constituency and what others see in theirs will we be able to better analyse and understand what is going on. This is yet another good reason to share cyber threat information with trusted communities.</p>
<p>We also know we have limited mental capabilities and can be assisted by technology to help ourselves with this challenge, for example with graphing and visualisation tools that are interconnecting with MISP!</p>2019-10-26T23:00:00+00:00https://blog.rootshell.be/?p=33475MISP - MISP Summit 0x05 Wrap-Up2019-10-21T17:42:21+00:00<p>I’m in Luxembourg for a full week of infosec events. It started today with the MISP summit. It was already the fifth edition and, based on the number of attendees, the tool is getting more and more popularity. The event started with a recap of what happened since the last</p>
<p><b>[The post <a rel="nofollow" href="https://blog.rootshell.be/2019/10/21/misp-summit-0x05-wrap-up/">MISP Summit 0x05 Wrap-Up</a> has been first published on <a rel="nofollow" href="https://blog.rootshell.be">/dev/random</a>]</b></p>2019-10-21T17:42:21+00:00https://www.misp-project.org/2019/10/11/MISP.2.4.117.releasedMISP - MISP 2.4.117 released (aka the the pre-conference season release)2019-10-10T23:00:00+00:00<h1 id="misp-24117-released">MISP 2.4.117 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.117">2.4.117</a>) has been release including major performance improvements in MISP and PyMISP, publish filter emails, throttling restSearch (very useful when you want to limit some users using the API of your MISP instance) and many more improvements.</p>
<h2 id="new-feature-publish-filters">New feature publish filters</h2>
<p>As port of the cyber-exchange programme, one of the participants - Armins Palms - gave us a great idea for an improvement that has been long overdue. Users now have the possibility to create filter rules for the publish alert e-mails. One of the biggest hurdles for efficiently using MISP’s alert system was that it could become quite verbose - if you are only interested in certain topics then receiving an alert about anything that gets published can easily cause alert-fatigue. Using the new system you can accurately configure MISP’s behaviour when it comes to alerting you based on your own preferences. The system allows to restrict alert messages by tags and publishing organisation using a nested boolean tree of settings, allowing for complex rule systems.</p>
<h2 id="new-feature-user-settings">New feature user settings</h2>
<p>One of the hurdles that has stopped us from implementing the above feature was the lack of a per user setting system. All configuration options in MISP have been based on system-wide, organisation-wide or role-based configurations. With the new user setting system, we have a simple but flexible tool to start adding more and more user level configurations.</p>
<h2 id="ipsum-feeds">IPSum feeds</h2>
<p>Another outcome of the cyber-exchange programme, thanks @stamparm we now have the different level IPsum feeds pre-configured in the default feed list.</p>
<h2 id="performance-improvements">Performance improvements</h2>
<p>We have identified and resolved several massive performance blockers in MISP. The issue reared its ugly head once larger, more object-heavy events started being shared, with some bringing even well provisioned servers to their knees. We have seen a rather drastic drop in CPU usage after applying the patch, resulting in our main sharing community’s server dropping to about 20% of its previous CPU usage. We highly advise everyone to upgrade their MISP instances ASAP.</p>
<h2 id="pymisp-performance-improvements">PyMISP performance improvements</h2>
<p>Similarly to the above fix, PyMISP was also suffering from performance issues in regards to massive events which have been addressed in the latest release, which includes a performance-oriented rework of the internals. Not only are we seeing a 50% cut in execution times when interacting with large events, but more importantly, the memory usage has been slashed to as little as ~5% of the usual numbers we’ve seen before the patch. It is therefore highly advised for anyone using PyMISP to upgrade to this release ASAP.</p>
<h2 id="throttling-restsearch">Throttling restSearch</h2>
<p>If you are running a larger community MISP instance, one of the biggest hurdles for coping with your community’s resource requirements is organisations using your heavily used MISP instance as the backend for their internal querying. Not only does this put a potentially unmaintainable level of stress on your instance when it comes to large and active communities, it also encourages bad practices in regards to information disclosures via the executed queries themselves (more information regarding this can be found in our previous blog entry regarding the <a href="https://misp-project.org/2019/09/25/hostev-vs-own-misp.html">benefits of running your own MISP instance</a>).</p>
<p>We have added a set of new options for administrators configuring user roles - it is now possible to enforce rate limits on API users. The setting controls how many heavy search-related queries users can execute within a 15 minute time-frame. The setting is completely optional per role and users are notified about their current quotas, reset times and remaining queries via headers in each request. The only endpoints affected currently are /events/restSearch and /attributes/restSearch, but we may extend this over time with other endpoints.</p>
<h2 id="using-custom-ca-bundles">Using custom CA bundles</h2>
<p>MISP comes with CakePHP’s default included CA bundle, which is based on the mozilla CA bundle. This can get rather stale, with the currently included bundle being several years old. Thanks to the contriution of @JakubOnderka, it is now possible to override the default bundle with a custom one.</p>
<h2 id="redis-diagnostics">Redis diagnostics</h2>
<p>The diagnostics page of MISP offers a wide range of tools to diagnose misconfigurations and issues that might arise with the instance, however, one aspect that was missing an easy way to diagnose was the redis configuration. Thanks to @JakubOnderka’s new tool this can now be diagnosed directly from the UI.</p>
<h2 id="various-other-improvements">Various other improvements</h2>
<p>Other improvements include a large list of general bug fixes, affecting UI and API users alike, an internal rework of the authentication workflow thanks to all the work of Andreas Rammhold in preparation for the merge of the LinOTP authentication module, various improvements to the STIX export, a new Netfilter export system and a host of other improvements.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large. Special thanks to Jakub Onderka for the continuous stream of excellent improvements, Andreas Rammhold for making the AppController much more sane, the participants of the cyber-exchange programme for helping us improve MISP in all sorts of different ways.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2019-10-10T23:00:00+00:00https://www.misp-project.org/2019/09/25/hostev-vs-own-mispMISP - Benefits of running your own MISP instance2019-09-24T23:00:00+00:00<h1 id="benefits-of-running-your-own-misp-instance">Benefits of running your own MISP instance</h1>
<p>One topic that regularly pops up during trainings and users that are just getting started with MISP in general is the question of running your own MISP versus using a hosted MISP instance. We have seen a lot of great efforts by ISACs, organisations with national or sectorial responsibilities leading the charge and acting as a central sharing hub for communities.</p>
<p>Whilst their efforts are absolutely pivotal fostering communities and in enabling information sharing, members of such communities should be aware of how to best utilise these resources. In any such community, members have the option to either use the “central sharing instance” as a hosted solution, or run their own MISP instances and interconnect with them to exchange data. In either case, they will have access to the same data and the same export functionalities, so avoiding the need to maintain another server may seem tempting, but do consider the following advantages of opting for your own server instead:</p>
<h2 id="ensure-that-private-data-remains-private">Ensure that private data remains private</h2>
<p>Distribution levels aside, if you create private data for yourself on a hosted instance, you are always have to rely on the hosting organisation to not accidentally view the data with their site admin accounts / directly via the database</p>
<h2 id="dont-let-other-snoop-on-your-searches">Don’t let other snoop on your searches</h2>
<p>Inspecting requests against a server you own is trivial, meaning that any search run against a posted MISP instance could be inspected by the system administrators of the hosted instance. What you search for is often more sensitive than the data that you store in your system, your analysts will often take to their knowledge-base such as MISP as a first step to verify whether datapoints are already known, often accidentally including for example victim information</p>
<h2 id="avoid-being-performance-limited-by-overburdened-systems">Avoid being performance limited by overburdened systems</h2>
<p>Consider the performance advantages when running heavy filtered lookups against MISP’s APIs, the load on sharing instances can be quite heavy depending on the number of organisations participating in the exchange, especially if they too use the hosted instance’s APIs for their internal use.</p>
<h2 id="take-advantage-of-advanced-features">Take advantage of advanced features</h2>
<p>MISP has a wide range of functionalities exclusively available to the host organisation. Be it ZMQ/Kafka/ES connections, local tags for routing 3rd party data, managing private enrichment modules, you’re missing out by not running your own system.</p>
<h2 id="be-the-king-of-your-own-castle">Be the king of your own castle</h2>
<p>MISP is a tool that aims to align itself to your workflows, from deciding on vocabularies to use, how to represent certain aspects of the information and setting requirements for how and when information can be shared, MISP site administrators have a host of tools at their disposal to drive how information is encoded and shared. By running your own MISP instance, you can decide for yourself instead of aligning yourself to the visions of your community hosts.</p>2019-09-24T23:00:00+00:00https://www.misp-project.org/2019/09/17/MISP.2.4.116.releasedMISP - MISP 2.4.116 released (aka the new decaying feature)2019-09-16T23:00:00+00:00<h1 id="misp-24116-released">MISP 2.4.116 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.116">2.4.116</a>) has been release, including a long awaited major new feature that deals with decaying indicators in addition to a new ATT&CK sightings export and a new sync priority capability.</p>
<h2 id="major-new-feature---decaying-indicators">Major new feature - decaying indicators</h2>
<p>After several years of gathering requirements, doing <a href="https://arxiv.org/abs/1803.11052">research</a> and various implementation attempts, MISP 2.4.116 finally includes <a href="https://www.misp-project.org/2019/09/12/Decaying-Of-Indicators.html">a new extensive feature for Decaying Indicators</a> using an advanced model to expire indicators based on custom and shareable models.</p>
<p>The feature allows MISP users to have a simple yet customisable system to automatically (or in some cases semi-manually) mark an Indicator Of Compromise (or more generally, an Attribute) as expired. The expiration system allows for the overlaying of computed scores on all attributes in real-time, based on the configured mappings via a decay model. The feature has been designed not to change the attributes per se, but rather to extend the meta information available about the attributes. As with everything in MISP, this new feature is accessible via both the user-interface and also via the API, in order to allow for the filtering of attributes based on a decay model.</p>
<p><img src="/assets/images/misp/blog/decaying/dm-event.png" alt="Decay Model index" width="700" /></p>
<p>The feature is exhaustive and we highly recommend to read the <a href="https://www.misp-project.org/2019/09/12/Decaying-Of-Indicators.html">blog post and watch the video showing all aspects of the new feature</a> or <a href="https://www.misp-project.org/misp-training/a.5-decaying-indicators.pdf">the slides from the MISP training</a>. As usual, MISP comes with a set of default decay models which can be extended locally or contributed back to the community at large.</p>
<h2 id="attck-sighting">ATT&CK sighting</h2>
<p>More and more users and communities are using the ATT&CK framework to contextualise information shared within MISP. The fine team of <a href="https://attack.mitre.org/resources/sightings/">ATT&CK recently created a format to share the sightings</a> associated with the techniques. MISP 2.4.116 now has a new output format available which allows users to export the sightings in the Mitre ATT&CK sightings format and share it back to the community or with MITRE directly. This allows the sharing of insights about the various techniques and their frequency of usage.</p>
<h2 id="new-sync-priority">New sync priority</h2>
<p>When having a lot of MISP server to sync with, you might want to prioritise the sync for specific communities or MISP instance. In 2.4.116, we introduced the ability to order the priority of the sync between MISP instances.</p>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to thank all the <a href="/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2019-09-16T23:00:00+00:00https://www.misp-project.org/2019/09/10/MISP.2.4.115.releasedMISP - MISP 2.4.115 released (aka CVE-2019-16202 and sync speed improvement)2019-09-09T23:00:00+00:00<h1 id="misp-24115-released">MISP 2.4.115 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.115">2.4.115</a>) with a major security fix (CVE-2019-16202) and various small improvements has been released. We strongly recommend all MISP users update to this version.</p>
<h2 id="fixed-major-performance-blocker-in-sync">Fixed major performance blocker in sync</h2>
<ul>
<li>fix based on the insights of @RichieB2B, the hero we need, not the one we deserve</li>
<li>added orgc_uuid to the minimal event index</li>
<li>added handlers for it on the pull side</li>
<li>when pulling from old instances the new functionality is skipped, resulting in the behaviour we had pre-patch</li>
<li>instances on both sides of the sync are encouraged to update, especially if the slow pulls are causing issues</li>
</ul>
<h2 id="api-and-export">API and export</h2>
<ul>
<li>[export] Add a proper filename to the event restsearch API’s output to make downloading events a bit more convenient, fixes #4905.</li>
<li>[stix2 import] Dealing with the case of named pipe attribute being imported from custom object.</li>
<li>[stix2 export] Avoid fails with named pipe export as custom object.</li>
</ul>
<h2 id="many-fixes-and-error-handling-improvement">Many fixes and error handling improvement</h2>
<p>Thanks to Jakub Onderka for the tireless review of the code and all the fixes. For a complete overview, check the <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a>.</p>
<h2 id="cve-2019-16202---vulnerability-in-misp-version--24114">CVE-2019-16202 - Vulnerability in MISP version <= 2.4.114</h2>
<h3 id="conditions-to-be-vulnerable">Conditions to be vulnerable</h3>
<p>Any MISP instance version 2.4.114 or below with sync users or organisation administrators allowing incoming synchronisation connections are affected.</p>
<h3 id="details">Details</h3>
<p>By requesting the /servers/index endpoint via the API, authenticated sync and org admin users have access to all synchronisation servers configured, including the API keys used.</p>
<p>The vulnerability was caused by a combination of 3 separate issues:</p>
<ul>
<li>The decision to allow sync users and org admins to have access to the server index was flawed, the idea was that they could assist with finding misconfigurations towards their home instance</li>
<li>The API and the UI code paths handled the query that fetched the server list differently, with the restriction for org admins / sync users missing on the API side</li>
<li>The API keys were included in the output via the API, not taking into the account that users besides site admins could have access to the functionality</li>
</ul>
<p>This allows these users to pivot to the remote instances and authenticate using the acquired sync user keys.</p>
<h3 id="mitigation">Mitigation</h3>
<p>If patching immediately is not an option, whitelisting the IPs of incoming sync accounts to their respective MISP instance IPs avoids any abuse with the obtained keys, though for large sharing communities, this mitigation is not recommended.</p>
<h3 id="fix">Fix</h3>
<p>Upgrade to a version of MISP that has tightened the access control for the vulnerable endpoint (>= 2.4.115). This remedies any future attempts to abuse the vulnerability.</p>
<p>The 2.4.115 release version also introduces tools that ease the purging of the potentially exposed keys, along with logging attempts to access the vulnerable functionality.</p>
<p>The fix itself removes the access of all users besides the site admin to the /servers/index end-point and thus removes the necessity to deal with issue 2 or 3 identified in the details.</p>
<p>Site administrators are encouraged to reset all org admin / sync user API keys via the new reset functionality found at the top of the /admin/users/index page, or by POSTing an empty request to /users/resetAllSyncAuthKeys as a site administrator or executing the reset via the CLI command: <code class="highlighter-rouge">/var/www/MISP/app/Console/cake resetSyncAuthkeys [sync_user_id]</code></p>
<p>Administrators are also encouraged to remotely reset their API keys on instances where the above is not executed by the administrators, by navigating to /servers/index on their own instance and issuing a remote reset for their API keys. This will conveniently issue a reset on the remote instance and store the new key in the sync connection.</p>
<h3 id="credits">Credits</h3>
<p>Guenaëlle De Julis and Céline Massompierre from CERT-XLM of Excellium Services.</p>
<h3 id="timeline">Timeline</h3>
<ul>
<li>2019-09-06 16:25:47: Vulnerability report received from CERT-XLM</li>
<li>2019-09-06 20:25:02 [TLP:amber]: MISP Project confirmed vulnerability to CERT-XLM along with notifying them of an internal fix being ready for co-ordinated publication, scheduled for 2019-09-09 13:00</li>
<li>2019-09-09 13:07:00 [TLP:green]: Co-ordinated limited release, patch released and tagged to GitHub and all known MISP community users notified and encouraged to notify their constituents</li>
<li>2019-09-10 [TLP:white]: CVE ID assignment, publication of tagged version, publishing of this advisory, release of blog post describing the vulnerability</li>
</ul>
<h1 id="acknowledgement">Acknowledgement</h1>
<p>We would like to reiterate the importance of continuous security testing and the reporting of findings. Without the diligent work of security professionals in our community, we would have an infinitely harder time of squashing potential vulnerabilities. Thanks again to everyone that has helped us make MISP more secure.</p>
<p>If you have found a vulnerability in MISP and would like to get in touch with us, please read our <a href="https://www.misp-project.org/security/">vulnerability disclosure notice</a>.</p>
<p>We would like to thank all the <a href="/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2019-09-09T23:00:00+00:00https://www.misp-project.org/2019/09/12/Decaying-Of-IndicatorsMISP - Decaying of Indicators - MISP improved model to expire indicators based on custom models2019-09-11T23:00:00+00:00<h1 id="an-improved-and-flexible-model-to-expire-indicators">An improved and flexible model to expire indicators</h1>
<p>This blog post introduces the new functionality of MISP 2.4.116 which allows users and organisations to easily expire information depending on their objectives and targets.</p>
<p>MISP being a distributed system, various users and organisations are sharing data, sometimes without even knowing each others. While having access to a lot of information is extremely beneficial for all parties, it, however, also induces challenges to deal with.</p>
<p>In this blog post, we will mainly discuss about information <strong>quality</strong> and <strong>freshness</strong>, other issues like <strong>trust</strong>, <strong>use-cases</strong>, <strong>interests</strong>, etc. are partially taken into account but will not be presented. Nevertheless, these concepts are examined in this <a href="https://arxiv.org/abs/1902.03914">paper</a> along with a detailed explanation of the solution we have chosen to tackle these issues.</p>
<p>Our main objective is to provide users a <strong>simple yet customizable system</strong> to automatically (or manually) mark an <em>Indicator Of Compromise</em> (or more generic, an <em>Attribute</em>) as <strong>expired</strong>.</p>
<p>Before getting started to show how the model presented in the paper is implemented in MISP, we first need to have a look at some concepts needed to better understand how components are working and tied together.</p>
<h1 id="the-potentially-annoying-bits-of-theory">The (potentially) annoying bits of theory</h1>
<p>The solution currently supported in MISP is based on two components: <code class="highlighter-rouge">base_score</code> and <code class="highlighter-rouge">score</code>. The idea is to have an initial fixed value called <code class="highlighter-rouge">base_score</code> taking into account the <strong>quality</strong> of an indicator; and a time-dependant <code class="highlighter-rouge">score</code>, which decreases the more time passes.</p>
<p>A simplified version would be something like this:</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>score = base_score * P
</code></pre></div></div>
<p>Where <code class="highlighter-rouge">P</code> is composed of <code class="highlighter-rouge">parameters</code>:</p>
<ul>
<li><code class="highlighter-rouge">lifetime</code>: The lifetime of the IOC or the time at which the score of the <em>Attribute</em>’s score will be 0</li>
<li><code class="highlighter-rouge">decay_speed</code>: The speed at which the decay happens or the speed at which an <em>Attribute</em> will loose score</li>
</ul>
<p><strong>⚠</strong> <strong>It should be noted that everytime a <a href="https://www.circl.lu/doc/misp/sightings/"><em>Sightings</em></a> is added to an <em>Attribute</em>, the <code class="highlighter-rouge">score</code> is refresh to the <code class="highlighter-rouge">base_score</code> and a new decay is initiated from that point.</strong></p>
<h1 id="polynomial-decaying-model-built-in-in-misp">Polynomial Decaying Model built-in in MISP</h1>
<p>We still have to see how the <code class="highlighter-rouge">base_score</code> is actually computed. In the built-in version of the <em>Decaying Model</em> in MISP, the <code class="highlighter-rouge">base_score</code> is computed from the <em>Taxonomies</em> and some weight. Weights are a mean to prioritize extracted <code class="highlighter-rouge">numerical_values</code> from <em>Taxonomies</em> over others.</p>
<p>To give the intuition of how the <code class="highlighter-rouge">base_score</code> computation works, let’s look at two examples. In these examples, the two <em>Taxonomies</em> used are
<a href="https://github.com/MISP/misp-taxonomies/blob/master/phishing/machinetag.json"><em>phishing</em></a> and <a href="https://github.com/MISP/misp-taxonomies/blob/master/admiralty-scale/machinetag.json"><em>admiralty-scale</em></a>. Both of them contain <em>Tags</em> that have a <code class="highlighter-rouge">numerical_value</code> associated to them:</p>
<ul>
<li><img src="/assets/images/misp/blog/decaying//tag-as-A.png" alt="admiraly-scale:source-reliability = Completely reliable" width="300" />, <code class="highlighter-rouge">numerical_value = 100</code></li>
<li><img src="/assets/images/misp/blog/decaying//tag-as-D.png" alt="admiraly-scale:source-reliability = Not usually reliable" width="300" />, <code class="highlighter-rouge">numerical_value = 25</code></li>
<li><img src="/assets/images/misp/blog/decaying//tag-p-H.png" alt="phishing:psychological-acceptability = high" width="250" />, <code class="highlighter-rouge">numerical_value = 75</code></li>
</ul>
<p>So, if an <em>Attribute</em> only have one <em>Tag</em> attached, let’s say <code class="highlighter-rouge">admiralty-scale:source-reliability="Completely reliable"</code>, the <code class="highlighter-rouge">base_score</code> would be:</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>base_score = 100
</code></pre></div></div>
<p>Weights come into action when multiple <em>Tags</em> are attached to an <em>Attribute</em>. To make things a bit easier, let’s suppose that both <em>Taxonomies</em> should have the same importance in regards to the <em>Attribute</em>’s score. Thus, the total weight (100) will be shared, assigning both <em>Taxonomy</em> a weight of 50.</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>admiralty-scale = 50
phishing = 50
---------------------
sum 100
</code></pre></div></div>
<p>If an <em>Attribute</em> has the <em>Tags</em> <img src="/assets/images/misp/blog/decaying/tag-as-A.png" alt="admiraly-scale:source-reliability = Completely reliable" width="300" /> and <img src="/assets/images/misp/blog/decaying/tag-p-H.png" alt="phishing:psychological-acceptability = high" width="250" /> attached, the computation steps would look like this:</p>
<p><img src="/assets/images/misp/blog/decaying/bs-computation-steps.png" alt="base_score computation steps" /></p>
<p>Thus, the <code class="highlighter-rouge">base_score</code> of this <em>Attribute</em> will be <code class="highlighter-rouge">87.50</code>.</p>
<h1 id="short-tutorial">Short tutorial</h1>
<p>Now that we’ve seen the basic concepts, let’s have a look at how MISP implements these components. For these examples, we are using the default <a href="https://github.com/MISP/misp-decaying-models/blob/master/models/phishing-model.json">phishing model</a> model on a <strong>test</strong> <em>Event</em>.</p>
<h2 id="practical-integration-in-misp">Practical integration in MISP</h2>
<h3 id="endpoint-eventsview">Endpoint: <code class="highlighter-rouge">events/view</code></h3>
<p>At the <em>Event</em> level, a new filtering button has been added to attach the real-time computed <code class="highlighter-rouge">score</code> of any <em>Attributes</em> that has been mapped to a <em>Model</em>.</p>
<p><img src="/assets/images/misp/blog/decaying/dm-event.png" alt="Decaying Model index" width="700" /></p>
<h3 id="endpoint-attributerestsearch">Endpoint: <code class="highlighter-rouge">attribute/restSearch</code></h3>
<p>The <code class="highlighter-rouge">attribute/restSearch</code> endpoint has been updated and now supports four new parameters to filter out expired <em>Attributes</em> or play with the different available models.</p>
<ul>
<li><code class="highlighter-rouge">includeDecayScore</code> <strong>[bool]</strong>: Attach the real-time computed <code class="highlighter-rouge">score</code> of the <em>Attribute</em> along with <em>Model(s)</em> informations</li>
<li><code class="highlighter-rouge">excludeDecayed</code> <strong>[bool]</strong>: Filter out all expired IOC</li>
<li><code class="highlighter-rouge">decayingModel</code> <strong>[list]</strong>: List of <em>Model(s)</em>, which will be attached to the <em>Attribute</em></li>
<li><code class="highlighter-rouge">modelOverrides</code> <strong>[dict]</strong>: JSON that can be used to on-the-fly modify <em>Model(s)</em> parameters</li>
</ul>
<p>Example</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>// attribute/restSearch query that gets every `ip-src` attributes being tagged with tlp or phishing,
// not being expired,
// with a overriden model threshold of 30 for the two models with id 84 and 12.
{
"type": "ip-src",
"tags": ["tlp:%","phishing:%"],
"includeDecayScore": 1,
"excludeDecayed": 1,
"modelOverrides": {
"threshold": 30
}
"decayingModel": [84, 12],
}
</code></pre></div></div>
<h2 id="default-and-custom-models">Default and Custom Models</h2>
<p>In MISP, Some <em>Decaying Models</em> called <strong>Default Models</strong> will be supplied by default. Similarly to <em>Taxonomies</em>, <em>Galaxies</em> or <em>misp-objects</em>, <em>Decaying Models</em> will have their <a href="https://github.com/MISP/misp-decaying-models">own repository</a> and will have the possibility to be updated directly from the UI via a single click. <strong>Default Models</strong> are available to everyone, meaning that they can been viewed and customized by any users having a presence on the MISP instance.</p>
<p><strong>Custom Models</strong> are user-defined models that are shared to other users. However, if desired, they can be hidden by turning off the sharing flag, similarly to the <em>Tag Collection</em> feature.</p>
<h2 id="decaying-fine-tuning-tool-setting-parameters-and-mapping-model-to-attribute-types">Decaying Fine Tuning Tool: Setting parameters and mapping model to <em>Attribute</em> types</h2>
<p>When creating a new <em>Decaying Model</em>, setting a parameters and viewing its impact should be as easy and straight forward as possible. To do so, few widgets are shipped with the latest version of MISP.</p>
<h3 id="customizing-lifetime-and-decay-speed-parameters">Customizing lifetime and decay speed parameters</h3>
<video src="/assets/images/misp/blog/decaying/dm-tool.mp4" title="Decaying Model Fine Tuning Tool - Parameters" width="800" height="450" controls="" autoplay="" loop="">
Your browser does not support the video tag.
</video>
<h3 id="setting-the-base_score-customizing-taxonomies-weight">Setting the <code class="highlighter-rouge">base_score</code>: Customizing Taxonomies’ weight</h3>
<video src="/assets/images/misp/blog/decaying/dm-bs.mp4" type="video/mp4" title="Decaying Model Fine Tuning Tool - Base score" width="800" height="450" controls="" autoplay="" loop="">
Your browser does not support the video tag.
</video>
<h3 id="viewing-scores-and-simulating-the-model">Viewing scores and simulating the model</h3>
<video src="/assets/images/misp/blog/decaying/dm-simulation.mp4" type="video/mp4" title="Decaying Model Simulation Tool" width="800" height="450" controls="" autoplay="" loop="">
Your browser does not support the video tag.
</video>
<h1 id="developer-perspective-creating-a-model-using-a-different-algorithm">Developer perspective: Creating a model using a different algorithm</h1>
<p>The Built-in Polynomial <em>Decaying Model</em> implemented in MISP allows any user to customize various components to achieve fine-grained decay behaviors. Still, it is possible that our model doesn’t encompass your specific use-case. Thanks to the implemented architecture, any other formulas or algorithms can be added and used in a straightforward way.</p>
<p>Steps to create a new decay algorithm:</p>
<ul>
<li>Create a new file <code class="highlighter-rouge">$filename</code> in <code class="highlighter-rouge">app/Model/DecayingModelsFormulas/</code></li>
<li>Extend the <strong>Base</strong> class <code class="highlighter-rouge">DecayingModelBase</code></li>
<li>Implement the two functions <code class="highlighter-rouge">computeScore</code> and <code class="highlighter-rouge">isDecayed</code> with you own formula/algorithm</li>
<li>Create a <em>Model</em> and set the <code class="highlighter-rouge">formula</code> field to <code class="highlighter-rouge">$filename</code></li>
</ul>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code><?php
include_once 'Base.php';
class Polynomial extends DecayingModelBase
{
public const DESCRIPTION = 'The description of your new decaying algorithm';
public function computeScore($model, $attribute, $base_score, $elapsed_time)
{
// algorithm returning a numerical score
}
public function isDecayed($model, $attribute, $score)
{
// algorithm returning a boolean stating
// if the attribute is expired or not
}
}
?>
</code></pre></div></div>
<h1 id="outcomes">Outcomes</h1>
<p>Evaluating <strong>quality</strong> and <strong>freshness</strong> of IOCs is a problem commonly found in Threat Intelligence Platforms. We tried to solve it using a simple yet customizable system.</p>
<p>Upon release, MISP will be shipped with few models that could fit most use-cases. Still, we are eagerly waiting for contributions, fine-tunings or feedbacks from users. This would opens up plenty of opportunities including improved <em>Models</em>’ precision, parameters tweaking or even integration of machine learning as a new <em>Model</em> algorithm.</p>
<p>Furthermore, we are not done yet! There are already improvements cooking in the MISP-Project oven,</p>
<ul>
<li>Integration of <code class="highlighter-rouge">False Positive</code> and <code class="highlighter-rouge">Expiration</code> <em>Sightings</em></li>
<li>Formula tweaking to provide better control on how to reset the <code class="highlighter-rouge">base_score</code> once a <em>Sighting</em> is created</li>
<li>Per-user Taxonomies’ <code class="highlighter-rouge">numerical_value</code> overrides</li>
<li>Weights on <em>Tag</em>’s predicate level</li>
</ul>2019-09-11T23:00:00+00:00https://www.misp-project.org/2019/08/31/MISP.2.4.114.releasedMISP - MISP 2.4.114 released (aka the community care package release)2019-08-30T23:00:00+00:00<h1 id="misp-24114-released">MISP 2.4.114 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.114">2.4.114</a>) with some new features supporting collaboration and a list of fixes and small improvements. We strongly recommend to update to this version.</p>
<h2 id="letting-the-world-know-about-your-community">Letting the world know about your community</h2>
<p>One of the most common questions we get from users is whether we can point them to a community that would fit their profile and needs. This is something that often leaves as stumped. Being an open source project, we only really know the part of our user-base that we directly interact with and even if they do, the question of whether we should point users in their directions in the first place is often a puzzling one.</p>
<p>We’ve decided to make everyone’s life just a tad bit easier. By incorporating an in-application registry of known communities, we not only allow organisations that run an ISAC or other sharing community to let potential new community members know that they exist in the first place, but also we also allow anyone with a MISP installation to conveniently send requests to communities for access.</p>
<p>Simply go to sync actions -> communities, browse the communities vetter or at least known by the MISP project and pick the ones that you consider yourself a good fit for. The system allows you to describe who you are and why you feel that you’d be an asset to the given community and send a request directly to the administrators of the instance.</p>
<p>The list of communities for now is rather brief, if you would like your community to be listed, get in touch us at the MISP project, or create a pull request describing your community.</p>
<h2 id="keeping-an-eye-on-incoming-delegation-requests">Keeping an eye on incoming delegation requests</h2>
<p>As with all new features in MISP, we often struggle with anticipating the interest a new system would generate, often under-estimating the volume of data that they would generate. When we first implemented the delegation system, we expected it to be more of an edge-case scenario. We were obviously wrong, several communities out there rely quite heavily on being able to pseudo-anonymously publish data.</p>
<p>This is especially the case in ISAC/ISAO driven communities, where a central trusted authority ensures both the quality of the data produced as well as protecting the identity of those that wish to remain unknown when disclosing information that could be considered a successful intrusion.</p>
<p>We have now added an interface that allows users to search both received and issued delegation requests in a more convenient manner.</p>
<h2 id="quality-of-life-improvements-for-administrators">Quality of life improvements for administrators</h2>
<p>Added a new diagnostic tool that allows administrators to keep track of the database table sizes in MISP along with the potentially recoverable space by optimising the table.</p>
<h2 id="taxonomies-improved-with-the-addition-of-an-industrial-control-systems-and-operational-technology-icsot-taxonomy">Taxonomies improved with the addition of an Industrial control systems and operational technology (ICS/OT) Taxonomy</h2>
<p>Industrial control systems and operational technologies (ICS/OT) are often the target of threats, intrusions and attacks. The <a href="https://www.first.org/global/sigs/cti/">FIRST.org Cyber Threat Intelligence SIG</a> did a tremendous work of documenting these into a series of taxonomies. To support and actively test the use of the ICS/OT taxonomy, the <a href="https://www.misp-project.org/taxonomies.html#_ics">ics taxonomy</a> is now part of the default MISP taxonomy library. We also encourage any ICS/OT operators to contribute back to the <a href="https://github.com/MISP/misp-taxonomies/blob/master/ics/machinetag.json">ics taxonomy JSON file</a> in order to improve the taxonomy based on their experiences. By being a taxonomy in MISP, this allows all ICS/OT users to directly tag and contextualise information shared within MISP instances and communities to describe their domain specific incidents and reports along with the related industrial threat intelligence.</p>
<h2 id="fixes-and-improvements">Fixes and improvements</h2>
<ul>
<li>[contact reporter] Various fixes ensuring that the right users can be contacted</li>
<li>[API] A long list of fixes ensuring consistency and proper responses for the less used endpoints, based on <a href="https://github.com/rafiot/">@rafiot</a>’s exhaustive test suite</li>
<li>[API] Fixed output of the attribute histogram. No more STIX-ish barf inducing numeric string keys for dictionaries</li>
<li>[Feeds and warninglists] A long list of fixes tuning the performance of said subsystems</li>
<li>[PostgreSQL] A list of fixes, making MISP work on psql</li>
<li>[Import modules] Ensuring that the new, object supporting import modules can be called via the API</li>
<li>[other] Various other fixes touching a long range of features, such as UI issues, object merge problems, invalid links and many more</li>
</ul>
<p>We would like to thank all the <a href="/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large.</p>
<p>Special shout-outs to Jakub Onderka (<a href="https://github.com/JakubOnderka">@JakubOnderka</a>) for the tireless work around tuning the warninglist systems and fixes all around, to Pierre-Jean Grenier (<a href="https://github.com/zaphodef">@zaphodef</a>) for the massive list of fixes ensuring that our APIs behave more sanely and Beckhalo Evgeny (<a href="https://github.com/4ekin">@4ekin</a>) for taming the beast that is PostgreSQL support.</p>
<p>We would also like to make a special dedication to the funding support of <a href="https://twitter.com/circl_lu">CIRCL</a> and <a href="https://twitter.com/inea_eu">INEA</a> under the CEF Telecom <a href="https://ec.europa.eu/inea/sites/inea/files/cef_telecom_supported_actions_november_2018.pdf">2016-LU-IA-0098 grant</a>.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2019-08-30T23:00:00+00:00https://www.misp-project.org/2019/08/19/MISP.2.4.113.releasedMISP - MISP 2.4.113 released (aka the bugs fixing marathon)2019-08-18T23:00:00+00:00<h1 id="misp-24113-released">MISP 2.4.113 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.113">2.4.113</a>) with tons of fixes and small improvements. We strongly recommend to update to this version.</p>
<h2 id="api-and-sync">API and sync</h2>
<ul>
<li>[API] get individual server settings via /servers/getSetting/[setting_name], fixes #4964.</li>
<li>[API] Allow posting freetext data for ingestion via the event UUID instead of ID, fixes #4995.</li>
<li>[internal / API] new component added to handle repeatable code across all controllers (toolbox controller)
<ul>
<li>added UUID -> ID lookup function and integrated it across several functions</li>
<li>fixes #4990</li>
<li>fixes #4999</li>
<li>fixes #4993</li>
<li>fixes #4991</li>
<li>fixes #4989</li>
<li>fixes #4987</li>
</ul>
</li>
<li>[sync] Added a protection from receiving empty published events from other instances.
<ul>
<li>a temporary solution to some older, bugged instances emitting them</li>
</ul>
</li>
<li>[sync] Sync object builder tool fixed.
<ul>
<li>was picking the wrong org as the owner of the remote side</li>
</ul>
</li>
<li>[sync] Fixed an invalid massaging of object attributes before a sync.
<ul>
<li>on a push, object attributes were not correctly filtered out based on distribution settings</li>
</ul>
</li>
<li>[API] Attribute add rework. Handle attribute creation in a unified manner via captureAttributes</li>
<li>Show sharing groups’ uuids.</li>
<li>Delete an object by its uuid, similar syntax to attribute’s deletion.</li>
<li>[stix test] Updated STIX1 test files with the updated MISP event files export results.</li>
<li>[stix test] Updated MISP event test files with the latest objects supported.</li>
<li>[logging] Truncate description lengths that would be longer than what
the DB can store with the default setup.</li>
<li>[stix export] Change on leveraged ttp at incident level.
<ul>
<li>No longer referencing ttps created out of MISP objects as leveraged ttps at incident level</li>
<li>Making sure all ttps, course of actions, threat actors and so on created from MISP galaxies are referenced at incident level</li>
</ul>
</li>
<li>[six export] Handling vulnerability attributes the same way as objects.
<ul>
<li>Fixing at the same time some references (with vulnerability objects related to vulnerability attributes) that were lost</li>
</ul>
</li>
<li>[stix export] Better tags handling.
<ul>
<li>Avoid passing event level tags everywhere</li>
<li>Using class variable for the tlp markings</li>
</ul>
</li>
<li>Modules can now pre-check a checkbox from userConfig.</li>
<li>[types] email-subject added as a valid type for network activity.
<ul>
<li>used to describe outgoing e-mail subjects for exfiltration. Perhaps consider adding a new category for exfiltration altogether.</li>
</ul>
</li>
<li>[API] servers/serverSettingsEdit now accepts the force parameter in a posted JSON object.</li>
<li>[API] get organisation by uuid for sightings/listSightings, fixes #4992.</li>
<li>[API] Misp object delete’s uuid lookup fixed.</li>
<li>[API] removed testing exception.</li>
<li>[API] Swapped error messages’ content from “don’t” to “do not” to avoid weird sanitisation artifacts coming from the exception handler.</li>
<li>[API] error message.</li>
<li>[API] Attribute edit fixed.</li>
<li>[API] /galaxies/view by uuid added, fixes #4993.</li>
<li>[API] sightings restSearch now accepts uuids as org_id, fixes #4992.</li>
<li>[API] Delete sightings by UUID, fixes #4987.</li>
<li>[API] /objects/view should accept UUID as a parameter instead of just ID, fixes #4991.</li>
<li>[API] Delete organisations by UUID, fixes #4989.</li>
<li>[API] Access event proposals by uuid via shadow_attributes/index/[uuid], fixes #4988.</li>
<li>[API] Adding an event without the info field set should never work, fixes #4984.</li>
</ul>
<h2 id="ui">UI</h2>
<ul>
<li>[enrichment] Handling correctly comments at objects level.
<ul>
<li>Objects level comments were displayed but not handled at the end, they are now displayed, users can modify them as comments at attributes level, and they are handled then with the saved results</li>
</ul>
</li>
<li>[UI] Handle settings being removed from config.php more gracefully in the UI.</li>
<li>[UI] Row description added in View Warninglists.</li>
<li>[UI] Improved the accessibility of the galaxy matrix view for screen readers. The table elements are now focusable, and only a short text is brailled/spoken by default.</li>
</ul>
<h2 id="internal">internal</h2>
<ul>
<li>[session handling] Session handling fixes.
<ul>
<li>changed the cookie name to MISP-[MISP.uuid] to rely on a unique data-point instead of the URL. This solves issues with multiple MISPs running on the same host via port based virtualhosts
sharing sessions</li>
<li>timeout issues potentially fixed when using the recommended PHP session handler. If the garbage collection is configured in php.ini it could previously purge sessions that based on the session timeout should still be valid</li>
</ul>
</li>
<li>[debug] Added an on-demand sync debug to assist some debug sessions.
<ul>
<li>very primitives, simply concatenates events to be pushed into a file</li>
</ul>
</li>
<li>[internal] Default field list added for attributes.
<ul>
<li>let’s try to standardised on things we output instead of doing it manually. It’s a first step</li>
</ul>
</li>
<li>[warning-list] Filter CIDR warning list before eval.</li>
<li>[internal] Potential fix for a race condition generating orphaned attributes, fixes #4886.
<ul>
<li>This fix will avoid issues where the delay is introduced by the deferred start of the execution via the background workers</li>
<li>deleting an event whilst data is being actively added will still not be interrupted</li>
</ul>
</li>
<li>[internal] Feed lookup by UUID removed as feeds don’t actually have UUIDs, fixes #4998.</li>
</ul>
<h2 id="misp-modules">misp-modules</h2>
<p><a href="https://misp.github.io/misp-modules/">misp-modules</a> have been improved with new modules especially an improved cuckoo import module (thanks to Pierre-Jean Grenier). The documentation has been also improved (thanks to all the contributors who helped us on the documentation).</p>
<p><a href="https://www.misp-project.org/galaxy.html">MISP galaxies</a>, <a href="https://www.misp-project.org/objects.html">MISP object templates</a> and <a href="https://github.com/MISP/misp-warninglists/">MISP warning-lists</a> have been updated to the latest version. MISP galaxy now includes a target-location galaxy to improve classification.</p>
<p>We would like to thank all the <a href="/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2019-08-18T23:00:00+00:00https://www.misp-project.org/2019/08/01/MISP.2.4.112.releasedMISP - MISP 2.4.112 released (aka summer fixes and improvement)2019-07-31T23:00:00+00:00<h1 id="misp-24112-released">MISP 2.4.112 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.112">2.4.112</a>) has been released with a host of API fixes, improvements and a security fix.</p>
<h2 id="improvements">Improvements</h2>
<ul>
<li>[sync] Event index cleaned up, total count of listed events added as X-Result-Count header</li>
<li>[sync] Previewing a remote instance now passes pagination rules in the request instead of fetching the full data-set and paginating in memory. This also include a fix to issues with empty preview pages. Massive performance boost when previewing a remote instance. This requires the remote side to be the same version or newer.</li>
<li>
<p>[API] New parameters added to attributes/restSearch to include additional context, fixes #4935, fixes #4940, affects MISP/PyMISP#415.</p>
<ul>
<li>includeSightings: include sightings for all attributes returned</li>
<li>includeCorrelations: include the correlations to other attributes (includes a light-weight event object with each attribute)</li>
</ul>
</li>
<li>[cli] Added cleanCaches command.</li>
<li>[API] Disable background processing on-demand via URL parameters.</li>
<li>[API] Disable DB logging completely, fixes #4921.</li>
<li>[API] IncludeContext now includes the additional event fields in the attributes/restSearch results (in JSON format).</li>
<li>[data model] New attribute type weakness (CWS) added</li>
<li>[alerting] Block the alerting of events based on the date field as an alternative to the timestamp, fixes #4937.</li>
<li>[warning-list] Speedup improvement in the CIDR lookup.</li>
<li>[UI] Add a quick button for the event attribute toolbar for the showing of related tags.</li>
<li>[restClient] Do not override query body if url hasn’t changed.</li>
<li>[feed-metadata] Panels Tracker feed added.</li>
<li>[eventGraph:search] Usage of chosen instead of bootstrap with non- stripped label.</li>
</ul>
<h2 id="bugs-fixed">Bugs fixed</h2>
<p>Many bugs fixed based on the extensive PyMISP test cases in addition to manual reviews. All fixes are documented in the <a href="https://www.misp-project.org/Changelog.txt">changelog</a>.</p>
<h2 id="cve-2019-14286-fixed">CVE-2019-14286 fixed</h2>
<p><a href="https://cve.circl.lu/cve/CVE-2019-14286">CVE-2019-14286</a> has been fixed. In app/webroot/js/event-graph.js in MISP 2.4.111, a stored XSS vulnerability exists in the event-graph view when a user toggles the event graph view. A malicious MISP event must be crafted in order to trigger the vulnerability. This vulnerability has been fixed in MISP 2.4.112. We strongly encourage everyone to update as soon as possible. Thanks to David Heise who reported the vulnerability.</p>
<h2 id="misp-modules">misp-modules</h2>
<p><a href="https://misp.github.io/misp-modules/">misp-modules</a> have been improved with new modules especially with a new advanced CVE module which includes the ability to import CVEs along with their associated weaknesses and attack techniques (as you can see in the screenshot). The documentation has been also improved (thanks to all the contributors who helped us on the documentation).</p>
<p><a href="https://www.misp-project.org/galaxy.html">MISP galaxies</a>, <a href="https://www.misp-project.org/objects.html">MISP object templates</a> and <a href="https://github.com/MISP/misp-warninglists/">MISP warning-lists</a> have been updated to the latest version. MISP galaxy has been updated to include the July edition of the MITRE ATT&CK model.</p>
<p>We would like to thank all the <a href="/contributors">contributors</a>, reporters and users who have helped us in the past months to improve MISP and information sharing at large.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2019-07-31T23:00:00+00:00https://www.misp-project.org/2019/07/19/MISP.2.4.111.releasedMISP - MISP 2.4.111 released (aka improved proposal sync)2019-07-18T23:00:00+00:00<h1 id="misp-24111-released">MISP 2.4.111 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.111">2.4.111</a>) has been released with an improved proposal sync, minor improvements and bugs fixed.</p>
<h2 id="proposal-synchronisation-rework">Proposal synchronisation rework</h2>
<p>The proposal synchronisation has undergone a long over-due rewrite and as a result it has been significantly improved compared to the original implementation, which was released several years ago. We strongly invite all users of MISP to upgrade
to the latest version to restore the fetch-on of proposals via the synchronisation. The proposal index has been reworked and proposal pull is now limited to the last 14 days (to avoid trying to pull ancient proposals at each sync).</p>
<h2 id="new-attribute-type-community-id-added">New attribute type community-id added</h2>
<p>At the MISP project, we are big supporters of new open standards, which can help communities in an effort to reference forensic evidences, especially network forensic evidences. It has always been difficult to track down common network flows as many tools and products rely on different methods to build network flow ids. <a href="https://github.com/ckreibich">Christian Kreibich</a> from Corelight decided to take a bash at resolving this issue and has been working on creating the <a href="https://github.com/corelight/community-id-spec">Community ID Flow Hashing</a> format. As the community-id is open to open source implementations which can be reused, various open source projects already support it such as Zeek (Bro), Suricata, Moloch, HELK, Elastic and now also MISP, as of version 2.4.111.</p>
<p>In 2.4.111, a new attribute type has thus been added, along with the following object templates already including the new attribute field:</p>
<ul>
<li><a href="https://www.misp-project.org/objects.html#_netflow">Netflow</a></li>
<li><a href="https://www.misp-project.org/objects.html#_network_connection">Network connection</a></li>
</ul>
<p>This feature allows to easily correlate network forensic flows from different tools or network equipment.</p>
<h2 id="improvements-and-bugs-fixed">Improvements and bugs fixed</h2>
<ul>
<li>[misp-modules enrichment] Fixed index in attribute.</li>
<li>[API] Deletes broken due to invalid boolean.</li>
<li>[API] Delete http method/requests properly accepted by some /delete endpoints.</li>
<li>[sync] Fixed a bug breaking the synchronisation between MISP instances.</li>
<li>[stix2] Import of User Account objects is now supported.</li>
<li>Issues #4864, #4861, #4847 fixed</li>
</ul>
<p><a href="https://www.misp-project.org/galaxy.html">MISP galaxy</a>, <a href="https://www.misp-project.org/objects.html">MISP object templates</a> and <a href="https://github.com/MISP/misp-warninglists/">MISP warning-lists</a> have been updated to the latest version.</p>
<p>We would like to thank all the contributors, reporters and users who have helped us in the past months to improve MISP and information sharing at large.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2019-07-18T23:00:00+00:00https://www.misp-project.org/2019/07/08/MISP.2.4.110.releasedMISP - MISP 2.4.110 released (aka local-tags and new MISP modules supporting MISP standard format)2019-07-07T23:00:00+00:00<h1 id="misp-24110-released">MISP 2.4.110 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.110">2.4.110</a>) has been released with a host of new features, improvements, many bugs fixed and one security fix. Even under the searing summer sun, the MISP-project team is hard at work, whilst enjoying some cocktails (with or without booze).</p>
<h1 id="new-main-features">New main features</h1>
<h2 id="misp-modules-extended-to-support-the-full-misp-standard-format">MISP modules extended to support the full MISP standard format</h2>
<p><a href="https://github.com/MISP/misp-modules">misp-modules</a> now support MISP objects and relationships. The revamped system is still compatible with the old modules, whilst the new modules bolster up the complete MISP standard format. New modules such as <a href="https://github.com/MISP/misp-modules/blob/52dadd2df32b19241fdd978e50b717f1967e264b/misp_modules/modules/expansion/urlhaus.py">url-haus</a>, <a href="https://github.com/MISP/misp-modules/blob/be61613da4f5dc8f082a7c1a9e1ec07fdb872560/misp_modules/modules/expansion/joesandbox_query.py">joe sandbox query</a> and many others support the new MISP standard format. This new feature allows module developers to create more advanced modules, generating MISP objects and associated relationships from any type of expansion, import or export modules in one click.</p>
<p><img src="/assets/images/misp/blog/misp-modules-new.png" alt="" />
<img src="/assets/images/misp/blog/misp-modules-2.png" alt="" /></p>
<h2 id="local-tags-introduced">Local tags introduced</h2>
<p><img src="/assets/images/misp/blog/local-tags.png" alt="" /></p>
<p>The long awaited feature “local tags” is now finally available. You can create tags locally if you are a member of the given MISP instance’s host organisation, enabling “in-place” tagging for synchronisation and export filtering. MISP events are not modified while using the local tags and are in turn always stripped before being synchronised with other MISP instances and sharing communities. Local tags allow users to avoid violating the ownership model of MISP, but still be able to tag any event or attribute for further dissemination and data contextualisation. Local tagging works for tags, tag collections, galaxies and matrix-like galaxies such as ATT&CK.</p>
<h2 id="new-norwegian-translation">New Norwegian translation</h2>
<p>Thanks to the contribution from <a href="https://github.com/Kortho">Kortho</a>, the MISP user-interface now includes a Norwegian translation in addition to the previously contributed Japanese, French translations along with multiple work in progress translation efforts getting closer to full coverage, such as Russian, German and Chinese. If you wish to contribute, feel free to join the <a href="https://crowdin.com/project/misp">crowdin page for MISP</a>. It’s simple and efficient, translations can be easily done via the web interface.</p>
<h1 id="various-updates-and-improvements">Various updates and improvements</h1>
<ul>
<li><a href="https://twitter.com/speshulted/status/1141711388617904128">Following SANS courses feedback</a>, physics can be enabled/disabled on demand.</li>
<li>[UI] Filter has been added in the template object index.</li>
<li>[API] On-demand inclusion of attribute relations via the event view endpoint. Thanks to Siemens for the ideas and feedback.</li>
<li>[security] Made certain settings modifiable via the CLI only. Some settings are too risky to be exposed, even to site admins, so made them CLI accessible only.</li>
<li>[API] New option to excludeLocalTags to events/restSearch.</li>
<li>[UI] Many improvements in the event view regarding related events. In case of multiple correlations, the related events are now in a scrollable box.</li>
<li>[Doc] Installation guides and scripts were improved.</li>
<li>[Bug] Fix an old hard-coded path for the temp directory.</li>
<li>[API] Simple worker management added.</li>
</ul>
<h1 id="security-fix-cve-2019-12868">Security fix (CVE-2019-12868)</h1>
<p><a href="https://cve.circl.lu/cve/CVE-2019-12868">CVE-2019-12868</a> has been fixed in MISP 2.4.110. MISP 2.4.109 had remote command execution by a super administrator because the PHP file_exists function is used with user-controlled entries, and phar:// URLs trigger deserialisation. This vulnerability can only be triggered by the site admin. Thanks to Dawid Czarnecki for reporting it.</p>
<h1 id="stix-improvements">STIX improvements</h1>
<ul>
<li>Parsing observable compositions from external STIX files.</li>
<li>Fixing issues with ‘parse’ being called on bundles containing custom objects.</li>
<li>Fixed user account pattern and user account observable extension in STIX 2.0 export.</li>
<li>Fixed socket extension parsing.</li>
<li>Fixed registry-key keys and values parsing for patterns.</li>
</ul>
<p><a href="https://www.misp-project.org/galaxy.html">MISP galaxy</a>, <a href="https://www.misp-project.org/objects.html">MISP object templates</a> and <a href="https://github.com/MISP/misp-warninglists/">MISP warning-lists</a> have been updated to the latest version.</p>
<p>We would like to thank all the contributors, reporters and users who have helped us in the past months to improve MISP and information sharing at large.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2019-07-07T23:00:00+00:00https://www.misp-project.org/2019/06/14/MISP.2.4.109.releasedMISP - MISP 2.4.109 released (aka cool-attributes-to-object)2019-06-13T23:00:00+00:00<h1 id="misp-24109-released">MISP 2.4.109 released</h1>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.109">2.4.109</a>) has been released with a host of new features, improvements, bug fixes and a minor security fix. We strongly advise all users to update their MISP installations to this latest version.</p>
<h1 id="new-main-features">New main features</h1>
<h2 id="encapsulate-existing-attributes-into-an-object">Encapsulate existing attributes into an object</h2>
<p>When an analyst inserts information into MISP, it’s very common to start with a set of unstructured indicators/attributes. At a later stage, common structures emerge and combining attributes into objects start making more and more sense. However, the effort spent on the process of attribute creation would have to be repeated in prior versions via the object creation interface, something that resulted in analysts deciding to save time and effort and move on, leaving the unstructured data as is. To reduce the workload needed to bring structure to our prior work, we have now introduced a new feature, allowing users to easily select a set of attributes and automatically propose suitable object templates depending on the combination of types of the selected attributes. These in turncan be gathered and processed into the desired object.</p>
<h2 id="improved-attck-and-attck-like-matrix-support">Improved ATT&CK and ATT&CK-like matrix support</h2>
<p><img src="https://www.misp-project.org/assets/images/misp/blog/attack-new.png" alt="" />
<img src="https://www.misp-project.org/assets/images/misp/blog/fraud-tactics.png" alt="" /></p>
<p>We received exhaustive feedback during the FIRST.org CTI conference in London and the <a href="https://www.attack-community.org/">ATT&CK EU community</a> workshop at Eurocontrol concerning the ATT&CK integration in MISP. The matrix visualisation has been improved by sorting and reorganising the individual techniques based on their aggregate scores. These statistics can now easily be queried based on time-ranges, organisations, tags, along with all other restSearch enabled filters to generate ATT&CK like matrix views.</p>
<h1 id="security-fix---cve-2019-12794">Security fix - CVE-2019-12794</h1>
<p>An issue was discovered in MISP 2.4.108. Organisation admins could reset credentials for site admins (organization admins have the inherent ability to reset passwords for all of their organization’s users) or impersonate them by reusing their API keys. This could be abused in a situation where the host organisation of an instance decides to use organisation admins to further manage their own users. The potential for abuse is limited to situations where the host organisation of an instance creates lower-privilege organisation admins instead of the usual site admins, so whilst it was indeed in the spirit of what the powers of organisation admins are, we agree that this was a bad design decision. <a href="https://cve.circl.lu/cve/CVE-2019-12794">CVE-2019-12794</a> Thanks to Raymond Schippers for the report.</p>
<h2 id="api">API</h2>
<ul>
<li>[API] added new restSearch filter - date.
<ul>
<li>deprecated to and from</li>
<li>date works similarly to timestamp, accepted syntax options:
<ul>
<li>time ranges in the shorthand format (7d or 24h, etc)</li>
<li>timestamps</li>
<li>fallback parsing for other formats (2019-01-01, “fortnight ago”, etc)</li>
<li>date ranges using lists [14d, 7d]</li>
</ul>
</li>
</ul>
</li>
</ul>
<h1 id="bugs-fixed">Bugs fixed</h1>
<ul>
<li>A long-standing bug has been fixed when adding tags or galaxies whilst using Firefox.</li>
<li>[permissions] Fixed the default sync/user/publisher permissions to include perm_tagger and perm_tag_editor(sync only).</li>
<li>And many other <a href="https://www.misp-project.org/Changelog.txt">fixes</a>.</li>
</ul>
<h1 id="misp-galaxy-object-templates-and-warning-lists-updated">MISP galaxy, object templates and warning-lists updated</h1>
<p><a href="https://www.misp-project.org/galaxy.html">MISP galaxy</a>, <a href="https://www.misp-project.org/objects.html">MISP object templates</a> and <a href="https://github.com/MISP/misp-warninglists/">MISP warning-lists</a> have been updated to the latest version.</p>
<p>New <a href="https://www.misp-project.org/feeds/">default feeds</a> were added in MISP. Don’t hesitate to contact us if you have any idea for new feeds.</p>
<p>We would like to thank all the contributors, reporters and users who have helped us in the past months to improve MISP and information sharing at large.</p>
<p>As always, a detailed and <a href="https://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>
<h1 id="warning-next-release-24110">Warning: Next release 2.4.110</h1>
<p>The next version of MISP will include major changes to the data-model by introducing new functionalities that support forensic capabilities, with a special focus on improving the time representation of MISP attributes and objects. The next release will update various tables in the database as usual, but the automatic update might take longer than usual (on larger instances between 30 and 45 minutes) depending on the number of attributes stored in the instance. During the update procedure, MISP will be unavailable until the update is complete. We will notify our users in advance to prepare their upgrade plan for the next release 2.4.110.</p>2019-06-13T23:00:00+00:00https://www.misp-project.org/2019/06/05/MISP.2.4.108.releasedMISP - MISP 2.4.108 released (aka copy-paste-and-sync feature)2019-06-04T23:00:00+00:00<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.108">2.4.108</a>) has been released with a host of new features, improvements and bugs fixed. We strongly advise all users to update their MISP installations to this latest version.</p>
<h1 id="new-main-features">New main features</h1>
<h2 id="a-copy-paste-and-sync-function">A copy-paste-and-sync function</h2>
<p>A new tool has been added in MISP to create MISP sync configuration objects in JSON format from the user-interface. This significantly improved the setup of synchronisation links between MISP instances. The synchronisation can now be set up (in addition to the standard setup) in 2 simple steps:</p>
<ul>
<li>Use your sync user account on the remote MISP instance to extract the sync config in one click;</li>
<li>paste the sync config into your own instance as a site-admin user.</li>
</ul>
<p>That’s it, you have the synchronisation configured.</p>
<h2 id="improved-paranoid-logging">Improved “paranoid” logging</h2>
<p>During the <a href="https://securitymadein.lu/news/ceis-securitymadein-lu-enforce-project/">enforce</a> training session in Paris, law enforcement officers mentioned the need for LEA to have extensive audit mechanisms in regards to information read and user access in general. A new optional paranoid logging functionality has been added to log any queries from the user-interface and the API of a MISP instance. The feature has two sub-features, allowing administrators to configure their MISPs to log the POST/PUT bodies as well as the ability to force paranoid log entries to skip being stored in the database, instead publish the gathered information exclusively via one of the various pub-sub channels (such as ZMQ, Kafka or ElasticSearch ZMQ, Kafka or ElasticSearch) or via syslog.</p>
<h2 id="api">API</h2>
<ul>
<li>New logical ‘AND’ for tag filters has been added in restSearch API.</li>
<li>Added object_relation as a filter for both the event/attribute restSearch functions.</li>
<li>[restResponse] Added documentation for adding tags on Objects.</li>
<li>[API] Allow more flexibility on the return content types. [iglocska]</li>
</ul>
<h1 id="various-improvements">Various improvements</h1>
<ul>
<li>[logging] Added verbose logging to the server sync test throwing an unexpected error.</li>
<li>[bug] A bug in the event graph displayed broken icons to some specific browsers. The bug was fixed by updating font-awesome 5.8.2 and the loading of font-awesome in visjs.</li>
<li>[event:view] Correctly display title to large by truncating (+ellipsis).</li>
<li>[diagnostic:view] Improved visibility of the <code class="highlighter-rouge">updateAllJson</code> update button.</li>
<li>[object:add] Disable the first select’s option when adding a new row.</li>
<li>[object:add] Added empty option support in select inputs when creating an object.</li>
<li>[UI] Event lock concatinating quoted empty strings.</li>
<li>[UI] Double sanitisation of org view fixed, fixes #4704.</li>
<li>[sync] Further fixes to the deleted flag changes breaking things.</li>
<li>[authkey] Fixed The authkey variable (Viper should work again) (#4694)</li>
<li>[sync] Critical bug fixed that blocked attributes from being included in a push. due to the change to the deleted flag that was not reflected in the way we prepare events for the synchronisation</li>
<li>[UI] Add the create server sync description menu to the server list.</li>
<li>[sync] whitelist fields that can be added via the JSON config.</li>
<li>[UI] Invalid redirect fixed.</li>
<li>[organisation:view] Fixed spinner when viewing events from an org.</li>
<li>[API] Weird responses from JSON objects fixed when data returned is empty.</li>
<li>[API] Wrong JSON output when /events/index returns empty result, fixes #4690.</li>
<li>[UI] Org index filter fixed.</li>
<li>[stix2 import] Fixed external domain & x509 patterns import.</li>
<li>[freetext import] Fixed shadow attribute import.</li>
<li>[event:view] Correctly support the new <code class="highlighter-rouge">deleted</code> parameter behavior.</li>
<li>[UI] Fixed checklocks polluting the top bar.</li>
<li>[enrichment:popover] Correctly fadeout when clicking on the close button.</li>
<li>[STIX] STIX upload fixed for API use.</li>
<li>[galaxy:add] Consider both model names when doing a mass cluster addition.</li>
<li>[installer] Checksum checker has been fixed and improved.</li>
<li>[stix import] Fixed email attachments parsing.</li>
<li>[stix import] Supporting multi attachment attributes for the email object.</li>
</ul>
<h1 id="misp-modules">MISP modules</h1>
<p>Many new <a href="https://github.com/MISP/misp-modules">MISP modules</a> were added such as Joe Sandbox integration.</p>
<h1 id="misp-galaxy-object-templates-and-warning-lists-updated">MISP galaxy, object templates and warning-lists updated</h1>
<p><a href="https://www.misp-project.org/galaxy.html">MISP galaxy</a>, <a href="https://www.misp-project.org/objects.html">MISP object templates</a> and <a href="https://github.com/MISP/misp-warninglists/">MISP warning-lists</a> have been updated to the latest version.</p>
<p>New <a href="https://www.misp-project.org/feeds/">default feeds</a> were added in MISP. Don’t hesitate to contact us if you have any idea for new feeds.</p>
<p>We would like to thank all the contributors, reporters and users who have helped us in the past months to improve MISP and information sharing at large.</p>
<p>As always, a detailed and <a href="http://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2019-06-04T23:00:00+00:00https://www.misp-project.org/2019/05/13/MISP.2.4.107.releasedMISP - MISP 2.4.107 released (aka similar objects review, yara native export)2019-05-12T23:00:00+00:00<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.107">2.4.107</a>) has been released with a host of new features, improvements and security fixes. We strongly advise all users to update their MISP installation to this latest version.</p>
<h1 id="new-main-features">New main features</h1>
<h2 id="similar-objects-and-an-easy-to-use-tool-to-merge-them">Similar objects and an easy to use tool to merge them</h2>
<p>MISP objects are now a cornerstone of describing complex data-structure along with other aspects of threat intelligence. We have seen a regular process of analysts to add new objects and having similar objects in their analysis. In MISP 2.4.107 shows similar objects (with common attributes) and proposes merging strategies into existing objects. The user-interface is easy to use and part of the standard project.</p>
<h2 id="native-yara-and-yara-json-export">Native yara and yara-json export</h2>
<p>For a very long time, MISP supported the sharing of pre-crafted <a href="https://virustotal.github.io/yara/">YARA</a> attributes and objects. As of 2.4.107, we’ve introduced the ability to export YARA rules generated from any existing attributes in MISP, via the yara and yara-json exports. Existing YARA rules will remain intact similar to the state before the current release and will be included together with the native YARA rules stored in MISP. The export depends on the <a href="https://github.com/plyara/plyara">Python plyara module</a>.</p>
<h2 id="api">API</h2>
<ul>
<li>New includeWarninglistHits option interested for the attribute and event search APIs, enabling users to query any subset of they’re misp repositories using the usual search filters to reveal potential false positives or other warnings.</li>
<li>Added new export format (attack) for restSearch, opening up the usual search filters to the <a href="https://attack.mitre.org/">ATT&CK</a> integration. The new export format returns the ATT&CK matrix data as HTML via the API and is therefore directly viewable via the REST client. The export was designed during the <a href="https://www.attack-community.org/">EU ATT&CK community</a> workshop organised at eurocontrol.</li>
</ul>
<h1 id="various-other-changes">Various other changes</h1>
<ul>
<li>New update process included in MISP (to prepare the merge of the “zoidberg” branch and improve the migration process).</li>
<li>Installer updated and improved (MISP now works on OpenBSD 6.5 and Debian 9.9).</li>
<li>Module selection improved (sorted and improved the look and feel).</li>
<li>STIX export fixed for email attachments.</li>
<li>RPZ export improved, including new RPZ policy actions (based on <a href="https://tools.ietf.org/html/draft-vixie-dnsop-dns-rpz-00">IETF draft</a>).</li>
<li>New button to quickly extend a MISP event added in the event view.</li>
<li>Many bugs squashed.</li>
</ul>
<h1 id="security-fixes">Security fixes</h1>
<p>Thanks to João Lucas Melo Brasio from <a href="https://elytronsecurity.com">Elytron Security S.A.</a> who reported the following security vulnerabilities which are now fixed in MISP 2.4.107.</p>
<ul>
<li><a href="https://cve.circl.lu/cve/CVE-2019-11812">CVE-2019-11812</a> A persistent XSS issue was discovered in app/View/Helper/CommandHelper.php in MISP before 2.4.107. JavaScript can be included in the discussion interface, and can be triggered by clicking on the link.</li>
<li><a href="https://cve.circl.lu/cve/CVE-2019-11813">CVE-2019-11813</a> An issue was discovered in app/View/Elements/Events/View/value_field.ctp in MISP before 2.4.107. There is persistent XSS via link type attributes with javascript:// links.</li>
<li><a href="https://cve.circl.lu/cve/CVE-2019-11814">CVE-2019-11814</a> An issue was discovered in app/webroot/js/misp.js in MISP before 2.4.107. There is persistent XSS via image names in titles, as demonstrated by a screenshot.:</li>
</ul>
<h1 id="misp-modules">MISP modules</h1>
<p>Many new <a href="https://github.com/MISP/misp-modules">MISP modules</a> were added such as PDF, PPT, DOCX and XLS importer along with VMRay sandboxes analysis import.</p>
<p>We would like to thank all the contributors, reporters and users who have helped us in the past months to improve MISP and information sharing at large.</p>
<p>As always, a detailed and <a href="http://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2019-05-12T23:00:00+00:00https://www.misp-project.org/2019/04/25/MISP.2.4.106.releasedMISP - MISP 2.4.106 released (aka Too many improvements)2019-04-24T23:00:00+00:00<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.106">2.4.106</a>) has been released with a host of improvements, including new features such as a feed cache search, CLI tools to manage your MISP instance along with improved diagnostics.</p>
<h1 id="new-features">New features</h1>
<ul>
<li>[API] Improved API to update warning-lists, object templates, the galaxy library, taxonomies and notice lists.</li>
<li>Searching the feed caches is now possible via both the UI and the API. This allows users to rapidly find out whether a provided value exists in any of the cached sources (feeds <a href="https://www.misp-project.org/feeds/">feeds</a> and MISP servers alike).</li>
<li>[CLI] Worker management is now exposed via the CLI. The listing, starting, restarting and killing of workers can now be simply accomplished via the CLI.</li>
<li>[CLI] reset/set a user’s API key via the CLI. Overriding a password is now also possible without the need to force a password reset on login.</li>
<li>[Auth] <a href="https://www.linotp.org/">LinOTP</a> authentication module added in MISP.</li>
<li>A <a href="https://github.com/MISP/MISP/blob/2.4/app/Console/Command/TrainingShell.php">training deployment script</a> has been added to support the deployment of configurable networked MISP training topologies. The script has been created in order to support the NATO locked shields 2019 exercise, especially in regards to the deployment of a large number of connected player-team instances.</li>
</ul>
<h1 id="improvements">Improvements</h1>
<ul>
<li>Image resizing of attachments has been improved including a local thumbnail cache.</li>
<li>[UI] Thumbnails are now included in the event graph visualisation.</li>
<li>Exports in all formats are now enabled by default even for non-published events.</li>
<li>Refanging of attributes are now done before saving attributes in the UI (refanging algorithms are the ones from the free-text import).</li>
<li>[UI] Refactor of the tag picker to improve performance and re-introduce the custom tags.</li>
<li>[UI] Performance improvements for events with large numbers of attributes and objects.</li>
<li>[doc] Installation scripts and documentation were significantly improved. <a href="https://misp.github.io/MISP/">MISP Install Documentation </a></li>
<li>[UI/translation] Improvements to the various UI translations including the Russian translation.</li>
<li>Improvement of various MySQL queries for outdated and buggy MySQL versions.</li>
<li>Many new <a href="https://github.com/MISP/misp-objects/">MISP objects template</a> were included. Don’t forget to run a git submodule update and update galaxies, objects and taxonomies via the UI.</li>
<li>Many improvements in the accessibility of MISP user-interface especially for <a href="https://developer.mozilla.org/en-US/docs/Web/Accessibility/ARIA">Accessible Rich Internet Applications (ARIA)</a>.</li>
<li>Many reported bugs were fixed.</li>
</ul>
<h1 id="misp-modules">MISP modules</h1>
<p>Many new <a href="https://github.com/MISP/misp-modules">MISP modules</a> were added such as a QR code extractor, OCR hover module, Cuckoo sandbox submission and Cisco FireSight manager.</p>
<p>We would like to thank all the contributors, reporters and users who have helped us in the past months to improve MISP and information sharing at large.</p>
<p>As always, a detailed and <a href="http://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>2019-04-24T23:00:00+00:00https://www.misp-project.org/2019/03/28/MISP.2.4.105.releasedMISP - MISP 2.4.105 released (aka security fix for CVE-2019-10254)2019-03-27T23:00:00+00:00<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.105">2.4.105</a>) has been released to fix a security vulnerability (<a href="https://cve.circl.lu/cve/CVE-2019-10254">CVE-2019-10254</a>) in addition to some minor improvements and a fix for the STIX 1.1 import, enabling the import of files with additional namespaces (such as <a href="https://www.dhs.gov/cisa/cyber-information-sharing-and-collaboration-program-ciscp">CISCP</a>).</p>
<p>This release includes a security fix for a reflected XSS (<a href="https://cve.circl.lu/cve/CVE-2019-10254">CVE-2019-10254</a>) vulnerability in the default layout template as reported by Tuscany Internet eXchange - Misp Team - TIX CyberSecurity (Thanks to them!). We strongly recommend that everyone update their MISPs to the latest version.</p>
<p>The STIX 1.1 import can now import STIX files using additional, non-standard namespaces (such as <a href="https://www.dhs.gov/cisa/cyber-information-sharing-and-collaboration-program-ciscp">CISCP</a>).</p>
<h1 id="improvements">Improvements</h1>
<ul>
<li>A new diagnostic to display the status of all the git sub-modules.</li>
<li>Replaced the old non-cached export page with improved restSearch.</li>
<li>Multiple improvements in the UI.</li>
<li>Russian translation of the UI added.</li>
<li>STIX 1.1 export fixed to set the adequate TLP marking.</li>
</ul>
<p>We would like to thank all the contributors, reporters and users who have helped us in the past months to improve MISP and information sharing at large.</p>
<p>As always, a detailed and <a href="http://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>
<p>Don’t hesitate to have a look at our <a href="http://www.misp-project.org/events/">events page</a> to see our next trainings, talks and activities to improve threat intelligence, analytics and automati
on.</p>2019-03-27T23:00:00+00:00http://blog.thehive-project.org/?p=4812MISP - A Short Story of Getting Work Done: TheHive 3.3.02019-03-27T22:40:16+00:00Some of our die-hard fans noticed that we silently released TheHive 3.3.0 a few days ago, after six release candidates. Well. Silently won’t be the right word to use in this case as we are drowning under work and feature requests and we sometimes postpone communication in favour of getting true real work done. So, … <a href="https://blog.thehive-project.org/2019/03/27/a-short-story-of-getting-work-done-thehive-3-3-0/" class="more-link">Continue reading <span class="screen-reader-text">A Short Story of Getting Work Done: TheHive 3.3.0</span> <span class="meta-nav">→</span></a>2019-03-27T22:40:16+00:00https://www.misp-project.org/2019/03/26/MISP.2.4.104.releasedMISP - MISP 2.4.104 released (aka too many new features)2019-03-25T23:00:00+00:00<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.104">2.4.104</a>) has been released with a host of new features such as new overlap feed comparator, a new graph visualisation of event and attribute distributions, a history/bookmark system for the REST client and many others.</p>
<h1 id="new-features">New features</h1>
<h2 id="new-overlap-feed-comparator">New overlap feed comparator</h2>
<p>Cached feeds can now be compared to the entire set or a subset of the other cached feeds, assisting users in their decision making process for acquiring new feeds based on being able to cover the contents of the new feed with their combination nof existing ingested feeds.</p>
<p><img src="/assets/images/misp/blog/feed-coverage.png" alt="Comparing a MISP feed to other feeds and check its coverage" /></p>
<h2 id="distribution-graph">Distribution graph</h2>
<p>A new distribution visualisation graph has been introduced to quickly display the potential recipients of the data. This allows users to get an overview of how far events and attributes will be distributed and shows the members of the community who will receive the information shared.</p>
<p><img src="/assets/images/misp/blog/distribution-graph.png" alt="MISP distribution graph example" /></p>
<h2 id="bookmark-and-history-in-rest-client">Bookmark and history in REST client</h2>
<p>The MISP UI REST Client now keeps a history of the 10 most recently performed queries. Additionally, queries can now be recalled and bookmarked for later use, so there’s no longer a need to manually keep track of your queries in your notes,
it’s now in your MISP instance.</p>
<p><img src="/assets/images/misp/blog/rest-bookmarks.png" alt="MISP REST Client bookmarks" /></p>
<h2 id="required-taxonomy">Required taxonomy</h2>
<p>It is now possible to retrict the publication of new events via the UI as long as certain tagging conditions aren’t met. Administrators can configure “required” taxonomies, thereby enforcing their use in the community (such as TLP for CSIRTs, mandatory classification for military organisation or other required contextualisation requirements for ISACs).</p>
<h2 id="kafka-publishing">Kafka publishing</h2>
<p>CERN provided an outstanding contribution which includes a <a href="https://kafka.apache.org/">Kafka</a> streaming functionality for MISP in addition to the existing ZMQ pubsub channel. This allows the inclusion of a real-time stream of actions (such as new events, update, new sighting, new tags) from MISP into advanced processing security workflows. For more information, the <a href="https://indico.cern.ch/event/775579/contributions/3306040/attachments/1808103/2951821/2019-02-20__WLCG_SOC_WG_CERN_SOC_Update.pdf">CERN presentation</a> gives some good insights.</p>
<h2 id="improvements">Improvements</h2>
<ul>
<li>A new ATT&CK heatmap is now displayed per galaxy cluster, aggregating information from the various events and attributes in MISP where the techniques are linked to the given cluster (for example a threat actor).</li>
<li>The matrix-heatmap representation of all matrix type galaxies are now included in the statistic page.</li>
<li>[API] Pagination is now available for the event index.</li>
<li>Galaxies can now be deleted from the user-interface.</li>
<li>A new exercise setup script has been introduced to setup MISP instances for training or exercise:
<ul>
<li>assumes a hub MISP and a set of training MISPs for different participating teams</li>
<li>This script is to be executed on the hub MISP and assuming a consecutively incrementing numeric component in the training MISPs’ URL it will pre-configure them</li>
<li>each instance has to have the same API key for the site admin (the idea is to clone training VMs)</li>
<li>configuration creates users, organisations, sync users, sync connections across both the hub and the individual trainee instances</li>
</ul>
</li>
</ul>
<h2 id="bug-fixes">Bug fixes</h2>
<ul>
<li>Upgraded to the latest version of CakePHP.</li>
<li>Bro/Zeek export fixed including the cached export feature.</li>
<li>The STIX 2 export received various fixes.</li>
<li>Some improvements to the RPZ export format to include serial.</li>
<li>Multiple bugs fixed in the ZMQ.</li>
</ul>
<p>A host of bugs were squashed and various small improvements were implemented.</p>
<p>MISP <a href="/galaxy.pdf">galaxy</a>, <a href="/objects.pdf">objects</a>, <a href="/taxonomies.pdf">taxonomies</a> and <a href="https://www.github.com/MISP/misp-warninglists">warning-lists</a> were extended by many contributors, which are also included by default in MISP. Don’t forget to run a <code class="highlighter-rouge">git submodule update</code> and update galaxies, objects and taxonomies via the UI.</p>
<p>We would like to thank all the contributors, reporters and users who have helped us in the past months to improve MISP and information sharing at large.</p>
<p>As always, a detailed and <a href="http://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>
<p>Don’t hesitate to have a look at our <a href="http://www.misp-project.org/events/">events page</a> to see our next trainings, talks and activities to improve threat intelligence, analytics and automati
on.</p>2019-03-25T23:00:00+00:00https://www.misp-project.org/2019/03/04/MISP.2.4.103.releasedMISP - MISP 2.4.103 released (aka UI improvements)2019-03-03T23:00:00+00:00<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.103">2.4.103</a>) has been released with significant UI improvements (including a new flexible attribute filtering tool at the event level), many bug fixes and a fix to a security vulnerability (CVE-2019-9482) which was affecting sighting visibility.</p>
<h1 id="new-features">New features</h1>
<h2 id="improved-attribute-filtering-tool">Improved attribute filtering tool</h2>
<p>A new attribute filtering tool has been added to the event view to replace the previous filtering. Complex filtering rules can be set to easily filter, navigate and paginate over large events with many attributes and objects.</p>
<p><img src="/assets/images/misp/blog/filtering.png" alt="MISP screenshot - new attribute filtering tool at event level" class="img-responsive" /></p>
<p><img src="/assets/images/misp/blog/filtering2.png" alt="MISP screenshot - new attribute filtering tool at event level" class="img-responsive" /></p>
<h2 id="improved-hover-behavior-for-expansion-services">Improved hover behavior for expansion services.</h2>
<p>Thanks to <a href="https://github.com/wesleya">Wesley Agena</a> from DomainTools for the improvement in the hover placement while using <a href="https://github.com/MISP/misp-modules">misp-modules</a> expansion services in MISP. The hover improvements include:</p>
<ul>
<li>add some logic to choose a better hover placement</li>
<li>make hover hide on outside click, to allow using the scrollbar to view
full hover</li>
<li>add an icon in the hover tooltip to turn it into a popup</li>
<li>move popup close button to better position</li>
<li>group attributes for each module in hover UI</li>
<li>prevent duplicate enrichment API queries once the first one is done</li>
</ul>
<h1 id="ui-rework">UI rework</h1>
<p>A major project is ongoing to improve the UI accessibility in MISP, UI elements are progressively updated to an adequate templating system to ease the future extension of the UI. This versions already includes a reworked UI for tab UI, index UI, server settings, server preview and much more. The rework is handled in a progressive fashion with the UI being gradually updated to ensure a smooth transition. If you notice any UI specific issues during the transition period, don’t hesitate to open an <a href="https://github.com/MISP/MISP/issues">issue</a> (with a screenshot if possible) to describe the expected behavior.</p>
<h2 id="generic-matrix-like-galaxies-are-now-supported">Generic matrix-like galaxies are now supported</h2>
<p>With the increased use of MITRE ATT&CK and the need of describing similar matrix-like models, generic matrix-like galaxies are now supported.
You can create your own matrix with the associated custom kill chains. A first <a href="https://www.misp-project.org/galaxy.html#_election_guidelines">new matrix-like galaxy</a> has been added to MISP called <em>Universal Development and Security Guidelines as Applicable to Election Technology</em> made by the <a href="https://www.ria.ee/sites/default/files/content-editors/kuberturve/cyber_security_of_election_technology.pdf">European Commission</a> to model the attack model against election processes and technologies.</p>
<p>If you want to create your own matrix-like, <a href="https://www.misp-project.org/misp-training/3.2-misp-galaxy.pdf">a slide deck called MISP Galaxy</a> part of the <a href="https://github.com/MISP/misp-training#misp-training-materials">MISP training materials</a> explains the basics.</p>
<h1 id="security-fix-cve-2019-9482">Security fix (CVE-2019-9482)</h1>
<p>In MISP 2.4.102, an authenticated user could view sightings that they should not be eligible for. Exploiting this requires access to the event that has received the sighting in addition to certain conditions aligning - the issue affects instances with restrictive sighting settings (event only / sighting reported only). This vulnerability got has received the designation <a href="https://cve.circl.lu/cve/CVE-2019-9482">CVE-2019-9482</a>. Thanks to Tyler McLellan of CanCyber.org for reporting the vulnerability. We are eager to receive security reports and/or analyses about the MISP project, <a href="https://github.com/MISP/MISP/blob/2.4/CONTRIBUTING.md#reporting-security-vulnerabilities">don’t hesitate to contact us</a>.</p>
<h2 id="enhancements">Enhancements</h2>
<ul>
<li>Kerberos authentication has been updated to include ldapEmailField to specify additional location of where email addresses can be found (thanks to <a href="https://github.com/iwitz">iwitz</a>)</li>
<li>[API] change_pw is now exposed to the API.</li>
<li>The event view now includes the number of objects included in an event.</li>
<li>Additional url setting to add a complementary baseurl especially when a MISP is accessible via different means and an url is required for the sharing groups. The objective is to decouple the baseurl (used to prepend links) from the announce baseurl (for sharing groups / emailing).</li>
<li>Add CORS setting for external integration (thanks to <a href="https://github.com/FloatingGhost">Hannah Ward</a>).</li>
<li>A major rework on the <a href="https://misp.github.io/MISP/INSTALL.ubuntu1804/">auto installer script for MISP</a> to transform the installation process into a pleasant journey.</li>
<li>[CLI] DB updates can now be executed via the CLI. This mimics what he is done what the automatic update does when login for the first time after an update.</li>
<li>[API] New tag search API to search for tags.
<ul>
<li>simply pass the value you want to search for. Use % for wildcards</li>
<li>taxonomy and galaxy metadata returned with tag</li>
</ul>
</li>
<li>[API] The log search API now supports time ranges.</li>
<li>Event view now includes a sparkline to track changes on the event over time.</li>
<li>Many docs and installer guides have been improved.</li>
</ul>
<p>A host of bugs were squashed and various small improvements were implemented.</p>
<p>MISP <a href="/galaxy.pdf">galaxy</a>, <a href="/objects.pdf">objects</a> and <a href="/taxonomies.pdf">taxonomies</a> were extended by many contributors, which are also included by default in MISP. Don’t forget to run a <code class="highlighter-rouge">git submodule update</code> and update galaxies, objects and taxonomies via the UI.</p>
<p><a href="https://github.com/MISP/misp-modules">MISP modules</a> were also significantly improved especially on the PDF export which includes a complete export of MISP events as a clean and concise PDF report.</p>
<p>We would like to thank all the contributors, reporters and users who have helped us in the past months to improve MISP and information sharing at large.</p>
<p>As always, a detailed and <a href="http://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>
<p>Don’t hesitate to have a look at our <a href="http://www.misp-project.org/events/">events page</a> to see our next trainings, talks and activities to improve threat intelligence, analytics and automation.</p>2019-03-03T23:00:00+00:00http://blog.thehive-project.org/?p=4750MISP - Here comes the Sun (and TheHive 3.3-RC5)2019-02-26T05:55:40+00:00On February 10, 2019, we released TheHive 3.3-RC2. It contained new features such as bulk alert merging, alert sorting, observable tag autocompletion, exporting case tags to MISP & more. Since then your favourite French code Chefs have been beesy refining TheHive 3.3 through new release candidates while getting Cortex 3 ready for prime time. Over … <a href="https://blog.thehive-project.org/2019/02/26/here-comes-the-sun-and-thehive-3-3-rc5/" class="more-link">Continue reading <span class="screen-reader-text">Here comes the Sun (and TheHive 3.3-RC5)</span> <span class="meta-nav">→</span></a>2019-02-26T05:55:40+00:00http://blog.thehive-project.org/?p=4688MISP - TheHive 3.3-RC2, Hot out of the Oven2019-02-10T20:33:13+00:00TheHive Project’s code Chefs, dressed in their outright haute cuisine outfit, including the traditional toque blanche, have been quite busy lately, working on dockerizing all the Cortex analyzers (more on this later in an upcoming post), and doing tedious work to prepare the replacement of Elasticsearch by a GraphDB which will help us finally release … <a href="https://blog.thehive-project.org/2019/02/10/thehive-3-3-rc2-hot-out-of-the-oven/" class="more-link">Continue reading <span class="screen-reader-text">TheHive 3.3-RC2, Hot out of the Oven</span> <span class="meta-nav">→</span></a>2019-02-10T20:33:13+00:00http://blog.thehive-project.org/?p=4692MISP - UnshortenLink, SSRF and Cortex-Analyzers 1.15.22019-02-11T09:57:09+00:00We urge our fellow fighters of cybercrime and funny and not-so-funny animals-in-disguise, to update their Cortex analyzers to the latest 1.15.2 version which plugs a serious vulnerability in the Unshortenlink analyzer and fixes several bugs. Unshortenlink Vulnerability On Jan 24, Alexandre Basquin discovered a SSRF vulnerability in the Unshortenlink 1.0 analyzer. By exploiting it, an … <a href="https://blog.thehive-project.org/2019/02/11/unshortenlink-ssrf-and-cortex-analyzers-1-15-2/" class="more-link">Continue reading <span class="screen-reader-text">UnshortenLink, SSRF and Cortex-Analyzers 1.15.2</span> <span class="meta-nav">→</span></a>2019-02-11T09:57:09+00:00https://www.misp-project.org/2019/02/02/MISP.2.4.102.releasedMISP - MISP 2.4.102 released (aka bug fixes and FOSDEM release)2019-02-01T23:00:00+00:00<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.102">2.4.102</a>) has been released with several fixes, various UI improvements, new types and a praise to the open source community.</p>
<h2 id="new-types">New types</h2>
<h3 id="anonymisation">Anonymisation</h3>
<p>Sharing and exchanging information encompasses a lot of different models, communities or practices, with the MISP project being involved in various discussions and projects centered around building sharing and information exchange communities. A complex topic comes up regularly, namely the anonymisation of the information exchanged. Sharing anonymised information often aims to simply share the existence of knowledge about information. We introduced a new attribute type in MISP called “anonymised”, which can be combined with a newly introduced object called <a href="https://www.misp-project.org/objects.html#_anonymisation">anonymisation</a>.</p>
<p><img src="/assets/images/misp/blog/anon-graph.png" alt="" class="img-responsive" />
<img src="/assets/images/misp/blog/anon2.png" alt="" class="img-responsive" />
<img src="/assets/images/misp/blog/anonymisation.png" alt="" class="img-responsive" /></p>
<p>The design is flexible and can be extended with new anonymisation techniques and/or approaches. We are standing on the shoulders of giants, for example open source tools such as <a href="https://www.cc.gatech.edu/computing/Networking/projects/cryptopan/">Crypto-PAn</a>, <a href="https://github.com/kohler/ipsumdump">ipsumpdump</a> or <a href="https://arx.deidentifier.org/">arx</a>.</p>
<h3 id="bro---zeek">Bro -> Zeek</h3>
<p>The open source NIDS <a href="https://blog.zeek.org/2018/10/renaming-bro-project_11.html">Bro project was renamed Zeek</a> in late 2018. Bro has a growing community and NIDSs are important in ensuring the detection and enforcement of threat intelligence information shared within various communities at the network level. We added a new MISP type called zeek which can be used in exactly the same fashion as the bro type (which will remain in place to ensure backwards compatibility). As diversity is of utmost importance when it comes to information security and also to open source NIDS options, the MISP standard core format supports <a href="https://suricata-ids.org/">Suricata</a>, <a href="https://www.snort.org/">Snort</a> and <a href="https://www.zeek.org/">Zeek</a>.</p>
<h2 id="sighting">Sighting</h2>
<p><img src="/assets/images/misp/blog/sighting-UI.png" alt="" class="img-responsive" /></p>
<ul>
<li>MISP UI has been improved to allow sighting at the attribute level or at the global level.</li>
<li>Various improvements to the sighting hover such as a generic hovering support.</li>
<li>ReST API for sighting improved.</li>
<li>ReST API bug fixes where sightings were added to every single attributes when addSighting failed.</li>
<li>Search results now include sighting results too.</li>
</ul>
<h2 id="enhancements">Enhancements</h2>
<ul>
<li>Server settings have been refactored and streamlined with the UI server settings.</li>
<li><a href="https://misp.github.io/MISP/">Installation documentation</a> has been improved with a generic Debian installer script.</li>
<li>restSearch APIs improved in regards to better support for URL parameters.</li>
<li>Feed correlation is no longer visible when attributes have correlation disabled.</li>
<li>Translations of the UI were improved and new languages were added (Updated: Czech 4%, Danish 53%, German 21%, French 95%, Italian 39%, Japanese 95%, Korean 3%, Brazilian Portuguese 6%, Spanish 3% new: [i18n] Hungarian, Russian, Ukrainian, Simplified Chinese.)</li>
<li>STIX 1 and 2 exports are now using the restSearch API instead of the old download interface.</li>
<li>Major improvements in the handling of malware samples in STIX 1 and 2 format.</li>
</ul>
<p>Many bugs were fixed and various small improvements were performed. A significant fix to improve performance for older versions of MySQL were implemented to avoid incorrect indexes being preferred for some specific queries.</p>
<p>MISP <a href="/galaxy.pdf">galaxy</a>, <a href="/objects.pdf">objects</a> and <a href="/taxonomies.pdf">taxonomies</a> were extended by many contributors. These are also included by default in MISP. Don’t forget to do a <code class="highlighter-rouge">git submodule update</code> and update galaxies, objects and taxonomies via the UI.</p>
<p>We would like to thank all the contributors, reporters and users who have helped us in the past months to improve MISP and information sharing at large. As this is the FOSDEM release, we would like to praise all the open source software and their respective authors who have helped us to make the MISP project a reality, including (in no particular order and this is in no ways meant to be exhaustive) <a href="https://redis.io/">Redis</a>, <a href="http://php.net/">PHP</a>, <a href="https://www.python.org/">Python</a>, <a href="https://thehive-project.org/">TheHive Project</a>, <a href="https://lief.quarkslab.com/">LIEF - Library to Instrument Executable Formats</a>, <a href="https://mariadb.org/">MariaDB</a>, <a href="http://visjs.org/index.html">vis.js</a>, <a href="http://zeromq.org/">ZMQ</a> …</p>
<p>As always, a detailed and <a href="http://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>
<p>Don’t hesitate to have a look at our <a href="http://www.misp-project.org/events/">events page</a> to see our next trainings, talks and activities to improve threat intelligence, analytics and automation.</p>2019-02-01T23:00:00+00:00http://blog.thehive-project.org/?p=4118MISP - Cerana 0.4: Hotfix & Way Beyond2018-02-06T12:46:53+00:00Update: Cerana 0.5 (TheHive 3.0.5) was released on Feb 8, 2018 to fix a regression introduced by Cerana 0.4, pertaining to the observable mini-reports. Please install 3.0.5 instead. Waiting for the menu, one of the numerous guests of TheHive Project’s world-renowned code restaurant grows impatient. He stands up and walks toward the kitchen, looking for … <a href="https://blog.thehive-project.org/2018/02/06/cerana-0-4-hotfix-way-beyond/" class="more-link">Continue reading <span class="screen-reader-text">Cerana 0.4: Hotfix & Way Beyond</span> <span class="meta-nav">→</span></a>2018-02-06T12:46:53+00:00http://blog.thehive-project.org/?p=4142MISP - Cortex 2.0.3 Released and Analyzer Updates2018-04-09T16:18:23+00:00There’s a new version of your ultimate observable analysis engine in town : Cortex 2.0.3 is out! Cortex 2.0.3 contains a few important enhancements over its predecessor and fixes a number bugs as described in the full changelog summarised below. So get it while it’s still hot out of the digital oven and let us … <a href="https://blog.thehive-project.org/2018/04/09/cortex-2-0-3-released-and-analyzer-updates/" class="more-link">Continue reading <span class="screen-reader-text">Cortex 2.0.3 Released and Analyzer Updates</span> <span class="meta-nav">→</span></a>2018-04-09T16:18:23+00:00http://blog.thehive-project.org/?p=4149MISP - TheHive 3.0.10 Released2018-05-29T13:36:10+00:00Rejoice DFIR fighters! Your favorite Security Incident Response Platform has just gotten better. TheHive 3.0.10 (codename Cerana 0.10) is just out of the oven. Thomas and Nabil, as the true code Chefs they are, have fixed a number of issues and added a few enhancements in this release. Read on, update and defend your constituency! … <a href="https://blog.thehive-project.org/2018/05/29/thehive-3-0-10-released/" class="more-link">Continue reading <span class="screen-reader-text">TheHive 3.0.10 Released</span> <span class="meta-nav">→</span></a>2018-05-29T13:36:10+00:00http://blog.thehive-project.org/?p=4184MISP - Cortex4py 2 is Out!2018-06-18T19:16:24+00:00Cortex, a free, open source software allows security analysts and threat hunters to analyze and enrich observables (IP addresses, hashes, domains, …) collected in the course of an investigation or received from third parties, for example through MISP, the de facto standard for threat sharing. On March 29, 2018, we released Cortex 2, a major improvement over the … <a href="https://blog.thehive-project.org/2018/06/18/cortex4py-2-is-out/" class="more-link">Continue reading <span class="screen-reader-text">Cortex4py 2 is Out!</span> <span class="meta-nav">→</span></a>2018-06-18T19:16:24+00:00http://blog.thehive-project.org/?p=4205MISP - Keep Them Coming: Hashdd, URLhaus & a Revamped FileInfo analyzer2018-07-13T07:27:38+00:00We are happy to announce the immediate availability of a new major version of Cortex-Analyzers. Version 1.11.0 includes two brand new analyzers, several updates and a few bug fixes: Hashdd, contributed by iosonogio URLhaus, contributed by ninoseki The Domaintools analyzer has been updated with two new flavors: Risk and Reputation The VirusTotal analyzer can (finally!) get reports … <a href="https://blog.thehive-project.org/2018/07/13/keep-them-coming-hashdd-urlhaus-a-revamped-fileinfo-analyzer/" class="more-link">Continue reading <span class="screen-reader-text">Keep Them Coming: Hashdd, URLhaus & a Revamped FileInfo analyzer</span> <span class="meta-nav">→</span></a>2018-07-13T07:27:38+00:00http://blog.thehive-project.org/?p=4250MISP - How to Cruise Ocean Threat Without Sinking Using TheHive 3.1 & Cortex 2.12018-07-31T15:52:23+00:00Paris, France. The Sun is shining on the city of lights and temperatures are quite high, even for the summer season. Life is good. As a matter of fact, life is excellent. TheHive Master Cooks are about to go on vacation for a few weeks. But before they pack up their Patagonia bags and leave … <a href="https://blog.thehive-project.org/2018/07/31/how-to-cruise-ocean-threat-without-sinking-using-thehive-3-1-cortex-2-1/" class="more-link">Continue reading <span class="screen-reader-text">How to Cruise Ocean Threat Without Sinking Using TheHive 3.1 & Cortex 2.1</span> <span class="meta-nav">→</span></a>2018-07-31T15:52:23+00:00http://blog.thehive-project.org/?p=4260MISP - Hold your breath and git pull2018-09-18T15:49:11+00:00Cortex-Analyzer 1.13.0 is out and includes new analyzers, some improvements and few bug fixes : Hunter.io has been contributed by Rémi Allain (@remiallain) DShield lookup contributed by Xavier Martens (@xme) Pulsedive contributed by Nils Kuhnert (@3c7, TheHive Project) FileInfo has been enhanced with Manalyze submodule for PE analysis ; by @lctrcl and Nils Kuhnert (@3c7) Thanks to @silrumpa, the Fortiguard_URLCategory analyzer has been updated and let you … <a href="https://blog.thehive-project.org/2018/09/18/hold-your-breath-and-git-pull/" class="more-link">Continue reading <span class="screen-reader-text">Hold your breath and git pull</span> <span class="meta-nav">→</span></a>2018-09-18T15:49:11+00:00http://blog.thehive-project.org/?p=4289MISP - Cortex 2.1.0: The Response Edition2018-09-27T06:29:24+00:00We released Cortex 2.1.0 as a release candidate back in July 31, 2018 along with TheHive 3.1.0-RC1. By then, the power duo which makes digital forensics, incident response and, to an extent, cyber threat intelligence, better, faster, happier, regular exercising gained the ability to perform active response. We ate our own dog food for a couple … <a href="https://blog.thehive-project.org/2018/09/27/cortex-2-1-0-the-response-edition/" class="more-link">Continue reading <span class="screen-reader-text">Cortex 2.1.0: The Response Edition</span> <span class="meta-nav">→</span></a>2018-09-27T06:29:24+00:00http://blog.thehive-project.org/?p=4300MISP - Cortex 101: Dissecting Observables a Hundred Ways2018-10-26T12:15:08+00:00TheHive Project’s Code Chefs are glad to announce that, thanks to the precious contributions of the user community, Cortex has broken the one hundred analyzer mark. Cortex-Analyzers version 1.14.0 is out and includes new analyzers, some improvements and some bug fixes. New Analyzers New and enhanced analyzers, described below, are: Cisco Investigate by Cisco Umbrella … <a href="https://blog.thehive-project.org/2018/10/26/cortex-101-dissecting-observables-a-hundred-ways/" class="more-link">Continue reading <span class="screen-reader-text">Cortex 101: Dissecting Observables a Hundred Ways</span> <span class="meta-nav">→</span></a>2018-10-26T12:15:08+00:00http://blog.thehive-project.org/?p=4335MISP - TheHive 3.2.0-RC1: The MISP Love Edition2018-11-16T17:02:03+00:00Guess what? Our integration with MISP, the de facto standard for threat sharing, has just gotten better with our latest beta release: TheHive 3.2.0-RC1. While you could synchronize TheHive with one or multiple MISP instances in earlier versions and select events using filters like their age, the number of attributes they contain or exclude those … <a href="https://blog.thehive-project.org/2018/11/16/thehive-3-2-0-rc1-the-misp-love-edition/" class="more-link">Continue reading <span class="screen-reader-text">TheHive 3.2.0-RC1: The MISP Love Edition</span> <span class="meta-nav">→</span></a>2018-11-16T17:02:03+00:00https://www.misp-project.org/2019/01/20/MISP.2.4.101.releasedMISP - MISP 2.4.101 released (aka 3 features for free)2019-01-19T23:00:00+00:00<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.101">2.4.101</a>) has been released with 3 main new features (tag collections, improved tag/galaxy selector and MISP instance caching), along with a host of improvements and bug fixes.</p>
<h2 id="tag-collections">Tag collections</h2>
<p><img src="/assets/images/misp/blog/tag-collection-creation.png" alt="" class="img-responsive" /></p>
<p>Contextualisation in threat intelligence is one of the key activities when performing analysis and when reviewing or processing information from internal or external sources. The task can be rather tedious, but nevertheless, it’s a critical step in ensuring the quality and the information’s capacity to be used for automatic processing. MISP 2.4.101 introduces a new concept, in an attempt to improve the “time-to-contextualise” information for users using the platform. Tag collections, a new feature in 2.4.101, aim to allow users to predefine re-usable structures consisting of a set of tags (from taxonomies) along with galaxy information attached. Analysts can use these named collections to quickly classify information with all of the contextualisation labels declared in the collection. This functionality enables anyone using MISP to significantly lower the time it takes to classify information and to ensure that all the pre-defined context related information is attached to an event or attribute. This feature is a first step in opening up the sharing of analysisMISP best practices directly via the platform itself.</p>
<h2 id="improved-taggalaxy-selector">Improved tag/galaxy selector</h2>
<p><img src="/assets/images/misp/blog/tag-collection.png" alt="" class="img-responsive" /></p>
<p>The success of MISP taxonomies and galaxies since their inception has been suffering from a minor but annoying drawback. When we originally designed the user-interfaces of the tag and galaxy systems in MISP, our immediate intent was to handle a rather small set of taxonomies. Since then we have come a long way and thanks to the many excellent contributions we’ve received from the community, the ugly side-effect of our original design decisions reared its head: adding multiple tags and galaxies has become a tedious chore, especially when trying to contextualise several aspects of the information to be shared, using multiple tags and galaxies.</p>
<p>In order to solve this issue, a complete new selector-system has been added to ease the process of adding multiple tags and galaxies. The design was based on various issues and the feedback we have received from private organisations, CSIRTs and analysts. Let us know what you think about it and don’t hesitate to <a href="https://github.com/MISP/MISP/issues">open an issue for bugs or feedback on the improved selector</a>.</p>
<h2 id="misp-instance-caching">MISP instance caching</h2>
<p>Synchronisation between MISP instances has always been a core functionality of MISP in order to support the sharing of information. This release includes a new feature, allowing administrators to perform MISP remote instance caching without the need to synchronise and pull events. The MISP instance caching feature supports the built-in correlation system of MISP along with the overlap matrix of the feed system. This allows users to see cross-instsance correlations without the need to ingest the data of other instances directly and to include remote instances in the feed correlation system to compare how the information of feeds stacks up to that contained on other instances. This also opens up a host of possible multi-MISP scenarios when it comes to running collection-oriented “junk” MISPs internally and being able to cross correlate them with the operational instances. Keep in mind, in order to benefit from this system, the instance to be cached also has to be on at least version 2.4.101.</p>
<h2 id="new-attribute-type">New attribute type</h2>
<p>“<a href="https://github.com/salesforce/hassh">HASSH</a>” is a network fingerprinting standard which can be used to identify specific Client and Server SSH implementations. The fingerprints can be easily stored, searched and shared in the form of an MD5 fingerprint.</p>
<p>hassh-md5 and hasshserver-md5 types are now part of <a href="https://tools.ietf.org/html/draft-dulaunoy-misp-core-format-06">MISP standard core format which has been updated</a>. If you see a missing types or object template in MISP, don’t hesitate to report it back to us.</p>
<h2 id="many-improvements">Many improvements</h2>
<ul>
<li>A new unpublish action has been added to simplify the process in the user-interface.</li>
<li>Disable correlation is now accessible when creating/modifying an attribute.</li>
<li>New default feed added (from <a href="https://mirai.security.gives">mirai.security.gives</a>).</li>
<li>Many improvements in the STIX2 import and export.</li>
<li>Various bugs fixed.</li>
</ul>
<p>We would like to thank all the contributors, reporters and users who helped us in the past months to improve MISP and information sharing at large.</p>
<p>MISP <a href="/galaxy.pdf">galaxy</a>, <a href="/objects.pdf">objects</a> and <a href="/taxonomies.pdf">taxonomies</a> were extended by many contributors. These are also included by default in MISP. Don’t forget to do a <code class="highlighter-rouge">git submodule update</code> and update galaxies, objects and taxonomies via the UI.</p>
<p>A detailed and <a href="http://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>
<p>Don’t hesitate to have a look at our <a href="http://www.misp-project.org/events/">events page</a> to see our next trainings, talks and activities to improve threat intelligence, analytics and automation.</p>2019-01-19T23:00:00+00:00https://blog.rootshell.be/?p=30204MISP - Running MISP in a Docker Container2016-03-03T20:11:06+00:00<p>MISP (“Malware Information Sharing Platform“) is a free software which was initially created by the Belgian Defence to exchange IOC’s with partners like the NCIRC (NATO). Today it became an independent project and is mainly developed by a group of motivated people. MISP is mainly used by CERT’s (“Computer Emergency Response</p>
<p><b>[The post <a rel="nofollow" href="https://blog.rootshell.be/2016/03/03/running-misp-in-a-docker-container/">Running MISP in a Docker Container</a> has been first published on <a rel="nofollow" href="https://blog.rootshell.be">/dev/random</a>]</b></p>2016-03-03T20:11:06+00:00https://blog.rootshell.be/?p=31569MISP - Quick Integration of MISP and Cuckoo2017-01-25T21:27:04+00:00<p>With the number of attacks that we are facing today, defenders are looking for more and more IOC’s (“Indicator of Compromise) to feed their security solutions (firewalls, IDS, …). It becomes impossible to manage all those IOC’s manually and automation is the key. There are two main problems with this</p>
<p><b>[The post <a rel="nofollow" href="https://blog.rootshell.be/2017/01/25/quick-integration-misp-cuckoo/">Quick Integration of MISP and Cuckoo</a> has been first published on <a rel="nofollow" href="https://blog.rootshell.be">/dev/random</a>]</b></p>2017-01-25T21:27:04+00:00https://blog.rootshell.be/?p=31587MISP - [SANS ISC Diary] IOC’s: Risks of False Positive Alerts Flood Ahead2017-01-26T12:45:12+00:00<p>I published the following diary on isc.sans.org: “IOC’s: Risks of False Positive Alerts Flood Ahead“. Yesterday, I wrote a blog post which explained how to interconnect a Cuckoo sandbox and the MISP sharing platform. MISP has a nice REST API that allows you to extract useful IOC’s in different formats.</p>
<p><b>[The post <a rel="nofollow" href="https://blog.rootshell.be/2017/01/26/sans-isc-diary-iocs-risks-false-positive-alerts-flood-ahead/">[SANS ISC Diary] IOC’s: Risks of False Positive Alerts Flood Ahead</a> has been first published on <a rel="nofollow" href="https://blog.rootshell.be">/dev/random</a>]</b></p>2017-01-26T12:45:12+00:00https://blog.rootshell.be/?p=32029MISP - Splunk Custom Search Command: Searching for MISP IOC’s2017-10-31T12:23:01+00:00<p>While you use a tool every day, you get more and more knowledge about it but you also have plenty of ideas to improve it. I’m using Splunk on a daily basis within many customers’ environments as well as for personal purposes. When you have a big database of events,</p>
<p><b>[The post <a rel="nofollow" href="https://blog.rootshell.be/2017/10/31/splunk-custom-search-command-searching-misp-iocs/">Splunk Custom Search Command: Searching for MISP IOC’s</a> has been first published on <a rel="nofollow" href="https://blog.rootshell.be">/dev/random</a>]</b></p>2017-10-31T12:23:01+00:00https://blog.rootshell.be/?p=32240MISP - [SANS ISC] Automatic Hunting for Malicious Files Crossing your Network2018-03-22T11:42:31+00:00<p>I published the following diary on isc.sans.org: “Automatic Hunting for Malicious Files Crossing your Network“: If classic security controls remain mandatory (antivirus, IDS, etc), it is always useful to increase your capacity to detect suspicious activities occurring in your networks. Here is a quick recipe that I’m using to detect</p>
<p><b>[The post <a rel="nofollow" href="https://blog.rootshell.be/2018/03/22/sans-isc-automatic-hunting-malicious-files-crossing-network/">[SANS ISC] Automatic Hunting for Malicious Files Crossing your Network</a> has been first published on <a rel="nofollow" href="https://blog.rootshell.be">/dev/random</a>]</b></p>2018-03-22T11:42:31+00:00https://blog.rootshell.be/?p=32276MISP - [SANS ISC] The real value of an IOC?2018-04-24T12:07:49+00:00<p>I published the following diary on isc.sans.org: “The real value of an IOC?“: When a new malware sample is analysed by a security researcher, details are usually posted online with details of the behaviour and, based on this, a list of IOCs or “Indicators of Compromise” is published. Those indicators</p>
<p><b>[The post <a rel="nofollow" href="https://blog.rootshell.be/2018/04/24/sans-isc-real-value-ioc/">[SANS ISC] The real value of an IOC?</a> has been first published on <a rel="nofollow" href="https://blog.rootshell.be">/dev/random</a>]</b></p>2018-04-24T12:07:49+00:00https://blog.rootshell.be/?p=32536MISP - [SANS ISC] Querying DShield from Cortex2018-11-20T13:41:51+00:00<p>I published the following diary on isc.sans.edu: “Querying DShield from Cortex”: Cortex is a tool part of the TheHive project. As stated on the website, it is a “Powerful Observable Analysis Engine”. Cortex can analyze observables like IP addresses, emails, hashes, filenames against a huge (and growing) list of online services.</p>
<p><b>[The post <a rel="nofollow" href="https://blog.rootshell.be/2018/11/20/sans-isc-querying-dshield-from-cortex/">[SANS ISC] Querying DShield from Cortex</a> has been first published on <a rel="nofollow" href="https://blog.rootshell.be">/dev/random</a>]</b></p>2018-11-20T13:41:51+00:00https://www.misp-project.org/2018/05/16/MISP.2.4.91.releasedMISP - MISP 2.4.91 released (aka distribution visualisation, galaxy at attribute level and privacy notice list)2018-05-15T23:00:00+00:00<p>A new version of MISP <a href="https://github.com/MISP/MISP/tree/v2.4.91">2.4.91</a> has been released including new major features, improvements and bug fixes.</p>
<h3 id="distribution-and-sharing-visualisation">Distribution and sharing visualisation</h3>
<p>MISP 2.4.91 has a new visual aid in order to simply view the distribution and sharing model of all the attributes within an event. As events can
become quite larger, with long lists of objects and attributes, analysts need to verify whether the proper distributions are applied. The new visualisation
allows them to view the items per distribution level including the associated sharing groups. The visualisation is dynamic and can be used to
filter the given attributes matching a specific distribution setting within the event.</p>
<p><img src="/assets/images/misp/blog/sharing.png" alt="Visualisation of a MISP event and how the sharing of attributes will take place" class="img-responsive" /></p>
<h3 id="galaxy-at-attribute-level">Galaxy at attribute level</h3>
<p><a href="/galaxy.html">MISP Galaxy</a> includes a large number of libraries to assist in classifying events based on threat actors, kill chains or actor techniques such as described in the <a href="https://attack.mitre.org/wiki/Main_Page">MITRE ATT&CK</a> galaxy. Initially, MISP galaxies were limited to be attached to MISP events alone. As many users developed new galaxy cluster to map their own model, MISP 2.4.91 is now capable of attaching MISP clusters at the attribute level. In the example below, a vulnerability attribute can be then easily linked to the respective MITRE ATT&CK adversary technique supporting analysts trying to search for and pivot on techniques, but also supporting various more advanced automation scenarios.</p>
<p><img src="/assets/images/misp/blog/exploitation.png" alt="An example of a MISP galaxy such as MITRE ATT&CK attached to a specific attribute in MISP" class="img-responsive" /></p>
<h3 id="privacy-notice-list-and-gdpr">Privacy notice list and GDPR</h3>
<p>The MISP Project is actively involved when it comes to questions of compliance, as of lately with a special focus on <a href="/compliance">information sharing and legal compliance</a>. In the scope of the CEF-TC-2016-3 - Cyber Security co-funding helped us to improve the various aspects of compliance while keeping a strong focus on the information sharing aspect.</p>
<p>In MISP 2.4.91, we introduced the <a href="https://github.com/MISP/misp-noticelist">MISP notice system</a> to inform MISP users of the legal, privacy, policy or even technical implications of using specific attributes, categories or objects. The feature was originally designed to support the Directive 95/46/EC (General Data Protection Regulation - GDPR) by notifying the analyst about the potential risks while entering specific information. The notice feature is a flexible solution to allow for a wide variety of notice systems (expressed in a simple JSON format) to be included in MISP, based on the category or type entered in the system.</p>
<p>We expect to see organisations using MISP to enable, disable or extend the notice lists to fit their specific policies, legal frameworks or local regulation frameworks.</p>
<p><img src="/assets/images/misp/blog/not1.png" alt="GDPR notice about a specific category" class="img-responsive" /></p>
<p>and notice lists are easily configurable:</p>
<p><img src="/assets/images/misp/blog/not2.png" alt="Notice lists are configurable" class="img-responsive" /></p>
<h3 id="api">API</h3>
<p><a href="/feeds">Feed</a> management, in 2.4.91, can be also be done via the API such as add/edit/delete feeds. API documentation is directly accessible via the API if a GET request is performed instead of a POST.</p>
<p>ZMQ feed has been extended to include base64 encoded attachments in order to improve the integration with the CSP platform (MeliCERTes) and other application relying on the ZMQ feed (3169 fixed).</p>
<h3 id="miscellaneous-improvements">Miscellaneous Improvements</h3>
<p>Event enrichment (via misp-modules) can now be easily triggered from the event menu to automatically enrich all the attributes in event. This enrichment is also globally accessible via the API and exposed via the command-line too.</p>
<p>The legacy STIX 1 import has been improved to support CustomObjects, socket address objects, CIQ targets, DNS records object and many others.</p>
<p>Many bugs were fixed with special note to issues 3245, 3240, 3202 and 3201.</p>
<p>MISP 2.4.91 has been updated to the latest version of CakePHP 2.10 series.</p>
<p>The full change log is available <a href="https://www.misp.software/Changelog.txt">here</a>. <a href="https://www.misp.software/PyMISP-Changelog.txt">PyMISP change log</a> is also available.</p>
<p>PyMISP has been also updated, boasting a more clever approach to timestamp handling while updating MISP JSON files. The PyMISP documentation has been updated <a href="https://media.readthedocs.org/pdf/pymisp/latest/pymisp.pdf">PDF</a>.</p>
<p>MISP <a href="/galaxy.pdf">galaxy</a>, <a href="/objects.pdf">objects</a> and <a href="/taxonomies.pdf">taxonomies</a> were notably extended by many contributors. These are also included by default in MISP. Don’t forget to do a <code class="highlighter-rouge">git submodule update</code> and update galaxies, objects and taxonomies via the UI. To get the MISP notice list, don’t forget to perform a <code class="highlighter-rouge">git submodule init; git submodule update</code> to initialise the new external dependency.</p>
<p>Don’t forget that the MISP Threat Intelligence Summit 0x4 will take place the Monday 15th October 2018 before hack.lu 2018. A <a href="https://cfp.hack.lu/misp0x4/">Call-for-Papers is open</a> for the MISP Threat Intelligence Summit 0x4. We would be glad to see users, contributors or organisations actively using MISP or/and threat intelligence to share their experiences and presentation to the CfP.</p>2018-05-15T23:00:00+00:00https://www.misp-project.org/2018/06/07/MISP.2.4.92.releasedMISP - MISP 2.4.92 released (aka performance improvement)2018-06-06T23:00:00+00:00<p>A new version of MISP <a href="https://github.com/MISP/MISP/tree/v2.4.92">2.4.92</a> has been released including aggressive performance boosts, various improvements and bug fixes.</p>
<p>We received feedback from various users about the negative impact on performance when the <a href="http://www.github.com/MISP/misp-warninglists/">MISP warning-lists</a> are enabled (a feature allowing the detection and filtering of false positive attributes in MISP). The performance hit incurred by enabling warning-lists has been reduced to such an extend that enabling them will barely have any impact on performance when viewing or browsing events. We hope this performance gain will increase the overall adoption of the warning-lists.</p>
<p>A benchmarking tool has been added to the AppModel allowing us to easily spot performance issues across the application. Aggregate execution time, number of iterations and peaked memory usage can be easily spotted in order to facilitate rapid and accurate profiling of the performance across the various functionalities of MISP.</p>
<p>The API has been improved to allow objects to be added by template UUID and version in addition to the local ID.</p>
<p>A new role permission to publish to the ZMQ pub-sub channel has been added (as kindly requested by our favorite user, who regularly motivates us by sending decapitated horse heads if we slack). This role allows administrators to enable or disable ZMQ publishing per user.</p>
<p>The flash message system has been rewritten from scratch, providing a cleaner approach that relies on bootstrap’s internal flash messaging look and feel, along with 3 different levels of notifications.</p>
<p>Allow hard deleting of attributes that were never published in order to avoid the leaking of sensitive information via soft deleted attributes.</p>
<p>Two security vulnerabilities were fixed: <a href="https://cve.circl.lu/cve/CVE-2018-11245">CVE-2018-11245</a> and <a href="https://cve.circl.lu/cve/CVE-2018-11562">CVE-2018-11562</a>. Thanks to the reporters Jarek Kozluk from zbp.pl and Dawid Czarnecki. Don’t hesitate to contact us for <a href="https://github.com/MISP/MISP/blob/2.4/CONTRIBUTING.md#reporting-security-vulnerabilities">reporting vulnerabilities</a>, we love those contributions.</p>
<table>
<tbody>
<tr>
<td>The STIX 1 and STIX 2 exports and imports were migrated to Python 3 (don’t forget to update the dependencies). The STIX 1 export has been improved to include additional objects such X.509 certificate and MISP objects. The STIX 1 import has been improved for email, whois, and artifact objects along with tags via journal entries. The STIX 2 export has improved regkey object parsing, along with ip</td>
<td>port and custom object export.</td>
</tr>
</tbody>
</table>
<p>The full change log is available <a href="https://www.misp.software/Changelog.txt">here</a>. <a href="https://www.misp.software/PyMISP-Changelog.txt">PyMISP change log</a> is also available.</p>
<p>A huge thanks to all the <a href="/contributors">contributors</a> who helped us to improve the software and also all the participants in MISP training which always give intere
PyMISP has been also updated, boasting a more clever approach to timestamp handling while updating MISP JSON files. The PyMISP documentation has been updated <a href="https://media.readthedocs.org/pdf/pymisp/latest/pymisp.pdf">PDF</a>. <a href="https://github.com/MISP/misp-rfc">MISP standard Internet-Drafts</a> have been updated and published.</p>
<p>MISP <a href="/galaxy.pdf">galaxy</a>, <a href="/objects.pdf">objects</a> and <a href="/taxonomies.pdf">taxonomies</a> were notably extended by many contributors. These are also included by default in MISP. Don’t forget to do a <code class="highlighter-rouge">git submodule update</code> and update galaxies, objects and taxonomies via the UI.</p>
<p>Don’t forget that the MISP Threat Intelligence Summit 0x4 will take place the Monday 15th October 2018 before hack.lu 2018. A <a href="https://cfp.hack.lu/misp0x4/">Call-for-Papers is open</a> for the MISP Threat Intelligence Summit 0x4. We would be glad to see users, contributors or organisations actively using MISP or/and threat intelligence to share their experiences and presentation to the CfP.</p>2018-06-06T23:00:00+00:00https://www.misp-project.org/2018/06/27/MISP.2.4.93.releasedMISP - MISP 2.4.93 released (aka ATT&CK integration)2018-06-26T23:00:00+00:00<p>A new version of MISP <a href="https://github.com/MISP/MISP/tree/v2.4.93">2.4.93</a> has been released including a much improved and tightly integrated <a href="https://attack.mitre.org">MITRE ATT&CK</a> interface, a new event locking functionality, initial support for a multilingual interface, various fixes including a security fix (<a href="https://cve.circl.lu/cve/CVE-2018-12649">CVE-2018-12649</a>).</p>
<p>MITRE ATT&CK offers an excellent, efficient and very complete framework to describe adversarial tactics and techniques, which MISP now directly incorporates as a way to contextualise the information contained within (at the event and attribute levels) and to share the contextualised data with your partners. We have been supporting the use of the ATT&CK framework via the <a href="https://www.misp-project.org/galaxy.html">misp-galaxy</a> from the early beginning but we quickly realised the limitations of using this technique in MISP. So we decided to improve the user-interface by having the ATT&CK matrix directly accessible in MISP in order to be able to more intuitively attach techniques and tactics to MISP data following a method that is more universally linked to ATT&CK. The global statistics were also extended in order to get a quick overview of techniques used.</p>
<div class="myvideo">
<video style="display:block; width:100%; height:auto;" autoplay="" controls="" loop="loop">
<source src="/assets/images/misp/video/attack.webm" type="video/webm" />
</video>
</div>
<p>A new functionality has been introduced called the event lock which shows users if another user is editing the event they’re viewing (same organisation only).</p>
<p>STIX 2 export now includes PE binaries and better support for MISP objects.</p>
<p>STIX 1 import has been significantly improved in regards to its capabilities when importing AIS/US-CERT STIX files that include specific relationships for malware samples.</p>
<p>A new functionality has been added to allow the toggling of the UI language of the MISP interface (part of the ongoing <a href="https://github.com/MISP/misp-book/tree/master/translation">internationalization effort</a>) .</p>
<p><a href="https://cve.circl.lu/cve/CVE-2018-12649">CVE-2018-12649</a> has been fixed, which allowed attackers to bypass the brute force protection via PUT requests.</p>
<p>Many bug fixes (including some to the install guides) and minor features including impfuzzy validation.</p>
<p>The full change log is available <a href="https://www.misp.software/Changelog.txt">here</a>. <a href="https://www.misp.software/PyMISP-Changelog.txt">PyMISP change log</a> is also available.</p>
<p>A huge thanks to all the <a href="/contributors">contributors</a> who helped us improve the software and also all the participants in MISP trainings giving us a bunch of interesting feedback for improvements.</p>
<p>MISP <a href="/galaxy.pdf">galaxy</a>, <a href="/objects.pdf">objects</a> and <a href="/taxonomies.pdf">taxonomies</a> were notably extended by many contributors. These are also included by default in MISP. Don’t forget to do a <code class="highlighter-rouge">git submodule update</code> and update galaxies, objects and taxonomies via the UI.</p>
<p>Don’t forget that the MISP Threat Intelligence Summit 0x4 will take place the Monday 15th October 2018 before hack.lu 2018. A <a href="https://cfp.hack.lu/misp0x4/">Call-for-Papers is open</a> for the MISP Threat Intelligence Summit 0x4. We would be glad to see users, contributors or organisations actively using MISP or/and threat intelligence to share their experiences and presentation to the CfP.</p>2018-06-26T23:00:00+00:00https://www.misp-project.org/2018/08/06/MISP.2.4.94.releasedMISP - MISP 2.4.94 released (aka summer improvements)2018-08-05T23:00:00+00:00<p>A new version of MISP <a href="https://github.com/MISP/MISP/tree/v2.4.94">2.4.94</a> has been released including an improved event graph interface, a new Elasticsearch plugin, various extensions and enhancements to the API, clean-ups and many improvements. Even though it’s summertime, we continuously work on the MISP project and a lot of changes were introduced.</p>
<p>Major improvements have been implemented in the MISP event graph such as:</p>
<ul>
<li>Export functionality added in the MISP event graph to export in PNG, JPEG, JSON format and Graphviz dot format.</li>
<li>Saving functionality to save the state of an event graph. This allows a user of an organisation to keep the state of the event graph and retrieve the history.</li>
</ul>
<p><img src="/assets/images/misp/blog/save-graph.png" alt="New functionality in the MISP event graph to export the graph and save the state of the graph" class="img-responsive" /></p>
<p>The MITRE ATT&CK matrix user-interface has been extended to add directly techniques at event level without passing by the galaxy interface.</p>
<p>A new functionality contributed allows users to log all MISP activities in Elasticsearch. It’s pretty simple to configure thanks to its settings being part of the standard plugin settings system, so head over there to find the Elasticsearch configuration options.</p>
<p><img src="/assets/images/misp/blog/elasticsearch.png" alt="Configuring Elasticsearch with MISP" /></p>
<p>The CLI interface has been improved with the ability to get the API key of a given user, to force update the taxonomies, warning lists, notice lists and object templates. All of this serves to improve the automation of deployment of MISP instances without the need to use the UI.</p>
<p>MISP Synchronisation has been improved by moving the blacklist event skipping to the negotiation phase instead of first pulling blacklisted events and discard them after the fact. Synchronisation has also been improved in situations involving a large number of deletions. The pre-sync negotiation is now based on UUID-based lookups instead of relying on local IDs.</p>
<p>The MISP API has been introduced allowing users to deduce the prefered edit strategy of a given event. This has been introduced to help additional tools to decide whether to edit or extend MISP events. One such tool is TheHive project, which recently received a new release utilising the extend event functionality through this edit strategy API.</p>
<p>Various UI views have been improved to ease administration tasks for admins operating large MISP instances, including features such as listing the PGP fingerprints via the verifyGPG interface, a new statistic tab to show how many users/organisations were added over the past months/year and more.</p>
<p>Many internal changes and clean-ups were performed based on a recent static analysis of the codebase.</p>
<p>For a complete overview of all the changes, the full change log is available <a href="https://www.misp.software/Changelog.txt">here</a>. <a href="https://www.misp.software/PyMISP-Changelog.txt">PyMISP change log</a> is also available.</p>
<p>New attribute types such as Monero (xmr) added along with the soft validation. <a href="https://github.com/MISP/misp-objects/blob/master/objects/coin-address/definition.json">coin-address object template</a> updated to match the xmr attribute type.</p>
<p>Major changes in the STIX2 export and import were undertaken to improve the scope of the <a href="https://github.com/MISP/misp-rfc">MISP open standard</a> and the mapping thereof to the STIX2 JSON format.</p>
<p>A huge thanks to all the <a href="/contributors">contributors</a> who have tirelessly helped us improve the software and also all the participants in MISP trainings giving us a bunch of interesting feedback for improvements.</p>
<p>MISP <a href="/galaxy.pdf">galaxy</a>, <a href="/objects.pdf">objects</a> and <a href="/taxonomies.pdf">taxonomies</a> were notably extended by many contributors. These are also included by default in MISP. Don’t forget to do a <code class="highlighter-rouge">git submodule update</code> and update galaxies, objects and taxonomies via the UI.</p>
<p>Don’t forget that the MISP Threat Intelligence Summit 0x4 will take place the Monday 15th October 2018 before hack.lu 2018. Don’t hesitate to have a look at our <a href="http://www.misp-project.org/events/">events page</a> to see our next activities to improve threat intelligence, analytics and automation.</p>2018-08-05T23:00:00+00:00https://www.misp-project.org/2018/09/06/MISP.2.4.95.releasedMISP - MISP 2.4.95 released (aka API search improvement)2018-09-05T23:00:00+00:00<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.95">2.4.95</a>) has been released with the first stage of a complete rework and refactoring of the API exports, allowing for more flexibility, improved search capabilities, performance and extendability.</p>
<p>The search API in MISP has been refactored to streamline and simplify the code’s logic and to bring consistency among the various export formats (MISP JSON, MISP XML, OpenIOC, Suricata, Snort and the text export) especially in regards to filtering. The filter system now assumes exact string matches by default and allows users to insert wild-card characters for substring searches across all filters. This provides both performance boosts along with more accurate results when substring matching is not needed along with the flexibility of setting search terms such as starts with or endswith. The API is also backwards compatible with previous versions and existing tools (let us know if you have <a href="https://www.github/MISP/MISP">any issue</a>).</p>
<p>With the new API, building search queries has become more natural and simple to build programmatically. For example, exporting all attributes of types ip-src and ip-dst that have a TLP marking and are not marked tlp:red, can be achieved with the query below. String searches are by default exact lookups, but you can use SQL style “%” wildcards to do substring searches.</p>
<div class="highlighter-rouge"><div class="highlight"><pre class="highlight"><code>{
"returnFormat": "json",
"type": {
"OR": [
"ip-src",
"ip-dst"
]
},
"tags": {
"NOT": [
"tlp:red"
],
"OR": [
"tlp:%"
]
}
}
</code></pre></div></div>
<p>All old parameter syntaxes are still supported, though passing ordered parameters via the URL has been deprecated. We are also currently in the process of baking all existing export APIs into the standard API search functionality - simply pass your usual standardised list of parameters as described in the API and choose the return format. Make sure you query the correct scope (/events/restSearch for all events matching a query and /attributes/restSearch for all attributes matching a query).</p>
<p>A complete ReST client has been added in the MISP interface to easily query the API from your MISP. A templating system has been included to assist users to create their ReST queries against the API. The ReST client includes the API enumeration documentation based on the API exposed description. Use this tool to build and test queries that you would like to use via other tools and applications.</p>
<p>A debug functionality has been added in any API query to quickly show the SQL queries performed by appending <code class="highlighter-rouge">/sql:1</code> to any query via the API (debugging mode must be set to “debug with SQL dump” - option 2).</p>
<p>Many new <a href="https://www.github.com/MISP/misp-modules">MISP modules</a> were included and we extend MISP to better support enrichment modules with large output (such as the Sigma to search queries converter). In this version, a new on-demand pop-up has been introduced to have a sticky hover to ease cut-and-paste or selection.</p>
<p><img src="/assets/images/misp/blog/sigma.png" alt="A sigma export to SIEM rules via the misp-modules export" class="img-responsive" /></p>
<p>A bro NIDS type has been added in MISP to support the exchange of raw bro NIDS signature within MISP communities.</p>
<p>For a complete overview of all the changes, the full change log is available <a href="https://www.misp.software/Changelog.txt">here</a>. <a href="https://www.misp.software/PyMISP-Changelog.txt">PyMISP change log</a> is also available.</p>
<p>Enhancements to the STIX2 export and import were undertaken to improve the scope coverage of the <a href="https://github.com/MISP/misp-rfc">MISP open standard</a> and the mapping thereof to the STIX2 JSON format. Relationships between SDOs have been improved in the export to map the MISP relationships with the fixed relationships described in STIX2. valid_until has been mapped in the STIX2 export based on the expiration date used in the expiration sightings available in MISP.</p>
<p>Several new translations were included in MISP for the user-interface localisation. The Japanese translation has been completed, French, Danish and Italian have been improved drastically and many other translations (such as German, Spanish and Korean) are on the way.</p>
<p>A huge thanks to all the <a href="/contributors">contributors</a> who have tirelessly helped us improve the software and also all the participants in the MISP trainings giving us a bunch of interesting feedback for ideas for improvements.</p>
<p>MISP <a href="/galaxy.pdf">galaxy</a>, <a href="/objects.pdf">objects</a> and <a href="/taxonomies.pdf">taxonomies</a> were notably extended by many contributors. These are also included by default in MISP. Don’t forget to do a <code class="highlighter-rouge">git submodule update</code> and update galaxies, objects and taxonomies via the UI.</p>
<p>Don’t forget that the MISP Threat Intelligence Summit 0x4 will take place the Monday 15th October 2018 before hack.lu 2018. Don’t hesitate to have a look at our <a href="http://www.misp-project.org/events/">events page</a> to see our next activities to improve threat intelligence, analytics and automation.</p>2018-09-05T23:00:00+00:00https://www.misp-project.org/2018/10/09/MISP.2.4.96.releasedMISP - MISP 2.4.96 released (aka API everywhere release)2018-10-08T23:00:00+00:00<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.96">2.4.96</a>) has been released with a complete rework, refactoring and simplification of the restSearch API, allowing for more flexibility, improved search capabilities, performance and extendability.</p>
<p>All of the MISP export APIs have now been unified into the restSearch APIs with a vastly improved query format. The complete documentation of the restSearch is included in the automation page.</p>
<p>A pagination system has been added allowing users to easily paginate over search result sets and limit the output. The two new parameters are limit and page, both directly accessible in the MISP query format.</p>
<p>The search results in the MISP UI now allows for the direct download of the search results in any of the supported formats available in MISP in a convenient and quick way.</p>
<p>The CSV export has been refined to remove inconsistencies in the requested field parameters and the header field names among other fixes.</p>
<p>The internal fetcher has been rewritten to use an internal pagination and caching mechanism that scales with the amount of memory given to the PHP process, increasing performance and reducing the chance of ever running into memory limit issues. Various other changes (such as resolving some bottlenecks in regards to object references, potential query length issues in certain situations, etc) improve both the stability and performance of all functions relying on fetching event / attribute data.</p>
<p>The freetext import is now delegated to a background process for large imports. It has also received additional tweaks such as support for ASN detection and additional indicator refanging rules.</p>
<p>The API for warning-lists has been improved and can now be updated by using a substring contained within a warninglist’s name. A simple toggle function mechanism to disable and enable warning-lists via the API has also been added.</p>
<p>The <a href="https://blog.thehive-project.org/2018/09/27/cortex-2-1-0-the-response-edition/">cortex integration is now back</a> to nominal and fully functional with this latest version.</p>
<p>A host of additional improvements and bugs fixed were introduced including improvements to the user-interface, API, STIX 1/2 import and export, etc.</p>
<p>A huge thanks to all the <a href="/contributors">contributors</a> who have tirelessly helped us improve the software and also all the participants in the MISP trainings giving us a bunch of interesting feedback for ideas for improvements.</p>
<p>MISP <a href="/galaxy.pdf">galaxy</a>, <a href="/objects.pdf">objects</a> and <a href="/taxonomies.pdf">taxonomies</a> were notably extended by many contributors. These are also included by default in MISP. Don’t forget to do a <code class="highlighter-rouge">git submodule update</code> and update galaxies, objects and taxonomies via the UI.</p>
<p>Don’t forget that the MISP Threat Intelligence Summit 0x4 will take place the Monday 15th October 2018 before hack.lu 2018. Don’t hesitate to have a look at our <a href="http://www.misp-project.org/events/">events page</a> to see our next activities to improve threat intelligence, analytics and automation. We have also two MISP trainings foreseen in Luxembourg Monday 17th December <a href="https://en.xing-events.com/MURFIIQ">MISP Training - Threat Intelligence Analyst and Administrators</a> and Tuesday 18th December <a href="https://en.xing-events.com/QDBMTBT.html">MISP Training - Developers session - API and Extensions </a>.</p>2018-10-08T23:00:00+00:00https://www.misp-project.org/2018/10/30/MISP.2.4.97.releasedMISP - MISP 2.4.97 released (aka so many new features)2018-10-29T23:00:00+00:00<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.97">2.4.97</a>) has been released with new features such as related tags, the sighting restSearch API, a new French localisation along with many improvements to the API and he import/export capabilities, such as improved support for <a href="https://www.us-cert.gov/ais">DHS AIS</a> STIX 1 files.</p>
<p><img src="https://www.misp-project.org/assets/images/misp/blog/eventgraph.png" alt="MISP event graph to display an overview of the relationships for a malware infection" /></p>
<p>The new related tags functionality has been introduced to allow users to view the most commonly used tags for a specific attribute across all events. This can help analysts when deciding to use a specific classification based on previous analyses to reduce the time it takes to contextualise the new information.</p>
<p><img src="https://www.misp-project.org/assets/images/misp/blog/related-tags.png" alt="MISP event graph to display an overview of the relationships for a malware infection" /></p>
<p>A new API has been introduced, allowing users to search <a href="https://www.misp.software/2017/02/16/Sighting-The-Next-Level.html">MISP sightings</a> using a set of filter parameters along with a list of data formats (JSON, CSV or XML). The search is available on an event, attribute or instance level. You can easily search by time ranges (from, to or last) using the standard restSearch API syntax.</p>
<p>At the API level, many changes were introduced such as:</p>
<ul>
<li><a href="https://www.misp-project.org/galaxy.html">Galaxy</a> API is now exposed and can be browsed via the API.</li>
<li>Event index API can now be exported in CSV format in addition to standard JSON format.</li>
<li>Log entries are now exposed via the API. The API is documented via the template system/REST client.</li>
<li>The Warning-list lookups are now exposed to the API. A value can be quickly tested against the warning-lists enabled on a MISP instance without the need to create any persistent data.</li>
</ul>
<p>Many fixes were introduced to the STIX 1 and 2 import and export including a better support of AIS markings and specific MISP objects.</p>
<p>The French localisation of the user-interface is now complete (thanks to all the contributors). French is now the second localisation after Japanese to reach full coverage. If you want to contribute and help with the translation project, don’t hesitate to <a href="https://crowdin.com/project/misp">join us on crowdin</a>.</p>
<p>MISP <a href="/galaxy.pdf">galaxy</a>, <a href="/objects.pdf">objects</a> and <a href="/taxonomies.pdf">taxonomies</a> were notably extended by many contributors. New object templates were introduced to better support the description of forensic analysis cases and improve their sharing. These are also included by default in MISP. Don’t forget to do a <code class="highlighter-rouge">git submodule update</code> and update galaxies, objects and taxonomies via the UI.</p>
<p>A detailed and <a href="http://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>
<p>Don’t hesitate to have a look at our <a href="http://www.misp-project.org/events/">events page</a> to see our next activities to improve threat intelligence, analytics and automation. We have also two MISP trainings foreseen in Luxembourg Monday 17th December <a href="https://en.xing-events.com/MURFIIQ">MISP Training - Threat Intelligence Analyst and Administrators</a> and Tuesday 18th December <a href="https://en.xing-events.com/QDBMTBT.html">MISP Training - Developers session - API and Extensions </a>.</p>2018-10-29T23:00:00+00:00https://www.misp-project.org/2018/11/26/MISP.2.4.98.releasedMISP - MISP 2.4.98 released (aka usability improvements and SleuthKit mactime import)2018-11-25T23:00:00+00:00<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.98">2.4.98</a>) has been released with new features such as improved UI consistency (such as attributes search output), improved validation error messages, a new built-in experimental SleuthKit mactime import, new small features and many bugs fixed.</p>
<p>The user interface has been significantly improved in regards to the reporting of validation errors occuring whilst attempting to save attributes. The user can now view the attributes not properly imported and the
reason for the validation failing. A user can view the failed/succeeded saves resulting from batch imports via the UI. Additionally a host of small fixes for the flash message system have been implemented.</p>
<p>The output of the search interface is now consistent with standard attributes view in MISP. The user can now add sighting, tags, galaxies directly in the search results.</p>
<p>A new experimental import functionality has been included to import SleuthKit mactime timelines from MISP directly. The user can import one or more mactime timelines in MISP, which will be included as a mactime object to describe forensic activities on an analysed file system. The import is a two-step process where the user can cherry pick the forensic events which took place and select the meaningful activity to be added in a MISP event.</p>
<p><img src="https://www.misp-project.org/assets/images/misp/blog/mactime1.png" alt="SleuthKit mactime import in MISP" />
<img src="https://www.misp-project.org/assets/images/misp/blog/mactime2.png" alt="SleuthKit mactime imported in MISP as objects" /></p>
<p>The API has been improved with many new features such as:</p>
<ul>
<li>The result counts to restsearch API are now visible via the x-result-count header</li>
<li>The option includeProposals is now functional at attribute level restSearch</li>
<li>The event controller readability has been improved</li>
<li>Fixed a bug blocking malware samples from being added using /events/add when the encrypt=1 flag was set for raw sample inclusion</li>
<li>Sighting restSearch API documentation has been fixed</li>
<li>Better handling when trying to edit an attribute without adequate permissions</li>
<li>Throw a proper error when trying to edit an event without access to doing so</li>
<li>Fixed non exportable tags being included in the attribute level restSearch.</li>
</ul>
<p>In the CSV export functionality, the ignore flag is restored to the old behaviour:</p>
<ul>
<li>If not set, only return published events / to_ids flagged events by default</li>
<li>Setting ignore:0 will result in the default behaviour</li>
<li>Setting ignore:1 will result in unpublished events and non to_ids attributes being filtered out</li>
<li>Fixed a bug that broke the CSV api if ignore:0 was passed</li>
</ul>
<p>Many long-standing bugs were fixed based on the feedback from various users and organisations.</p>
<p>In STIX 1 import, AIS marking is now included in import as MISP event tag. Many improvement in STIX 1 and STIX 2 import/export, check the changelog for the complete changes.</p>
<p>MISP <a href="/galaxy.pdf">galaxy</a>, <a href="/objects.pdf">objects</a> and <a href="/taxonomies.pdf">taxonomies</a> were notably extended by many contributors. New object templates were introduced to improve the support for the description of forensic analysis cases and improve their sharing. These are also included by default in MISP. Don’t forget to do a <code class="highlighter-rouge">git submodule update</code> and update galaxies, objects and taxonomies via the UI.</p>
<p>A detailed and <a href="http://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>
<p>Don’t hesitate to have a look at our <a href="http://www.misp-project.org/events/">events page</a> to see our next activities to improve threat intelligence, analytics and automation.</p>2018-11-25T23:00:00+00:00https://www.misp-project.org/2018/12/06/MISP.2.4.99.releasedMISP - MISP 2.4.99 released (aka API/UI fixes and critical security vulnerability fixed)2018-12-05T23:00:00+00:00<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.99">2.4.99</a>) has been released with improvements in the UI, API, STIX import and a fixed critical security vulnerability.</p>
<p>Thanks to Francois-Xavier Stellamans from NCI Agency Cyber Security who reported a critical vulnerability in the STIX 1 import code. The vulnerability allows a malicious authenticated user to inject commands via an incorrectly escaped variable name (the original name of the STIX file). We strongly urge users to update their MISP instance to the latest version. We also replaced the mechanism of storing the original uploaded files on ingestion with a standardised function that will process the files without passing them to external tools - this reusable system will avoid any similar issues in the future if new similar mechanisms are introduced. <a href="https://cve.circl.lu/cve/CVE-2018-19908">CVE-2018-19908</a></p>
<p>This release includes the following changes:</p>
<ul>
<li>The following attribute types were added x509-fingerprint-md5 and x509 -fingerprint-sha256 to the network activity category.</li>
<li>A new CLI interface to cleanup the brute-force protection entries from MISP.</li>
<li>Some warning messages inconsistencies were fixed in the UI.</li>
<li>Added a warning when a site administrator is trying to edit an event not belonging to the organisation of the site admin.</li>
<li>[API] Object edit has been fixed to return the object in the correct format.</li>
<li>When editing an object to add new attributes, correctly set the default distribution if nothing is set.</li>
<li>Many fixes and improvement in the STIX 1 and STIX 2.0 import.</li>
<li>XML MISP export has been fixed.</li>
</ul>
<p>We would like to thank all the contributors, reporters and users who helped us in the past days to improve MISP.</p>
<p>MISP <a href="/galaxy.pdf">galaxy</a>, <a href="/objects.pdf">objects</a> and <a href="/taxonomies.pdf">taxonomies</a> were extended by many contributors. These are also included by default in MISP. Don’t forget to do a <code class="highlighter-rouge">git submodule update</code> and update galaxies, objects and taxonomies via the UI.</p>
<p>A detailed and <a href="http://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>
<p>Don’t hesitate to have a look at our <a href="http://www.misp-project.org/events/">events page</a> to see our next activities to improve threat intelligence, analytics and automation.</p>2018-12-05T23:00:00+00:00https://www.misp-project.org/2019/01/01/MISP.2.4.100.releasedMISP - MISP 2.4.100 released (aka happy new year release)2018-12-31T23:00:00+00:00<p>Happy new year! We are so proud of our community which has supported us for the past year and we hope to do even better for 2019. Thanks a lot.</p>
<p>A new version of MISP (<a href="https://github.com/MISP/MISP/tree/v2.4.100">2.4.100</a>) has been released with improvements to the UI, API, import and export along with the addition of a new query builder.</p>
<p><img src="/assets/images/misp/blog/restsearchbuilder.png" alt="" /></p>
<p>Considering the criticality of being able to accurately define how we query MISP instances in order to feed and integrate with network security devices, endpoint security devices or monitoring tools, we have tried to improve the life of the users tasked with the above duties via a new query builder, available through the REST client interface (REST client below the Event Actions). The query builder provides a simple interface to create your JSON queries used to get
the information you truly are interested in back for ingestion in your devices and tools easily.</p>
<p>Instead of going through the sometimes headache inducing task of trying to manually craft JSON objects, you can now construct complex queries via a series of simple clicks. The query builder is intelligent in a sense that it attempts to provide the exact values that are supported as options and provide you with dynamic contextual information for each of the query filters. You can subsequently test your queries and grab the code generated based on your filter choices in Python or curl format to support your integration.</p>
<p>UI usability has been improved with the following fixes (based on various feedbacks during the MISP trainings):</p>
<ul>
<li>Quickedit (double-click on value) on the event view has been replaced by a more obvious edit icon to ease cutting and pasting values the attribute list. This change has also made for the category, type and IDS fields.</li>
<li>Hover functionality has been improved to avoid glitchy popovers and a scrollbar was added along with multiple bugs that were fixed.</li>
<li>Clarification of the old hide tag functionality to clarify it’s intended effect (being a non-selectable tag via the interface for the given instance).</li>
</ul>
<p>Two new attribute types were introduced in MISP (thanks to the contributors):</p>
<ul>
<li>cdhash - Code Signing which is the canonical hash of the program’s CodeDirectory resource on Apple OS ref:<a href="https://developer.apple.com/library/archive/documentation/Security/Conceptual/CodeSigningGuide/RequirementLang/RequirementLang.html">Code Signing Guide</a>. Thanks to <a href="https://github.com/droe">Daniel Roethlisberger</a> for the contribution.</li>
<li>ja3-fingerprint-md5 - is a hash for creating SSL client fingerprints in an easy to produce and shareable way. A tool to extract ja3 from pcap and generate ja3 object in MISP called <a href="https://github.com/eCrimeLabs/ja3toMISP">ja3toMISP</a> has been developed by <a href="https://www.ecrimelabs.com/blog/2018/12/30/ja3-to-misp-tool-released">eCrimelabs</a>.</li>
</ul>
<p>The types are also part of <a href="https://tools.ietf.org/html/draft-dulaunoy-misp-core-format-06">MISP standard core format which has been updated</a>. If you see a missing types or object template in MISP, don’t hesitate to report it back to us.</p>
<p>Multiple bugs were fixed, such as a synchronisation bug causing certain events not getting synced via a pull due to an overzealous protection mechanism.</p>
<p>MISP submodule for STIX 2.x now relies on our <a href="https://github.com/MISP/cti-python-stix2">fork of the STIX 2 library</a> to support import STIX 2.x files (which time-based UUIDs) produced by some vendors and tools. If you have any issue while updating the submodule, don’t forget to run a <code class="highlighter-rouge">git submodule sync</code> before running a <code class="highlighter-rouge">git submodule update</code> on existing MISP instances. STIX 1 and 2 import/export has been significantly improved based on the numerous sample files received. If you have specific issues with certain STIX files, feel free to send these to us.</p>
<p>We would like to thank all the contributors, reporters and users who helped us in the past months to improve MISP and information sharing at large.</p>
<p>MISP <a href="/galaxy.pdf">galaxy</a>, <a href="/objects.pdf">objects</a> and <a href="/taxonomies.pdf">taxonomies</a> were extended by many contributors. These are also included by default in MISP. Don’t forget to do a <code class="highlighter-rouge">git submodule update</code> and update galaxies, objects and taxonomies via the UI.</p>
<p>A detailed and <a href="http://www.misp-project.org/Changelog.txt">complete changelog is available</a> with all the fixes, changes and improvements.</p>
<p>We also released the <a href="https://github.com/MISP/misp-training">complete source code of the MISP training materials</a> and we hope to see many improvements such as translation, new materials or ideas from the training materials.</p>
<p>Don’t hesitate to have a look at our <a href="http://www.misp-project.org/events/">events page</a> to see our next activities to improve threat intelligence, analytics and automation.</p>2018-12-31T23:00:00+00:00